ISO/IEC 27001:2013 PART1
Overview
In this article I will provide an Overview of A new Information Security Management System Standard ISO/IEC 27001:2013 , . ISO/IEC 27001:2013 Provides requirements for Establishing, Implementing, Maintaining and Continually Improving an Information Security Management System.
The adoption of an information security management system is a strategic decision for an organization. The establishment and implementation of an organization’s information security management system is influenced by the organization’s needs and objectives, The standard covers all types of organizations (e.g. commercial , government agencies, non-profits), all sizes (from micro-businesses to huge multinationals), and all industries/ segments (e.g. retail, banking, defense, healthcare, education and government).
The Information Security Management System (ISMS) preserves the Confidentiality, Integrity and Availability of information by applying a Risk Management process and gives confidence to interested parties that Risks are adequately managed
Confidentiality – ensuring that access to information is appropriately authorized
• Integrity – safeguarding the accuracy and completeness of information and processing methods
• Availability – ensuring that authorized users have access to information when they need it.
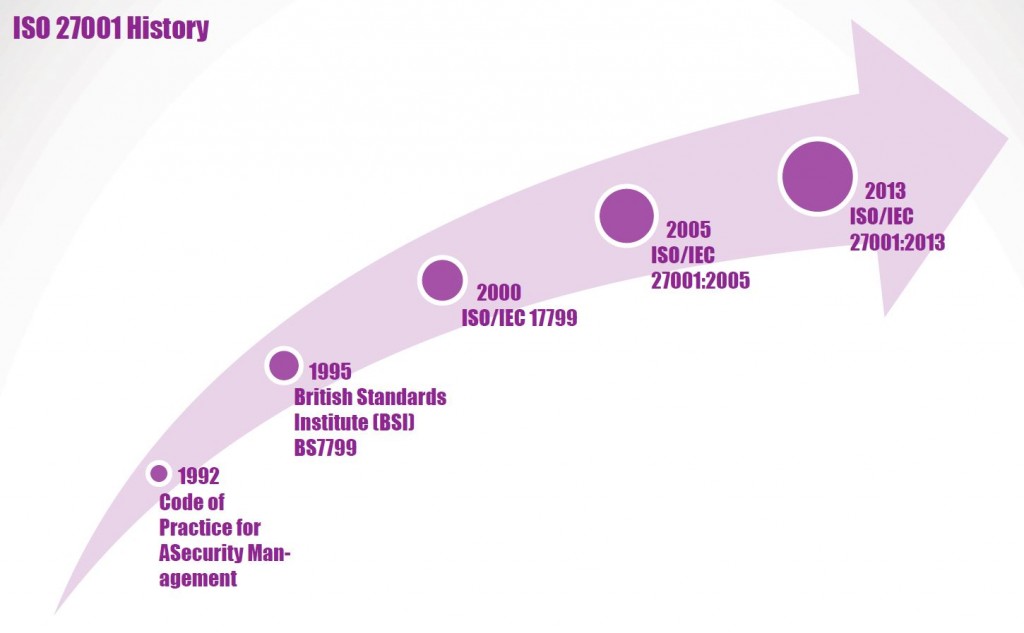
ISO 27001 History
• 1992
The Department of Trade and Industry (DTI), which is part of the UK Government, publish a ‘Code of Practice for Information Security Management’.
• 1995
This document is amended and re-published by the British Standards Institute (BSI) as BS7799.
• 2000
In December, BS7799 is again re-published, this time as a fast tracked ISO standard. It becomes ISO/IEC 17799
• 2005
ISO/IEC 27001:2005 is published, this is a specification for an ISMS (information security management system), which aligns with ISO 17799 and is compatible with ISO 9001 and ISO 14001.
• 2013
ISO/IEC 27001:2013 A New information security standard published on the 25/09/2013. It cancels and replaces ISO 27001:2005
ISO 27001 Family
The Family of ISO 27000 provides best practice recommendations on information security management, risks and controls within the context of an overall information security management system (ISMS), Alignment to management systems for quality assurance ISO 9000 Family
ISO 27000: Vocabulary
ISO 27001: Information Security Management System Requirements
ISO 27002: Code of Practices
ISO 27003: Information technology – Security techniques – Information security management system implementation guidance – Published 2010
ISO 27004: Information technology – Security techniques – Information security management – Measurement – Published 2009
ISO 27005: Information technology — Security techniques — Information security risk management – Published 2011
ISO 27006: Information technology — Security techniques — Requirements for bodies providing audit and certification of information security management systems – Published 2011
ISO 27007-ISO 27008: Information technology — Security techniques — Guidelines for auditors on information security controls – Published 2011
ISO 27011: Information technology — Security techniques — Information security management guidelines for telecommunications organizations based on ISO/IEC 27002 – Published 2008
ISO 27799: Health informatics — Information security management in health using ISO/IEC 27002 Published 2008
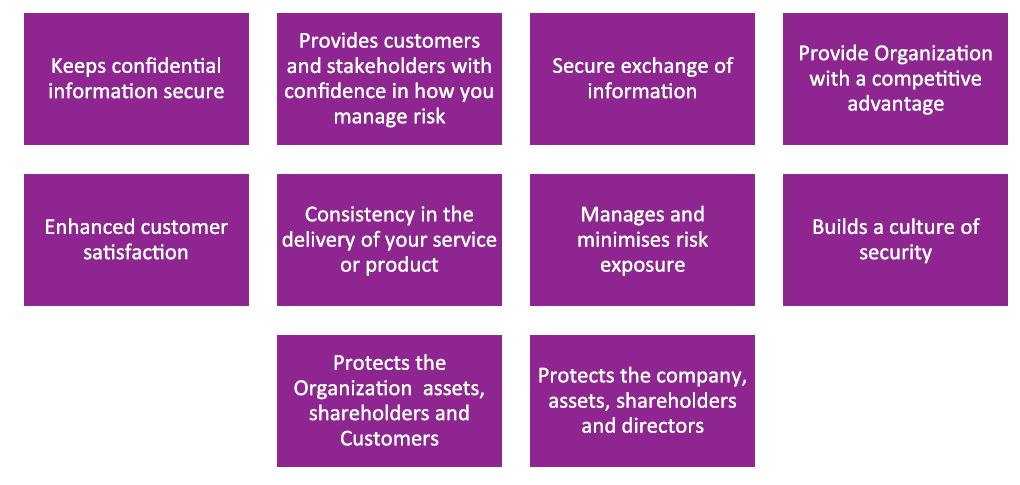
Benefits of ISO 27001
ISO/IEC 27001:2013 Implementation, Certification from a certification body demonstrates that the security of organization information has been addressed, valuable data and information assets properly controlled. Also there is List of benefits By achieving certification to ISO/IEC 27001:2013 organization will be able to acquire numerous benefits including:
ISO /IEC 27001:2013 Structure and Content
It’s a new format and wording of Information Security Management System ( ISMS ). This structure is a new formulation of ISO Management System and alignment with “ Annex SL “ that allows an organization to Made multiple implementation at the same time for related ISO Management Standard. Now any organization can Implement ISO/IEC 27001:2013 Together with ISO 22301:2012 (Business Continuity Management System) at same time.
Structure
All Below from 4 to 10 are Mandatory Requirements for Implementation and Certification of ISO/IEC 27001:2013
0. Introduction
The Objective of an Information Security Management System (ISMS)
1. Scope
State the Applicability of Standard within Context of Organization
2. Normative References
Overview and Vocabulary
3. Terms and Definitions
a brief, formalized glossary Including Common Terms and Definition of ISMS
4. Context of Organization
It has to determine organization needs and Expectations and Interested Parities
5. Leadership
Establish role of Top management toward ISMS
6. Planning
Establish Organization Strategic Objects and Risk Management
7. Support
Determined Organizational Resources and Competencies Requirements and Standard Documentation Required
8. Operation
The Information Security Requirements of the ISMS and way to address it
9. Performance Evaluation
Measurement of ISMS Performance
10. Improvement
Identify and act toward nonconformity of ISMS through Corrective Action and Ensure of Continual improvement of ISMS
About The Author
Ahmed Riad, Middle East Business Continuity Leader