Fake Antivirus
Executive Summary
• By performing (behavior and code analysis) analysis on this packed executable sample it has been identified as Fake Antivirus or Rogue Security Software
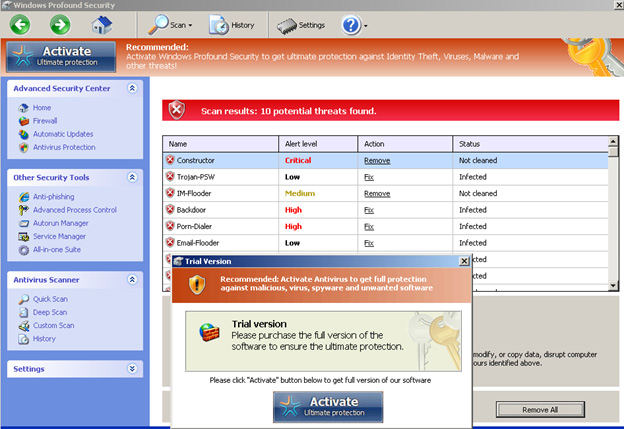
• Fake Antivirus is malicious software which fakes to be an Antivirus solution which, once installed on a user’s computer, pretends to scan the system and finds number of computer viruses and/or malware as shown below. But really the fake Antivirus does not perform any scan. Once it has reported the presence of these hypothetical malware, the FakeAV usually proposes for the user to buy a paid version to clean the computer. So FakeAV used to deceive users into paying money for fake or simulated removal of malware (form of ransomware)
• Rogue security software has become a growing and serious security threat in desktop computing in recent years. Because they have visual payloads. It often displays pop-up messages telling users that their machines have been infected. This may cause panic among users, pressuring them to purchase rogue antivirus applications in the hope of resolving the issue.
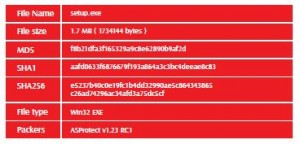
Sample Identification
Packing and Anti-analysis techniques
• According to PEiD the sample packed using “ASProtect v1.23 RC1” which designed for software protection of applications, targeted for software developers. It provides quick implementation of application protection functions such as working with registration keys and creation of evaluation and trial application versions.
• ASProtect Provides a number of anti-analysis technique (IsDebuggerPresent, GetTickCount,… ) so its recommended to use OllyDbg ‘s plugings like OllyAdvanced in order to bypass the anti-analysis techniques.
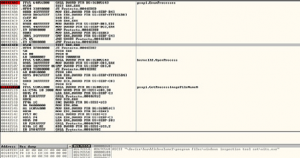
• To unpack the sample by step the first three instructions you will find PUSHAD instruction which used to push all registers into stack. The packers
use this instruction to buck up the registers original state before going on the unpacking code and once unpacking finished the registers contents will be restored again .
• So by putting hardware breakpoint on the address which will be pointed by ESP register (after the PUSHAD instruction is executed) you will detect whe the sample restore the registers which means when the unpacking code is finished.
Main Findings
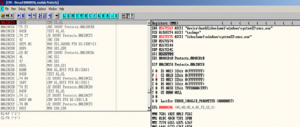
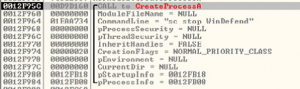
1- The malware starts by creating new process named “setup.exe” which installs a hook procedure that receives a useful notifications to a CBT application using SetWindowHook API with hook id=5
2- Then It drops a copy from the original malware file on the path “C:\Documents and Settings\Administrator\Application Data\Protector-xxxx.exe” and creates new process “Protector-xxxx.exe” which responsible for the major malware malicious activity after that as setup.exe deleted itself and terminated
3- “Protector-xxxx.exe” sets values in the following registry keys
• HKCU\Software\Microsoft\Windows\CurrentVersion\Settings\ID=”0x00000000”
• HKCU\Software\Microsoft\Windows\CurrentVersion\Settings\UID=”hodrpyibot”
• HKCU\Software\Microsoft\Windows\CurrentVersion\Settings\GConfig=””
• HKCU\Software\Microsoft\Windows\CurrentVersion\Settings\net=”2014-10-14_6”
4- Also it attempts to ensure its persistence on the infected machine by creating the following registry entry to automatically start the malware whenever Windows launches
• HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Inspector
5- Then malware creates another thread used to enumerate all running processes on the system by using EnumProcesses API which retrieves the process identifier for each process object in the system and GetProcessImageFileName API which retrieves the name of the executable file for the specified process. and compares it with defined string list contains:
• taskmgr • regedit
• iexplorer • procexp
• defender • msseces
• msascui • defender
• avastsvc • egui
• avgnt • avcenter
• msconfig • mbam
• chrome • opera
If it finds any process from this list it terminates the process. So it disables Windows system Utilities like Task Manager and Windows Registry and will block user from running certain programs like the three mentioned browsers, process explorer monitor tool and security programs related processes
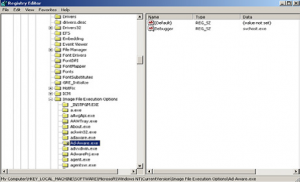
6- After that malware uses “HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\” registry key for doing two malicious behaviors the first one to block various popular security products and anti-viruses programs from running on the system by creating large numbers of entries under this key each one for one of popular antiviruses and sets value “debugger” with “svhost. exe” as shown below so when the operating system determines which executable is going to be started it checks the registry key for a debugger. If it finds one, it will launch the debugger instead of the application
The second activity is adding the following two registry entries under this key and it sets the value of the debugger with its malicious file so every time regedit. exe or taskmgr.exe called the malicious malware file will runs instead of them
• HKLM\SOFTWARE\Microsoft\Windows NT\Current-Version\Image File Execution Options\taskmgr.exe\Debugger
• HKLM\SOFTWARE\Microsoft\Windows NT\Current-Version\Image File Execution Options\regedit.exe\Debugger
7- Malware tries to connect to domain “galaint.updateinfostat.pl” using “mshta.exe” windows process which is known as an interpreter for the Microsoft Scripting Host, so it is responsible for executing HTML applications (.hta files) and helping scripts run in Windows .But the domain is now offline
8- Then malware stop the following security related services using SC tool “sc.exe” as shown below
• WinDefend • Msmpsvc
• Ekrn • AntiVirService
• AntiVirSchedulerService
• GuardX
9- Malware disables UAC (User Account Control) by setting the value of EnableLUA to 0 and it suppress UAC consent prompt dialog by setting the values of ConsentPromptBehaviorAdmin and ConsentPromptBehaviorUser to 0 under the following registry key
• HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\
10- malware also disables the warning message that alerts user when the internet explorer redirect from secure web site (https://) to another web site by setting the value of WarnOnHTTPSToHTTpRedirect to 0 under the following registry key
• HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\
11- Then it disables certificate revocation list checking (which contains all the serial numbers of the digital certificates which have been revoked ) by setting the value of CertificateRevocation to 0 under the following key
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\
12- It Installs a hook procedure that monitors keystroke messages and a hook procedure that monitors mouse messages using SetWindowHook API with hook id=2,7
13- The malware create (creates) file named “C:\Documents and Settings\Administrator\Application Data\ result.db”. it contains the fake program results which displayed by the program when it claims to scan the system
14- The malware open two UDP ports
15- After the fake program installed it gives the user warning and error message in order to deceive him to activate the program. When user click to activate it. the malware tries to connect to another domain “fdd91a- 64ce20e17d.payinfohelp.pl” which is also offline
16- Malware tries to detect the real ip address of the victim machine by connecting to domains “cmyip. com” and “showrealip.info”
Removing Steps:
1- Terminate malware processes “Protector-xxxx.exe”, “mshta.exe” using any working tool “as mentioned before some popular tools will not be working” so using tool like process hacker terminates the processes
2- Using any registry editor for example registrar registry manager free edition removes all malware related registry entries manually or you can just remove the registry key which related to your favorite antivirus for example using Malwarebytes Anti-Malware the following registry entries must be removed manually before using it then run it to remove everything
• HKLM\SOFTWARE\Microsoft\Windows NT\Current-Version\Image File Execution Options\mbamservice.exe\Debugger
• HKLM\SOFTWARE\Microsoft\Windows NT\Current-Version\Image File Execution Options\mbamgui.exe\Debugger
• HKLM\SOFTWARE\Microsoft\Windows NT\Current-Version\Image File Execution Options\mbam.exe\Debugger
About The Author
Doaa Wael, Malware analyst at EG-CERT