Rootkits: A Deeper Look
1. What is rootkit?
The rootkit is simply a programme that gives you a permanent access to the “root”, which is the highest privileged user in UNIX system. The rootkit can easily control the system or modify it on the fly to force it to hide the presence of a specific virus or spyware.
2. Why rootkits?
It gives you a permanent access to the infected machine. For as much as hackers’ belief, it is not only enough to penetrate a system or compromise its security defenses, but also the ability to stay hidden in the system to spy or control it for your desired needs is a must. Therefore, rootkits are mainly created to hide the hacker inside the system from administrators, file monitors and firewalls. Some of the hiding techniques are hiding files in the hard disk, a connection port, some registry keys or a running process in the machine.
Furthermore, some other rootkits are especially created for other needs, like keystroke monitor (keyboard spy), or packet sniffer, which is a program that monitors all the data that is sent or received in the computer in order to steal passwords or credit cards.
3. Some Definitions:
1. User-mode Vs. Kernel-mode:
The computer processor has some type of security called rings. Rings are simply a set of privileges or restrictions, which enable hackers to work on them. There are four rings and they begin with ring-0, which is the highest privilege and it is called kernel-mode. Ring-3, that is, the lowest privilege and is called usermode.
All applications run in user-mode and have specific privileges which they, by all means, cannot exceed. When the operating system runs in the kernelmode, which has the highest privilege, it can do everything ranging from modifying the memory of the system, modifying the setting of the processor, to sending and receiving signals from computer devices.
There is a single way to jump from ring-3 to ring-0, which is done by a processor instruction named “Sysenter” – System
Enter, to call a specific function in the operating system.
2. Patching and Hooking:
Hooking is a term given to the process of intercepting or interrupting a call to a system function like zwQueryDirectory File. Some examples are query files, which either function as modifiers to the input (the path to a certain folder whose files need to be queried), or modifiers to the output (deleting the name of a specific file in order to hide it).
Patching, in like manner, is very similar to hooking. Patching means modifying; modifying the first instructions of a specific function to hook the inputs or the outputs of this function.
4. Types of Rootkits:
1. User-mode Rootkits:
This type of rootkits is simply working in the user mode and it hooks some functions in a specific process, sometimes it loops on all processes except the system processes. It is done by injecting a code inside the virtual memory of this process, and then it patches the first instructions of the hooked function to force it to call the injected code.
Hence, the injected code modifies the input of this function, and then resumes the hooked function to modify the output of the very same function, and at last returns again to the process.
2. Kernel-mode Rootkits:
On the other hand, kernel-mode, the second type of rootkits, works inside the system. These rootkits are installed as device drivers and they have the ability to modify the system functions or hook I/O request packets (IRPs), which are sent to the device drivers for the purpose of modifying the inputs and outputs to this device driver.
Kernel-mode rootkits can hook all processes, including system processes at once; however, they are harder to detect and remove. The problems of kernel-mode are mainly due to it being hard to program and very sensitive to the changes of the operating system, and sometimes sensitive to the changes of devices too.
5. How Rootkits Work?
First of all, how Windows works should be understood. Windows is an operating system created to become a layer between the hardware devices and the software applications and users.
It is created to be non-sensitive of the hardware changes, to support multiple users and processes (applications), and to support system security from malformed processes and from users to users.
It supports a static interface between applications and hardware devices called Application Programming Interface (API). This interface includes many functions that do everything like managing files and directories, internet, connectivity and so on.
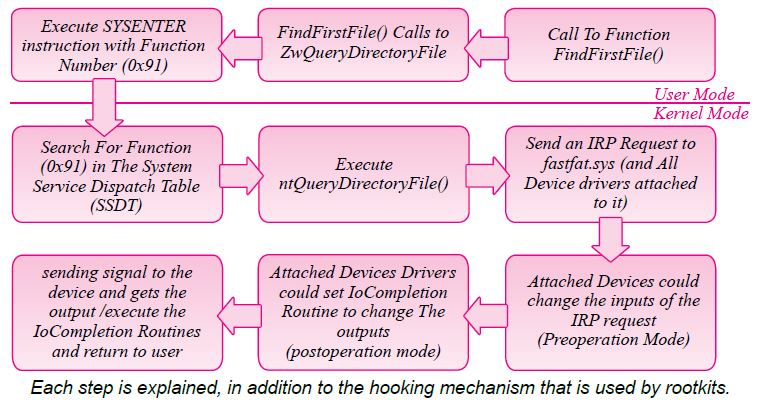
In order to understand the tricks of the rootkits, the way the interface works should be first understood. Thus, the life cycle of executing an API like “FindFirstFileA()” from user-mode to kernel-mode, to the device itself is shown below in this figure.
1.User-Mode Part:
At the user-mode, the applications have the ability to call a function of hundreds of functions in the Windows’ interface (APIs), and as it is seen in the last example, the application calls to FindFirstFileA(), which calls to another API named ZwQueryDirectoryFile(), which calls to KiFastSystemCall(), which executes a processor instruction “Sysenter” that converts you from user-mode to kernelmode and executes another function in the system in the kernel-mode named KiSystemService()
At this part, the user-mode rootkits, as previously explained, have the ability to hook one of these functions by patching its first instructions by another which allows the rootkit to change the inputs or the outputs of these functions.
2. SSDT:
While executing “Sysenter” instructions, the processor converts you into the kernel-mode (ring-0), and executes KiSystemService() function which search in an array named “System Service Dispatch Table (SSDT)” with the function number as an index in the array and gets a pointer to another function (for the last example NtQueryDirectoryFile()) and then calls to this function and the execution in the kernelmode continues.
At this part, the kernel-mode rootkits, as explained above, have the ability to change the pointer to a function in the SSDT array with another function inside the kernel-mode rootkit. Additionally, other rootkits prefer to hook these functions by patching its first instructions like the usermode rootkits.
3. Device Drivers:
After executing ntQueryDirectoryFile() function, this function sends to the related device driver a request named “I/O Request Packet (IRP)” to query on a specific directory. This packet will be received by the appreciate device driver and all device drivers attached to it. Windows allows device drivers to be attached to any device driver to filter its input, change its output or complete the request without the need of the real device driver itself. These device driver filters have the ability to change the inputs, as the IRPs were first received, and have the ability to set a function named “IOCompletionRoutine”.
The IoCompletionRoutine is executed after completing the request and before returning to user or the user-mode application. IoCompletionRoutine has the ability to change the outputs of this request in order to hide files, for example, or make any other changes. In a like manner, the rootkits have the ability to filter the inputs and the outputs of any request.
Regarding the last example, the rootkit could change the results of this query to hide a file or change its name in the results of QueryDirectory IRP.
4. Communicating With Devices:
After the device driver gets the IRP, the device driver communicates with the related device, the Hard Desk for instance, by sending signals to this device or receiving signals from it. After getting the reply from the device, the device driver changes the output to the standard shape for windows or converts the output into a more higher level and then returns to the user-mode application after calling to IoCompletionRoutine. In this stage, the rootkits cannot hook the signals to the devices, but some rootkits with another tasks, such as Key Loggers or Packet Sniffers, could communicate to the device directly to receive the pressed keys or send an internet packet by passing with this way and software filters or any hooker.
This part is very sensitive to the changes of the hardware, which is a very hard task to work on, and actually it is only used by the elite hackers as most people say.
Conclusion:
The rootkit is considered a programme or a tool that gives the root privileges to be used for the purpose of hiding the presence of a specific virus or spyware. This tool uses the hooking mechanism to filter the inputs or outputs of the system functions, either in a user-mode or kernelmode, to hide the malware process. By the same token, it can hide files from the outputs of any query as if there is no malware in the computer.
Some other rootkits use these privileges to log the key presses or sniff the internet packets to steal passwords or intrude on someone’s privates. It is also described above in this article the life system cycle to execute a system query from the usermode to the kernelmode to the hardware devices to reply to someone’s request in a high level reply with the transparency of the hardware changes.
References:
1. Addison Wesley Professional Rootkits – Subverting the Windows Kernel
2. The Rootkit Arsenal : Escape and Evasion in the Dark Corners of the System, by Reverend Bill Blunden
3. Rootkit – Wikipedia, the free encyclopedia, at this link: http://en.wikipedia.org/wiki/Rootkit
About The author
Amr Thabet
Malware Researcher at Symantec and Author of Pokas x86 Emulator and Security Research and Development Framework