Constructing mature information security awareness and educational models
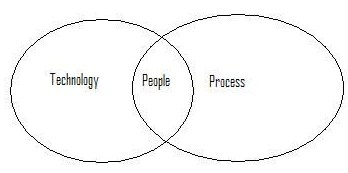
Information Security is defined as protecting information and the systems that hold and support them directly from unauthorized use, access, disclosure, disruptions, modification and destruction. Any organization irrespective of their size and number utilize the following mechanisms for practicing and improving their information security posture. The mechanisms utilized are People, Process and Technology
The only common factor as seen from the diagram is that people manage both process and technology. Therefore every employee permanent, temporary, contractor, business partner, vendor etc has information security roles and responsibilities to be fulfilled. It is therefore imperative that the entire workforce receives sufficient and good quality information regarding security responsibilities.
Information security awareness is extremely critical to any organization security strategy and supporting security operations. In spite of the importance of making end users aware of their roles and responsibilities in reference to security only 64% of US organizations, 48 % of UK organizations and 59% of Indian organizations conduct security awareness programs in spite of the many regulations that make it mandatory. Many of the security incidents that resulted in Millions of dollars in penalties and loss of reputation could have been prevented by proper security awareness and training. This paper not only focuses on end users but also on the technical users and the senior management which are generally missed out.
What value does information security awareness and education deliver?
Having a comprehensive and mature information security educational program will result in better health of the organization in terms of security as well as the organizational
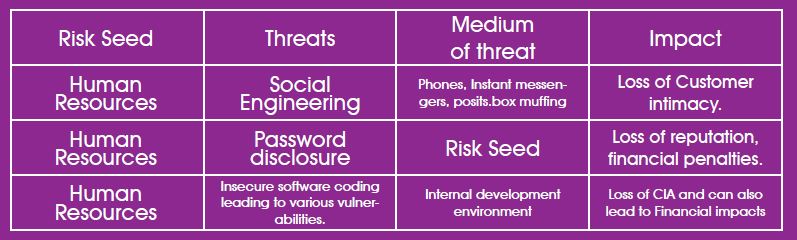
health. Let us now tabulate some of the risks that involve people factor and involves people which can be prevented by effective awareness programs.
From the above table it is clear that Security awareness and training needs to be imparted to all members of the organization. Let us now see how an information security awareness program is constructed.
Pillars of Information Security
awareness and education:
Right People, Management Commitment and Information security policies form the pillars of an effective security awareness and education program.
Information security policies:
Have well articulated and updated information security policies in place that support the vision and mission of the organization. Keep them current in line with the evolving threats and have a review every month by an Internal IT team. Have this review circulated to the senior management. This will ensure that the policies are updated and are being viewed by senior management thereby generating buy in.
Management Commitment:
Get Management Commitment before going ahead with a plan such as this. A mature enterprise wide security awareness program increases the security posture as well as the internal communication posture of the organization which will help foster cross functional effectiveness’ and bring in a healthy working culture. Highlight to them the above advantages and get their nod. Getting their nod also sends positive signals across the enterprise that the management is seriously committed to improving and maintaining security.
Right People:
This is the number 1 ingredient for any organizational success. Having the right people on the team makes all the difference for making any plan/strategy highly successful. Always hire people by conducting a good background check for positions that require no experience. When hiring for senior/mid level positions make sure that people are cross checked across on all areas such as Education, Employment, Previous Employer References, groups, conferences, publications, personal history and check if they are committed towards excellence. This forms the ground for building the plan.
Form a team:
After having the right people on board, you will have to form a Core Committee involving and comprising members across the various business units. The team structure is very vital for success and is discussed below in greater detail.
Core Committee members:
The core committee members should comprise heads of members of all business sections. This will ensure that their support is there which is very vital for a successful awareness program. The CISO/Corresponding person who is responsible for security should also be part of the Core Committee.
Security Awareness Champions group:
Security awareness champions group should be formed which will include senior members across the business. People to be included in this group should exhibit at the least the following qualities:
1. Knows the business: The person selected as awareness champions should have a sound knowledge on business process. This will be very vital when mapping security risks with new process/ policies/strategies of the organization.
2. Competent in their selected field: The person selected should be competent in his/her chosen field. This will ensure that he has the respect of his team members and peers which will be very effective for putting forth ideas in place.
3. Respected by peers: People chosen as awareness champions should be respected by peers in their respective departments. This will ensure team commitment as a person of such caliber will have his voice heard and respected across his team members.
4. Effective Communicator: People should exhibit effective/extraordinary communication skills. These people should be conversant and fluent in one or more languages. Examples include a person conversant in English and fluent in his native language say (Arabic), this will ensure that the diversity factor in organizations has been taken care of.
Security Awareness focus Group:
This group should consist of members across departments who are committed towards excellence and are keen to add value to the organization. These people should have the option of getting promoted as awareness champions as part of their commitment towards information security awareness.
IT awareness group:
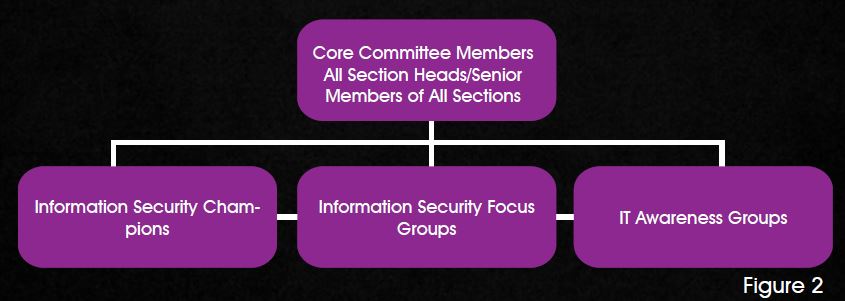
This group will cater specifically to the Information Technology department. This will include senior members within the department and will keep a track of training requirements needed by the departmental people. This group will also measure the success of the trainings given to IT personnel. Formation of the team and team members should be done involving HR, Customer Service, IT and other sections and should have the approval of 3/4 of the core committee members. A sample hierarchical chart is given below for a reference. (Fig 2)
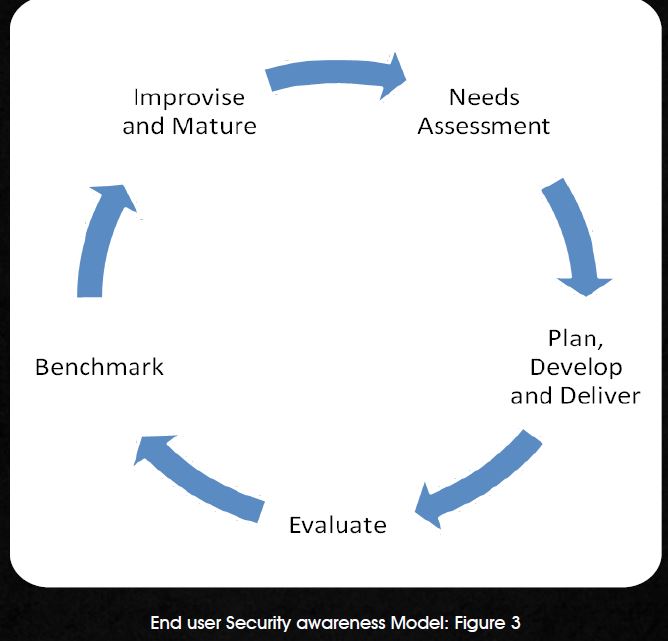
End user Security awareness Model: Figure 3
Identify Needs:
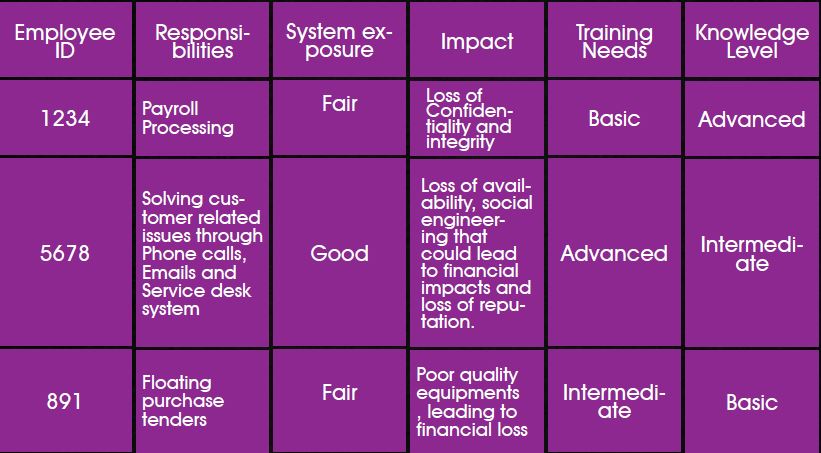
Not all users are equal. This phase will also identify the training needs of each and every individual mapped to their responsibilities handled by them. Training needs are assessed vis-a-vis responsibilities and impacts that can be caused by the responsibilities. Map responsibilities to system exposure, impact, and training needs. A simple matrix that can be used is shown below.
Since we go by the saying not all users are the same, the knowledge of each and every users in terms of security awareness, system expertise and computer knowledge are assessed individually through pre-assessment questionnaires developed by the Information Security Awareness champions. The information security awareness questionnaire should be prepared keeping in mind the normal end user to the advanced user. IT specific assessment questionnaires should be prepared for IT personnel and their knowledge on various domains tested periodically. It is recommended to use web based assessments through the organization intranet portal site for easy collection and improvements. This will also help us analyze gaps and improve knowledge levels of users. Based on answers collected and personal interviews with people classify their training needs and knowledge levels. Have them documented as per the sample format given below. The basic purpose of the sample report is to organize the article and provide an idea and is not intended to be comprehensive.
Needs Assessment Report:
We will describe clearly on what it means by basic, Intermediate and advanced.
Basic Training: Primarily for users whose ignorance can cause the least impact on the organization and their resources. Impact causes negligible financial loss and zero loss of reputation and integrity.
Intermediate Training: For users whose ignorance can cause some damage to the organization and its resources, but does not cause much financial loss and does not damage the reputation of the organization.
Advanced Training: For users whose ignorance can cause significant financial loss and damage of reputation thereby affecting customer intimacy and credibility. Develop and Deliver: After doing a need assessment. Plan, Develop and Deliver security awareness and educational programs across the enterprise. Each process has been described in detail below.
Develop: This step involves gathering available training resources such as people, content an development of training material. The training material should be developed with the following points in mind by the security awareness champions and security awareness focus groups.
– How do we want users to react/follow?
– What skills do we want the users to learn and apply?
– Will this content reach out effectively?
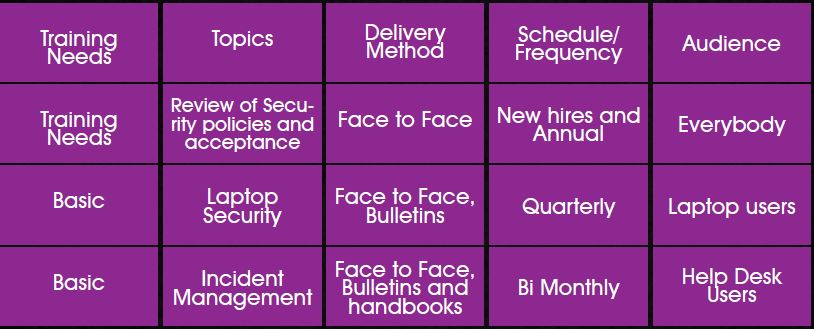
There is series of materials available that requires to be imparted to each and every person in the organization, based on their responsibilities and level of knowledge that is needed, the scope of which is too large to be discussed here. IT service champions in consultations with focus groups must ensure that necessary areas have been taken care of. Classify topics required for each level.
After comprehensive designing and planning, deliver the plan to the end users based on their training needs that have been assessed through various mediums that are available in an organization. The training plan and methods should be ratified by Core Committee, awareness champions and focus groups. General topics ranging from basic to intermediate can be given by Information security focus groups\Awareness champions whereas advanced topics should be delivered solely by information security champions selected from the IT department.
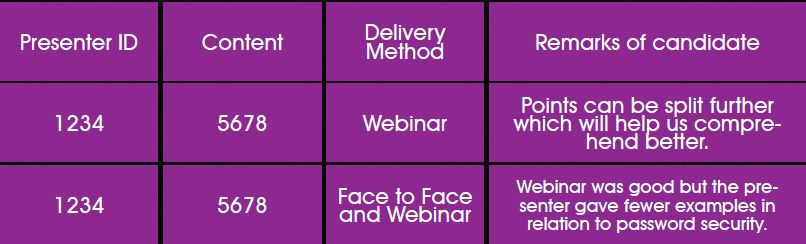
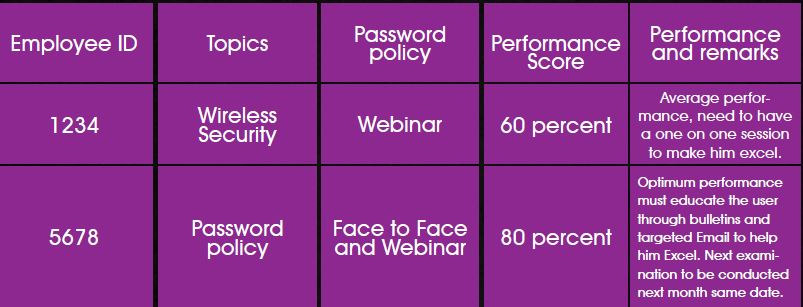
Evaluate and Improvise: Ideally after delivering the content, the end users must be evaluated under controlled environment to check if they have comprehended the topics properly. A post assessment report template has to be prepared to see if the outcome of the training is as desired. The Assessor must also get inputs from the candidate to see what can be improved in terms of content, presentation etc. All collections if done online will be easy to comprehend and deliver better results in future. Benchmark the current performance and continually improvise it for matured results.
Sample Assessment and Improvisation Report Template of Content and Assessor:
Sample Candidate Assessment and Improvisation
Template:
The post assessment reports are stored in a repository accessible to all the security awareness champions, Core Committee members and focus groups. This will ensure that continual improvisation happens on a regular basis. The security champions can also develop a Department Based Grading system to check which department performs best and recognize them through internal newsletters. This will certainly improve the organizational health in terms of security and performance.
Information security education does not end with End users as is the case most organizations do, their own IT department also needs to be educated on a continual basis to keep them updated with the latest compliance regulations, evolving threats. The process has been described above. Security Awareness Model for IT
personnel: Figure 4
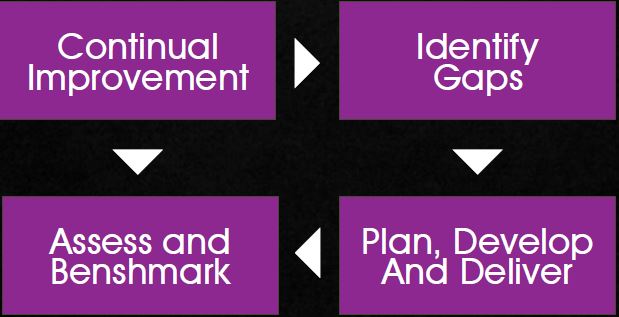
Identify Gaps:
The CISO/IT manager and the Information security personnel must conduct regular audits on their department people to check if they are equipped with the knowledge to handle evolving threats, knowledgeable on new standards, current trends etc. A “needs assessment” is conducted through needs assessment as described for end users.Invest in Education materials: The organization must invest in good quality educational materials that are available for IT people such as ISSA, ISACA, ISC2, IEEE etc. By Investing in these journals and educational materials the organization is certainly bound to increase the learning curve of their IT people which will result in better codes, process improvements etc. These
journals pave the way for identifying an effective needs assessment.
Plan, Develop, Deliver, Assess and Improve: After conducting a “needs assessment,” check to see whether internal people are qualified enough to fill the gap or not. If so prepare content and plan delivery methods for educating them. In some cases it becomes necessary to bring in external expertise to train our people. In such cases depending on budgetary constraints train the senior members/a group, and retrain them asking them to train other members. This way knowledge is resonated throughout the organization. Document the training, assess those using internal feedbacks and keep them improvising continually. IT based security educational needs must be done bi monthly for better quality to keep in line with evolving threats and regulations.
Conclusion
Information Security awareness and education is continuous and continual. With proper management support, right people ,good team formation and involving all business units in the process
we get their commitment which will ensure a successful security awareness and education to one and all in the organization going beyond security education and awareness to increasing cross functional effectiveness and organizational health.
References
http://www.pwc.com/en_GX/gx/information-security-survey/pdf/pwcsurvey2010_report.pdf
csrc.nist.gov/publications/nistpubs/800-50/NIST-SP800-50.pdf.
About The Author
Vinoth Sivasubramanian, I am a founding member of ISSA UAE and a working committee member of International Cyber
Ethics. CEH,ABRCCIP, ISO 27001 LA,