CAM Table Overflow Attack & how to prevent it
CAM Table Overflow Attack & how to prevent it
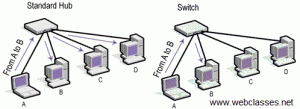
Before we start there is a basic concept in the network field which is “Switch VS Hub”. The main difference is how the packets are transmitted from one device “Source” (A) to another “Destination” (B).
Hubs always perform frame flooding by sending a received packet from source (A) to all connected devices. Normally all devices will drop the received packet except the destination (B). Switches on the other hand have a table called Content addressable memory (CAM) which refers to a dynamic table that maps MAC addresses of the connected devices to the ports on the Switch. When the packet is sent from A to B the switch will search its CAM table for the port that corresponds to the MAC address of B and will only send the packet to B, which is more secure than the Hub flooding technique.
BUT the question is what if this CAM table is full? In this article we will see how to perform an attack to test the security of our own virtual network and we will also learn how to secure it.
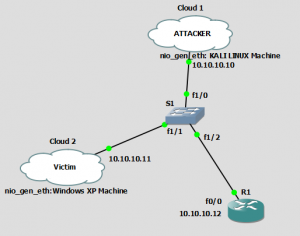
Let’s establish our virtual environment using GNS (virtualization of the Network), Virtual Box or a Virtual machine with two O/S’s (Kali Linux and Window XP). As shown
here we have a network administrator running windows XP (victim) trying to manage its own router (R1) and a Kali Linux machine (Attacker) connected on the same switch (S1).
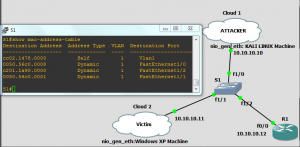
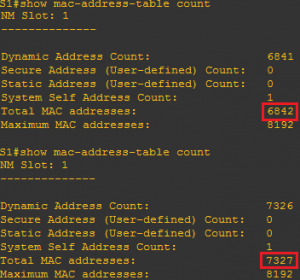
If we issue the command “show mac-address-table” on our switch we will see the CAM table of the Switch which shows the port and MAC addresses of the devices that are connected to it.
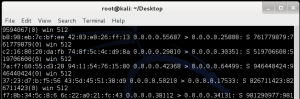
After pressing enter a huge number of fake random MAC addresses will be generated as seen below.
The switch will also dynamically store these MAC addresses in its CAM table. Now we will issue our first two commands on our switch again to see the changes made to the CAM table.
Here the number of the total MAC addresses stored is increasing each time we issue the same command because the Attacker’s machine continues to generate a huge number of fake MAC addresses.
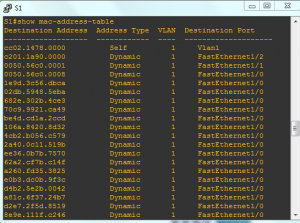
The new CAM table entries will be as the following, notice the large number of MAC addresses assigned to the same port (interface FastEthernet 1/0)
After a couple of minutes our humble switch is forwarding packets as a Hub !!
Now the switch is flooding any received packet from any port to all other ports including the (Attacker), he will receive a copy of each packet sent from the administrator(Vitim) or any other machine to the router (R1) or any other device connected to this switch. By using software like Ettercap the Attacker can change his NIC from the normal operation mode into promiscuous mode which causes the controller to pass all traffic it receives to the CPU rather than passing only the frames that the controller is intended to receive, this mode is normally used for packet sniffing and is also known as man in the middle attack.
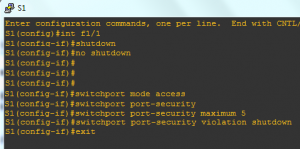
To recover from this attack we first need to shutdown this port from the switch using the two commands shutdown & no shutdown on the attacked interface
To prevent this type of attack we will change the port to an access port by issuing switchport mode access and to apply port security on our port we type switchport port-security, after that we will assign the maximum number of MAC addresses to be stored in the CAM table for this interface using switchport port-security maximum 5. Finally we will choose our violation action that will be applied when the user (attacker) is trying to generate more than 5 MAC addresses associated to same port. We choose to shutdown this port switchport port-security violation shutdown Now if the attacker attempts to perform this attack again on this switch his port will be automatically shutdown, also a log will be generated on the switch informing the administrator that the (attacker) MAC address on this port was trying to attack us and the port state is now down.
About the Author
Ahmed Haytham
Network Security Engineer at Raya Integration