Futuristic Approach to Ensuring Data Security in Clouds
Information Technology has come a long way ever since computers were invented. Similarly Information Security has come a long way. Trends such as Cloud Computing have been helping Small and Medium Investors and Innovators (SMIs) by reducing the initial cost of deployment and maintenance. This will definitely pave a new path ahead for many people. With emerging trends such as these data security in the Clouds must not be viewed in the traditional triadic way but must be viewed in a different way.
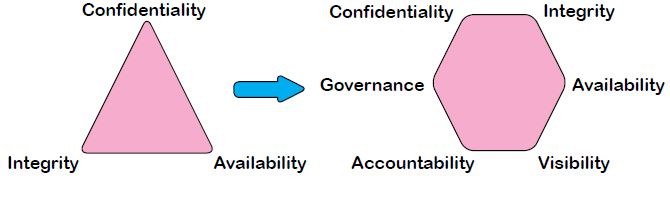
This paper will discuss ways on how data security paradigms can change in the near future and ways to address the new. Traditionally Information Security has been governed by the “CIA” triad, namely Confidentiality, Integrity and Availability, but this is bound to change in the future especially with data being spread across the globe. This model will ensure a considerably high level of data security and authenticity:
Since there are enough materials and resources available already to address the first three parameters such as Confidentiality, Integrity and Availability we will focus on the other
three parameters namely Visibility, Accountability and Governance. We will focus this article from a Process and Governance perspective. A clear well-defined Service Level Agreement (SLA) is the first step in ensuring the security of our data. Here we provide some fresh approaches to drafting an SLA that will deliver a win-win situation.
1. Accountability:
Accountability is a concept in Ethics and Governance with several meanings. It is often used synonymously with concepts such as responsibility and answerability. From a modern management perspective it can be coined in two words “Stupendous leadership” , this can be looked at from either a people perspective or
from an organizational perspective ,wherein both the people and the organization go beyond the call of their duty to create sustaining and winning relationships. Here are some factors that can be woven into the Service Level Agreement:
1.1 Availability:
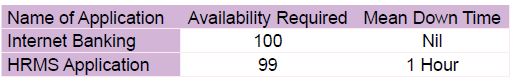
Draft SLAs which will clearly enlist the minimum time that the organization can hold on disruptions. This is because certain applications in an organization will not be critical as compared to their front-line applications. This way the customer ends up getting better quality of service for their most critical applications. A sample template is given below which can be used as a cue:
1.2 Rewards Management :
This is something new, draft agreements that clearly state the rewards that you will share with the provider if the ultimate goal of providing secure and reliable data quality is met; make them understand the metrics that you require for sharing incentives. Also provide certificate-ofexcellence rewards to the people who maintain your infrastructure and help achieve business excellence.
1.3 Loss of business:
Clearly state the legal and other risks that the vendor will incur if they do not meet the metrics that are deemed fit by the organization; outcomes could range from cancellation of contracts to fines imposed due to legal obligations.
1.4 People Employment:
Clearly enlist the kind of people who must be employed to manage your data and infrastructure, the kind of checks that must be done on those people, the credentials (degrees and certifications) that they must hold.
1.5 Good Governance Practices:
Ensure that an organization such as an Internet Service Provider (ISP) will practice good governance principles in reference to management, which is basically corporate governance that extends beyond IT governance. Conducts of good governance guides are available in the OCEG Red book. Organizations that practice good governance are more sustainable in the long term. To cite an example, in the case of an Internet Service Provider going in for a merger or acquisition the ISP should ensure that customers are properly informed and have visibility on what is happening to their data.
1.6 Good IT practices:
Make them accountable to follow good IT practices such as ITIL, SAS70, etc. This will ensure that your data is taken care of properly, as organizations that have these certifications get audited by an independent body. If this is not feasible, get them to follow at the least good Incident Management, Change Management, Release Management, Problem Management and Security Management procedures as per ITIL or any other leading standards.
This will ensure confidence amongst stakeholders as well as management.
2. Visibility:
One of the biggest challenges of Cloud Computing is gaining visibility into the infrastructure of the service provider. Most organizations will provide some sort of certification such as ISO 27001 but does that ensure that everything is taken care of? Unfortunately it does not. So how should an organization tackle visibility? Here are certain steps to do so:
2.1 Have a dedicated team in-house:
Have a small but dedicated in-house team of system admins, network admins, or security personnel who can mark the nature of data as to whether it is critical/semi-critical/normal and also monitor the movement of data. The KRA of this team should be to report violations and Log anomalies.
2.2 Implement CCTV Monitoring:
Through CCTV monitoring the customer can have a ground view on the physical security of the place in which the data resides. Record the findings, review them every month, note observations, circulate the observations and archive them on an external storage. These findings will be particularly useful when dealing with legal issues arising out of operations occurring across the globe.
2.3 Identity Management and Access Control:
Ensure that the service provider give you the power to enforce Identity Management and Access Control privileges as per your requirements; for critical systems implement dual identity authentication wherein changes on require the acknowledgement of two people. Implement Authentication, Authorization, and Audit (AAA) for these systems and have them logged on a sys-log server.
2.4 Backup:
Business Continuity and Disaster Recovery are critical components of availability but the CIO needs to ensure that they have first-hand facts on the back-up data, as to where it is located, who has access to it, and how the data is being managed.
2.5 Implement Logging Server:
Implement a logging server wherein all transactions carried on your infrastructure and data will be logged to this server. Provide no service provider access to this server; access to this
server must rest with a specific group of people from within the organization, such as the CISO or CIO only. Ensure that the log files are read-only.
3. Governance:
This pillar is based on the paradigm trust-but-verify. In spite of getting all the above factors correct the CISO or CIO must adopt an audit-based approach. We present a multi-pronged governance approach here.
3.1 Risk Management:
Have a quarterly risk assessment conducted by your internal security team in line with international standards such as NIST or COBIT. Record the observations and have them circulated.
3.2 Vulnerability Analysis and Penetration Testing:
Have a VA/PT done by your internal team every half year and a yearly VA/PT done by a team of external specialists; this will help uncover surprise items and mitigate risks.
3.3 Internal Audit:
Have a year-end audit conducted by an internal team and a similar audit done by external auditors, who are specialists. Have the audits collated, and discuss the results with the top management of service providers. Identify concerns and areas for improvements and have them addressed through various compensating mechanisms.
Conclusion:
Cloud Computing is here to stay and will change the way data is being managed, stored and processed. By following the procedures laid out above the CISO/CIO can ensure that a high level of data security can be achieved. The above process requires well-planned strategy, budget and resources but going by the Return-On-Investment (ROI) that Cloud Computing provides management will hardly say NO.
About the Authors:
Vinoth Sivasubramanian,
Professional security expert focussing to reach pinnacle of excellence in areas of IT security , governance , Ethics and Leadership.
Mohamed Mohieldeen
I am the Vice President Service Delivery and Strategy of Intrendz Consulting
Mail : [email protected]