Fighting Zero Day Vulnerabilities using Microsoft EMET tool
Introduction
Zero Day Vulnerability is one of the most crucial and often missed threats, Zero day vulnerabilities can be extremely serious security risks and although there has been a lot of discussion, blogs and warnings about the Zero-Day vulnerabilities, it is still not common and clear for most of security teams. Hackers and bad people are on the internet trying to attack you to steal your money, data or get you out of business. It’s pretty simple, all they need to do is sending you a fake email that looks to be from your bank, corporate or any legitimate source (not always from African Princesses). This email is sent to thousands of people hoping that few of them will just open the link and get the malware installed on their computer.
Unfortunately most of this malware is silent and mostly won’t be detected by your firewalls or Antivirus (Advanced AV can detect some of these malware) however the key to defend against these attacks is first user awareness which should help you in more than 90% of the cases and using tools as EMET for Windows which we are going to discuss in this article. In this article I try to explain what is exactly this zeroday exploits and why is it so dangerous, risky and most importantly I discuss new approach using EMET (Enhanced Mitigation Experience Toolkit) to protect your assets, systems and data from this kind of attack.
What is Zero-Day Attack?
Normally Hackers and bad people tend to exploit a vulnerability or a hole in your security system to gain unauthorized access to a system and hack it for different purposes. As security professionals we tend all the time to ensure that our systems are fully patched, our devices have the latest firmware, Firewalls are in place with the most efficient rules running on them and we are using the latest updated software versions. However just imagine in your house that you have a vulnerability or a hole in your system. For example, a broken basement window that neither you nor your security guard are aware of. The thief or intruder gained access to this window and was able to access the house. You did not become aware of this vulnerability or broken window until the intruder already exploited it and used it to attack your home. This is Zero-Day attacks and Vulnerabilities. Zero-Day attack is an attack that makes use of an unknown vulnerability in your computer application, software or hardware. You and the software vendor are not aware of it. It’s called Zero-Day attack because the attack occurs on day Zero of being aware of this vulnerability and attack. The Vendor or the Software developer who created this program or software had zero days to discover, address and fix or patch this security or vulnerability problem.
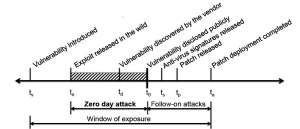
Zero-Day Attack Lifecycle
The lifecycle of a zero-day attack and Vulnerability exploitation is divided into the following seven phases:
1. The vulnerability is being discovered by the bad guy/ Hacker.
2. The hacker exploits this vulnerability and generates his code or attack to hack this vulnerable system.
3. The Vulnerability is discovered by the Vendor either by his own team (while testing the software) or from the feedback and problems reported by the customers.
4. The Vulnerability is released for the public and everyone having this software or application should be aware of it.
5. The first action taken by the Security vendor is to release an Antivirus new signature or IDS/IPS (Intrusion Detection/Prevention System) signature to at least stop the attack from hitting your application or system.
6. The Next step done by the Security vendor will be to release a patch or fix to fully close and solve this problem (Root Cause Fix).
7. The Last phase will be the client reaction and time when he received this patch/fix and when it’s deployed to his applications/systems (Incident Response). Many Customers will first test this new patch or fix first before deploying it (Recommended way).
Fig 1. Zero-Day attack Life Cycle, Source: http://securityaffairs.
co/wordpress/
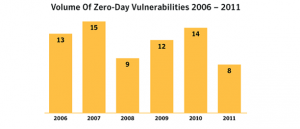
Zero-Day Statistics in 2013
Based on different statistics from different companies, it looks like 2013 was the year of Zero-Day exploits nd attacks. FireEye has identified seven (7) Zero-Day exploits during the First half of 2013 while Symantec identified eleven exploits (11) in the first quarter only of 2013. The main concerns by both reports are that these attacks cover a wide range of applications as Oracle Java, Microsoft Internet Explorer, Adobe Flash and Adobe PDF. This is large number of attacks/ vulnerabilities compared to previous years as shown below.
Fig 2 Volume of Zero-Day Vulnerabilities
2006-2011, Source: http://www.symantec.
com/threatreport/topic.jsp?id=
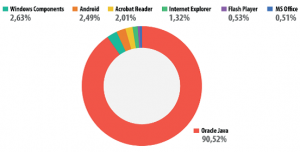
The Most vulnerable and targeted application is Oracle Java. It’s widely installed on millions of computers and it’s not periodically or automatically updated on most systems. The below figure from Kaspersky Labs show the percentage of threats on various applications and malware evolution in the first half of 2013.
Fig 3 Malware Evolution in 2013 – Zero-Day
Attacks, Source: http://www.securelist.com/en/
analysis/204792316/Kaspersky_Security_Bulletin_
2013_Malware_Evolution#_Toc373346266
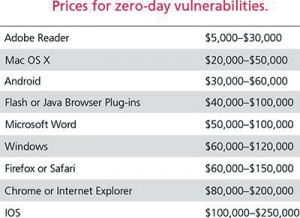
The most interesting part with these numbers is the business done with Zero-Day vulnerabilities, there are very specific organizations searching and looking for unknown vulnerabilities to sell them to any willing buyers to use them in any manner. The prices for such vulnerabilities is quite high as per the below table.
Fig 4: Forbes Sources – Price List 0-day vulnerabilities
Source: http://resources.infosecinstitute.com/a-worldof-
vulnerabilities/
How does EMET fit in the picture?
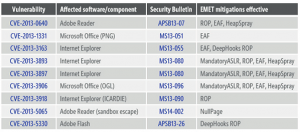
Protection against Zero-Day attacks is as if you are searching for a needle in haystack, Microsoft EMET tool is a free tool that anticipates the common attack techniques used by hackers and stop/block and terminate this attack. It’s not an Antivirus or malware protection tool so even the attack is blocked you would still need to check with the software vendor for the permanent fix for the vulnerability. EMET is highly recommended by several frameworks and governing policies as SANS 20 Critical Controls, U DoD DISA Security Technical Implementation guides and it’s ranked #7 in the Australian Signals Directorate (ASD) mitigations against cyber-attacks. During the year 2013, 4 Internet Explorer, 2 Office and 3 Adobe Vulnerabilities were mitigated using EMET. So far in the 2014 the most two severe Microsoft Exploits and zero-day vulnerabilities (IE and RTF) where both detected and mitigated using EMET.
Fig 5: Vulnerabilities mitigated in 2013 by EMET, Source:
Microsoft
How does EMET works?
The core protection of EMET is the memory mitigation techniques (13 memory corruption mitigations) since most of the attacks are targeting the memory, examples of used mitigations are the ASLR, SEHOP, Null page, DEP, ROP………etc. A new feature in the latest EMET 5.0 tool is the attack surface reduction (ASR) which is a plugin blocker that allows blocking plugins based on zones in IE or plugins in general in Office products. One of my favorite is the Certificate Chain Trust where EMET will run while connecting to an HTTPS site and validate the other end SSL certificate and the Root Certification Authority (CA) that issued this certificate versus the corresponding pinning rule configured by the user, this is very beneficial to detect the manin-
the-middle-attacks. Example is to ensure you are connecting to the legitimate Facebook, twitter, Gmail service instead of being redirected to fake site and get your credentials stolen.
EMET Installation
The latest current public version is EMET 5.0 released on July 2014 and it can be downloaded from http://www. microsoft.com/en-us/download/details.aspx?id=43714
EMET Requirements:
1. Dot Net Framework 4
2. For Windows 8 and IE 10 Protection you need to have KB2790907
Installation Steps for Standalone users:
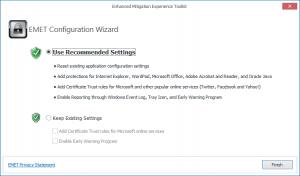
1. EMET installation is straight forward, just few click on the MSI file and you are done. (Ensure to run the MSI as administrator)
2. The final screen in EMET installation is where you will choose between the recommended settings or manual settings. For now we will choose recommended settings.
Fig 6: EMET Configuration Wizard
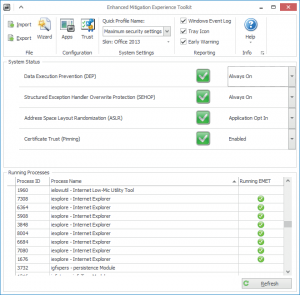
After Installing EMET you can go back to the configuration Wizard by clicking on the Wizard button on EMET Home as shown below
Fig 7: EMET Console
EMET Basic Configuration
The bottom of EMET main page shows the Running Process, since EMET default configuration enables protection for Main Microsoft Products as Internet Explorer so when I opened Internet Explorer to browse the Internet it get listed in the running process with green check to confirm that EMET is enabled on it (Check Fig.7) and protecting this application using EMET Mitigation techniques.
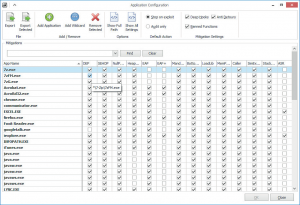
EMET tool comes with another list for the popular software such as google Chrome, Firefox, iTunes and most importantly Java. To Import the popular software list you need to go to the main page and check import and point to the EMET default installation folder\Deployment\Protection Profiles and choose the popular software.
After importing the new list of apps, you may click on the Apps button and you will see the list populated as shown below.
If any of these apps were open before importing the software as Java or Firefox you will need to close it so that EMET can start protecting it on the next launch of the software.If you have any special Program not listed (EXE file), you can click on Add Application and add it to the list.
Ethical Responsibility and Disclosure
During 2013 there has been several blogs and discussions over the internet discussing some NSA (National Security Agency) Servers codenamed FoxAcid. These servers have a wide-ranging menu of software exploits (Not known or publicly disclosed) at its disposal to tailor the right attack to the targets it wants to monitor. These servers traps their targets to connect to them by any mean (Program, website, email link………etc.) and then they can know everything about this system software and applications used and prepare/Launch the appropriate exploit when needed. For more information you may check this interesting article http://arstechnica.com/security/2013/10/nsasaves- zero-day-exploits-for-high-value-targets/
This raised the question of how ethically should we do this? Is it something acceptable? Is it allowed for issues related to National Security? Are these Customers or organizations aware that they purchased a software with unknown vulnerabilities?
There are several events and conferences that encourage developers, testers or Ethical Hackers to discover and disclose these vulnerabilities as Pwn2Own or Google’s Chrome bug bounty program. They reward hackers for discovering and responsibly announcing these threats. If it’s discovered by the Software vendor or application owner then it’s his responsibility to patch/fix it as soon as possible and inform the public to patch their systems.
Conclusion
Zero-day attacks have been around for long time and will continue to be there since humans make software and there will always be errors. They are very difficult to prevent because of their nature and being unknown vulnerabilities where there isn’t any patch or readymade fix or even antivirus signature or firewall rule to detect it.
If you are responsible for protecting Windows system then it’s highly recommended to add the EMET tool to your security arsenal of tools as it tries to fill the gap and complete the whole picture.
About The Author
Ahmed Nabil, IT Manager | Security, Networking, System Engineering