Vulnerabilities Opportunities
Vulnerabilities are indeed opportunities for information security professional regardless whether you are a good or a bad guy. If you are a hacker then this is your golden ticket to fulfill your dreams of hacking glory, and if you are a system or network admin then these are the holes that you need to cover. For SysAdmins (at least the good ones), vulnerabilities means…”finally some serious work”…at least better than resetting passwords for idiotic users “also known as top management” who keep forgetting the CAPS Lock on after 6 attempts. The question is……how to find vulnerabilities?
Professional hackers follow a process (called Triage) to collect information about their target. The information will help them identify and answer questions like:
• What Operating systems are they using?
• What is the target patch level?
• What vendors are they using (Cisco, Linksys, Microsoft…etc.)?
• Do they have a surveillance camera online that can give me a peek inside the company?
• Do they have any printers accessible from the Internet?
And ultimately and after long days of search they will know the exact vulnerability they should be targeting.
Having said that, I never thought that a day would come where a hacker or just a curious professional can have an entire search engine doing this for him. Then about 2 years ago I meet Shodan: www.shodanhq.com
Shodan is an online computer search engine that lets you find servers/ routers/ printers/ surveillance cameras…etc. by using simple search keywords like (Ports, Services, vendors, country names…etc.).
Typing the search keywords: cisco country: eg returned for me 1409 IPs for Cisco devices accessible from the internet in Egypt. Why not spend some time trying the default user names and passwords and see what you can get. You will be surprised. Typing FTP country: eg returned 9373 FTP servers in Egypt, I managed to access some of them just by trying the guest credentials. That left me depressed for days.
In those 9373 FTP servers, some of those companies even provide the exact version of the FTP server they are using which only makes it easier for the bad guy to look for the vulnerabilities available in this particular version. It’s really that easy. In the above example, “Egypt Air” our national carrier disclosed that they have a CISCO device
(IP: 217.139.100.1), with the FTP server enabled and publicly published online and its version (1.00), and this obsolete version has known vulnerabilities. This FTP server can be either insignificant or of great value.
“Alico Egypt”, the insurance company apparently has a Microsoft FTP server accessible online that doesn’t accept anonymous accounts, which is a good security practice. To take it up a notch, how about a query that can get you all the IIS servers (Web servers) in Egypt that are still using IIS 6.0 for example: Typing: IIS 6.0 -404 -403 -302 country: eg returned 2443 web servers in Egypt still using Microsoft IIS 6.0 with its known vulnerabilities, at east 8 ministerial/government websites are on the list.
Ever wondered who in Egypt is still using IIS 5.0 just ask Shodan. Typing IIS 5.0 -404 -403 -302 country: eg returned 526 web servers including the website of the American University in Egypt, so the AUC is still using IIS 5.0 that originally was released with Windows 2000 (around 12 years ago). They can definitely do better than that. Another IIS 5.0 worthy note was an exchange securities trading company called Optima (http://41.205.125.68/), the vulnerable website host important clients information. Who is monitoring the private information protection in Egypt?
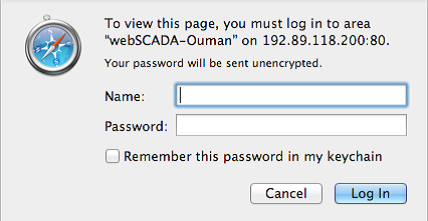
But to be fair this is a global problem, even looking for SCADA keywords returned more than 59 SCADA services available online…for example this particular webSCADA in Finland owned by a tractor manufacturing company just asks you about your (username/password) and you are in, how immune is this against brute force attacks…only the experiment can tell.
Looking to cause an empty tray of papers somewhere, how about looking for HP print servers with anonymous FTP access: searching for 230-Hewlett- Packard retrieved more than 350 print servers available online that you can try and access. If you are just looking for fun, try searching for PelcoNet- Web server, which is the default streaming server for Pelco surveillance cameras, the world’s best CCTV cameras. And you can see what your target company security officer is watching live. I believe this can be useful if you are planning on robbing a bank……you didn’t hear that from us.
About The Author
Omar Sherin, Mr. Omar Sherin is the head of critical information infrastructure protection (CIIP) at Qatar Computer Emergency Response Team (Q-CERT), an ictQATAR initiative. In this role he participates in technically assessing critical infrastructure, drafting guidelines such as the Qatari National ICS Security Standard, and conducting Qatar’s national cybersecurity drills. He is also an international partner of the Industrial Control Systems Joint Working Group (ICSJWC) and a certified business continuity professional, certified ethical hacker, and ISO 27001 lead auditor. He has more than 11 years of professional experience in information security and resiliency, and has worked for several multinational firms in the oil and gas sector.