A Portable Penetration Testing Kit
Utilization of hardware in hacking nowadays is eminent in various fields. It adds a new power of mobility and exposure to unknown implementations of various attacks. For a long time, hardware hacking was restricted to engineers understanding the hardware they are working on, so they can modify it to expand its usage in an abnormal way. Nowadays there are many kits sold off the shelf that enable programmers with limited knowledge of hardware to make their own projects by adding parts to the kit and composing their system and programming it using python, c# or any high level language, without direct knowledge of the underlying hardware.
When You talk to people about hardware hacking , you’ll hear some keywords based on their perspective, like the hardware keylogger ( a dongle that’s attached to the ps2/usb keyboard cable to store keystrokes ), hacking PlayStation, overclocking, bitcoining machine , emulated hardware dongles ( for software that requires a dongle as a serial verification ), signal jammers and many more
have enough knowledge in the field of electronics and of course circuits, usually electronics engineers have these abilities, but it`s a skill that gets matured
with experience. Though you can make a hardware keylogger in raspberry pi which will have dimensions about 85.60 mm × 53.98 mm, a skillful hardware engineer can make it in a dimension of 4 cm * 1 cm, if he uses a PCB (Printer Circuit Board), a microcontroller and others. Of course the size can be reduced greatly to an average of 1 cm* 1 cm if surface mounted components (small sized components that are hard soldered at home, usually done at a factory) are used.
In this topic we`ll be discussing one of the projects I made using raspberry pi as a mobile (moveable) penetration testing device. This introduces the idea of down scaling projects to fit into a spying-behavior type and non-engineers will find it easy while expanding their vision of programming. Raspberry pi [1] is a single board computer with a size nearly matching a wallet. You can check it`s full specs from various online sources and it`s shipped to nearly everywhere. The info you need to know is that it runs on a 700 Mhz ARM processor that can be overclocked to reach 1 GHz, it has 2 models, model B rev 2 features 512 MByte of memory and can run Linux/Unix Oses capable of working on ARM arch from an attached SDCARD .
Special penetration testing distro’s were made available to this platform like pwnpi, kali and rasberry pwn . It can run Rasbian, Fedora, Arch Linux, NETBSD and others. It’s worth mentioning that the kit has 2 usb slots, RJ45 socket, HDMI, miniusb for power input , analog audio output and an RCA for connection with old TV’s.
It also includes GPIO pins to iinterface with external hardware, all of that for $35. Let the hacking begin! The idea of the project came to me from the concept of Wardriving (identifying the state of Wifi access points across a region and pinpointing them on a map). Wardriving has special hardware requirements but can be done using a laptop with a good wireless NIC.
You can implement it on raspberry pi by attaching an external Wifi dongle with a high gain antenna and a good power supply. Put it in your bag and just keep walking and map the entire area, which I plan on doing soon. So instead of just logging the state of public Wifi`s, why not make a platform that`s capable of performing automatic penetration testing on connected devices and producing a report. Of course you shouldn`t violate privacy laws and go rogue on people`s networks without permission, this is a POC, you can face serious charges if you attempt to try this on the public in general.
This project was created so that you can perform automated penetration tests, either by connecting to DSL cable or simply by wireless means using the attached wireless NIC on raspberry pi. Some control was needed over the device. To keep it totally hidden and away from any suspicion you can use your mobile phone to control raspberry pi using Bluetooth, you`ll have to add a Bluetooth dongle to the kit.
You have plenty of other options for connectivity as you can attach an LCD and buttons or RF transmitter and receiver but you’ll have to get an arduiino kit to interface with the android mobile , which is a hassle, so let’s keep it simple.
For a use case scenario, let’s imagine you have the device in your backpack and you’re walking in the street or in a target entity, it detects an open access point, then it tries to get associated , or tries to bruteforce the access point credentials using a dictionary list . once it gets associated with it scans for hosts using a simple Nmap scan to discover online hosts and their OS and then sends the data to your mobile where an application is installed and paired with Bluetooth attached to the device.
When you open the mobile application you`ll find the list of the online ip’s and their OS. Through the application , you can command raspberry pi to find more info, try to
autopwn the target or do a custom scan. There are not many issues in trying to get associated to a network or do a simple Nmap scan and parse the result and send it over Bluetooth, but it`s a bit challenging when you`re trying to autopwn.
I`m using Metasploit framework v4 and the old autopwn (db_autopwn.rb) which is not available now as it was found to follow bad methodology of profiling exploits ready to be launched. I used the Metasploit API which integrates with python`s msfrpc module in order to list the exploit information and apply the necessary filters, launch the exploits at the target, then listen for any connections and report them. Now as you see it`s more about programming and less about hardware, which enables many skillful hackers to abuse the exposure of the mobility to a terrifying extent. Though don`t forget that the speed will definitely vary as you’re using far less resources than that available by a pc or a laptop.
Now for the network SSID sniffing, there`s a simple 10 line code at Securitytube[2] That scans for SSIDs
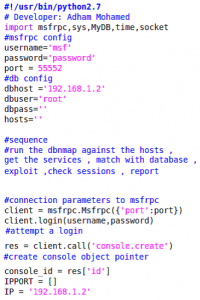
With a slight modification you can try associating to each and trying the passwords. at this point you have made an advanced passive wardriving scanner. After you get associated , you will run a simple Nmap scan and parse the results to get the online pc’s with their OS info. After getting a request from the mobile phone to start autopwning the target, an exploit search starts depending on the scan results of Nmap and compared with the exploit database created from Metasploit earlier. Python will use the msfrpc[3] to communicate with Metasploit. Here is a sample code screenshot of the msf api connection
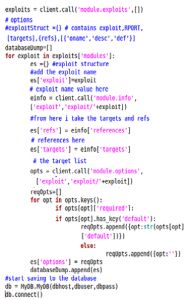
In case you`re asking about the exploit database, I used python with MSF api to list all available exploits and their non-optional parameters in a MySQL database. This phase is launched after an update is ran against Metasploit to update exploit information. Here is a snapshot that copies all the Metasploit exploit information into a python array of exploit structures.
The exploits are launched with a payload of reverse shell connection and the final results are saved to an html file indicating vulnerable hosts and a simple log
is sent to the mobile. I don`t have enough space to talk about the mobile part but maybe I’ll fuse it in future topics. It`s useful to note that this entire project can be totally automated and needs no human intervention as it will simply try to exploit any reachable device and log information.
Hardware usage in hacking is limitless and the applications are endless. We`ll try to keep you updated with more projects in coming issues.
References
[1] Raspberry pi official site – http://www.raspberrypi. org/
[2] http://hackoftheday.securitytube.net/2013/03/ wi-fi-sniffer-in-10-lines-of-python.html
[3] http://blog.spiderlabs.com/2012/01/scriptingmetasploit-
using-msgrpc-.html
About The Author

Adham Mohamed, Information Security Researcher