CSRF Attack
What is CSRF?
CSRF (Cross-Site Request Forgery) is web application vulnerability. It enables the attacker to obtain any kind of information through creating a website or email after the authenticated user/ viewer access this website or e-mail remotely. The purpose of this malicious code is to redirect the user’s request to a specific task URL. Actually this kind of attacks is severe and difficult to detect, because all the process is done without user’s knowledge.
Example
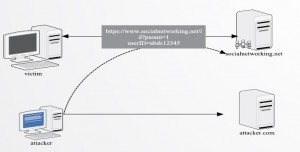
Imagine that a user want to chat with his friends through his favorite social networking site (for instance www.socialnet.net). Unfortunately this website allows its users to insert their images into the website such as the avatars for forums or social networks as in face book. The normal action taken in this case is like this: (the user’s method)
< img src=http://socialnetworking/image.jpg>
The attacker’s method:
< img src=http://socialnetworking/changepassword?newpassword=password12345”>
Illustration
Figure 1:
Figure 1: example on how the CERF attack would happen.
There are many ways used by the attackers to execute the CSRF attack. The most popular way is to use an HTML image tag, or JavaScript image object. As I stated previously; the attacker will embed these tags into an email or website. Without the user’s knowledge, he loads the page or email, by which a request to any URL that the attacker has the link. Below is a list of the common ways that an attacker may use to try sending a request.
How to Avoid Such Attacks?
After we illustrated an overview on CSRF attack and how attackers think about it. Now you have to know to keep yourself safe. I personally recommend reviewing the OWASP CSRF attack prevention cheat sheet which can be found in [https://www.owasp.org/index.php/Cross Site_Request_Forgery_%28CSRF%29_Prevention_Cheat_Sheet]
In the OWASP web site you can find also, tools that help you to test your code, and more about other related attacks in details.
Actually, if you look online for how to prevent yourself from CSRF attack dozens but millions of articles and resources online will give you suggestions about that. But if you have a deeper look at most of these best practices as they claim you will find there is a huge misconceptions which discussed by Eric Sheridan (who was one of the team who reviewed this update of the Top 10 web application vulnerabilities by OWASP you can find more about on [https://www. owasp.org/index.php/Top_10_2010]), to be as follows:
1. Only accept POST
• Stops simple link-based attacks (IMG,frames, etc.)
• But hidden POST requests can be created with frames, scripts, etc…
2. Referrer checking
• Some users prohibit referrers, so you can’t just require referrer headers
• Techniques to selectively create HTTP request without referrers exist
3. Requiring multi-step transactions
• CSRF attack can perform each step in order
Conclusion
Due to the severity of CSRF attack targeting our financial, health care, and computer infrastructure which enables the attacker to take advantage of any authenticated transaction the user can do.
As I stated before you can find your bank account is transferred to another account with your knowledge or more than that, your password on any web application is modified, on that you can measure. The severity of this attack is based on all the transactions done by the attacker sound authenticated.
Acknowledge
I hereby certify that most of this article has a reference of other authors, in addition to that some of the code above has been taken from another web sites which is referenced in the reference section. Besides I would like to thank the editorial team for making this work come
to the light. If you have any suggestions, comments, or questions. Please contact me @[email protected]
Reference and Further Reading
1. OWASP [https://www.owasp.org/index.php/Cross-Site_Request_Forgery_%28CSRF%29]
2. Robert Auger @ [http://www.cgisecurity.com/csrf-faq.html]
3. [http://haacked.com/archive/2009/04/02/anatomy-of-csrf-attack.aspx]
4. [http://knol.google.com/k/preventing-cross-site-request-forgeries-csrf-using-modsecurity#]
5. [http://evilzone.org/tutorials/csrf-tutorial-by-connection/]
6. [http://www.gnucitizen.org/blog/csrf-demystified/]
7. Eric Sheridan, Cross-Site Request Forgery: Danger, Detection, and Defenses, can be found on OWASP
8. [http://www.techrepublic.com/blog/networking/csrf-attacks-home-dsl-routers-are-vulnerable/756]
9. Jesse Burns, Cross Site Request Forgery , An introduction to a common web application weakness, can be found in https://www.isecpartners.com
10. Kurt Seifried, Attack of the CSRF, 2008
About The Author
I am the OWASP Mansoura– Egypt chapter leader. Neil is an Information Security
researcher in the Faculty of Computer and Information Sciences at Mansoura
University-Egypt.
Ahmed Nile