Pentesting on Non-Jailbroken IOS Device’s!! PART2
Hello Again! In previous article we had gone thru, basic understanding of Application installation and application traffic analysis, in this part we will look in to reverse engineering and memory analysis.
Link of PART1 | http://goo.gl/IF0JF6
- Reverse engineering – As we have a non-jailbroken iOS device, we are having certain limitations in reverse engineering and decryption of iOS application source code, but still we can perform App Cracking and Traditional Reversing Approach.
Application cracking simply means extracting .ipa package from the application. If you have installed application from the app store, you should go for application cracking technique.
To crack the application, we require the iTools tool. It is a simple application that will help you install iPhone application. Take backup of the application and more important is to crack the application.
Observe in the figure 19 that iTools is showing list of all application with backup and browse function. iTools and iFunbox both the tools are almost similar but major difference is that we can take .ipa backup (app cracking) and runtime system logs and crash reports with the help of iTools tool.
When we click on Backup button the tool is gives two options
- Backup program (.ipa package) and 2. Backup program and document.
We will choose first option as we need to test for app cracking and then reversing with traditional approach.
Figure 20
Observe in the below snapshot that we have cracked the application with .ipa package.
Figure 21
Till now we have only cracked the .ipa package, now we need to proceed with reversing the .ipa package.
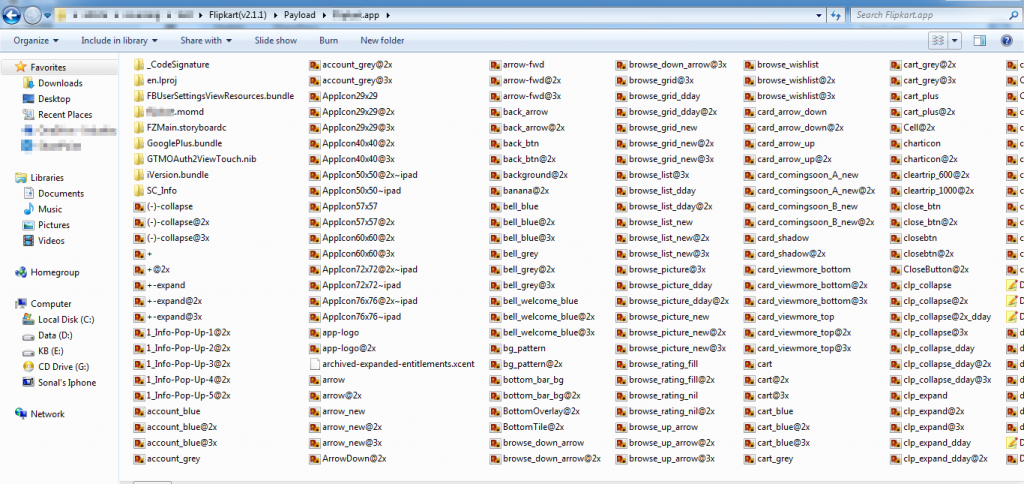
We are going to use traditional approach for this. Now rename application.ipa with application.zip and then extract the .zip file. Below snapshot shows the content inside the Payload- .app folder.
Figure 22
Guys, now we have the content of .app folder inside Payload, what should be the next step??? Just go through different files like plist files, NIB files, localizable strings, mobileprovision file, Appresource files, and License and package info and last but not the least the app binary file.
- Memory Analysis – The iOS application stores data at various locations like Plist files, cache, Coredata and Sqlite files, Keychain, keyboard cache, logs, Cache snapshots etc.
As we are working with Non-jailbroken iPhone device, still we can able to analysis Plist files, Coredata and Sqlite files, logs and Cache snapshot. We are not able to view keychain and keyboard data through non-jailbroken device though.
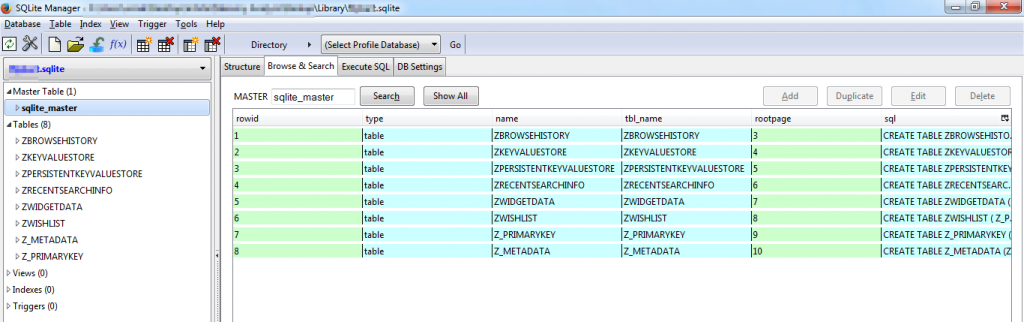
- SQLite storage: SQLite is a cross-platform C library that comes with iOS is a lightweight and powerful relational database engine that can be easily embedded into an application. Unencrypted sensitive information stored in a SQLite file can be stolen easily by gaining physical access to the device or from the device backup
You can view Sqlite files in SQLite Manager
Figure 23
2. Plist file: Property list file is a well-structured binary files which contains the configuration details of .ipa bundle in key value pairs.
This files are used to store configuration information and preferences. List file can be in binary or XML format. They can be easily view in plistEditors. Also you can look-up for weak encoding used in plist file.
Figure 24
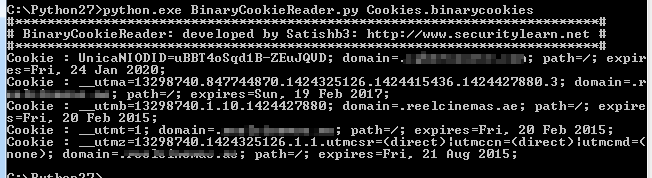
3. binarycookies : This files contain persistent cookies of those application which do not prompt user to login every time. Cookies.binarycookies file is locatde in libary folder of the application. You will find snapshot inside Library/Cookies folder.
This file is not in readable format, so to read this file use below steps.
You must have Python installed on your device. Downlaod ‘BinaryCookieReader’ and copy past inside Python folder. Similary extract application’s Cookies.binarycookies file and copy past inside Python folder too. Open command propt, traverse through the Python folder and run below command
Python.exe BinaryCookieReader.py Cookies.binarycookies
Figure 25
4. Cache Snapshot: When the application goes into the background screenshot has been created with the last state of the application. An attacker can exploit this feature if sensitive information can be recovered through the snapshot storage.
You will find snapshot inside Library/Cache/snapshot folder.
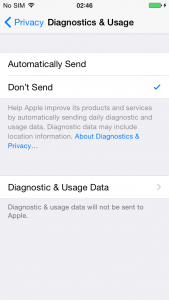
5. Error Logs: In general iOS application writes data, exceptions onto logs for diagnostics and troubleshooting purpose. In iOS the logs are not getting stored in application sandbox that means one application can read logs of another application. Logs can also be viewed by Console App available on App store itself.
The logs are getting stored in device, to view that go to – Privacy – Diagnostics & Usage – Diagnostics & Usage Data.
Below is the snapshot of logs which are getting stored on device.
Figure 26
Figure 27
With the help of iTools we can see runtime system logs too.
Figure 28
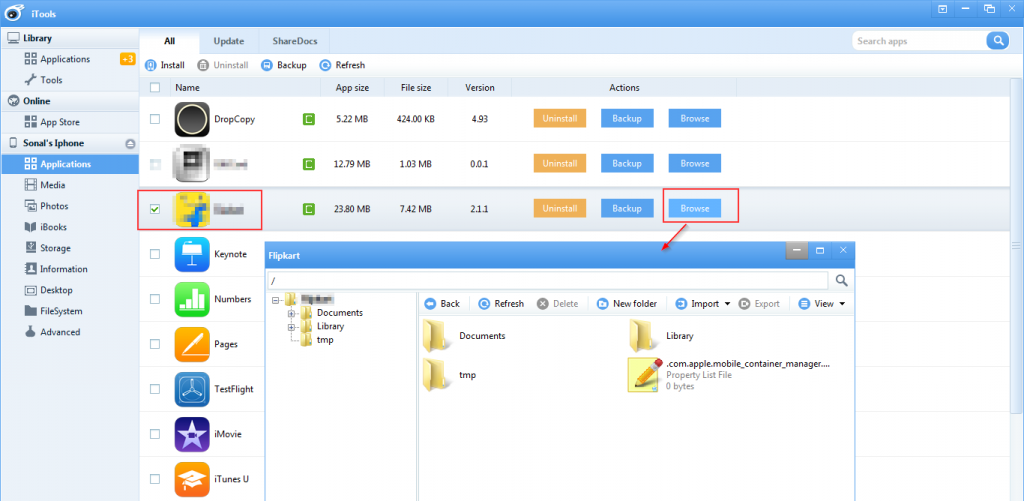
To extract / browse the application data, we can use iFunbox or iTools tool. Here I have used iTools tool to extract the application’s folder. Open iTools on your workstation and connect iPhone device with USB.
As shown in the snapshot below, we can browse through the application folder. Now to analyse the storage we have to copy paste this folders to our workstation.
Figure 29
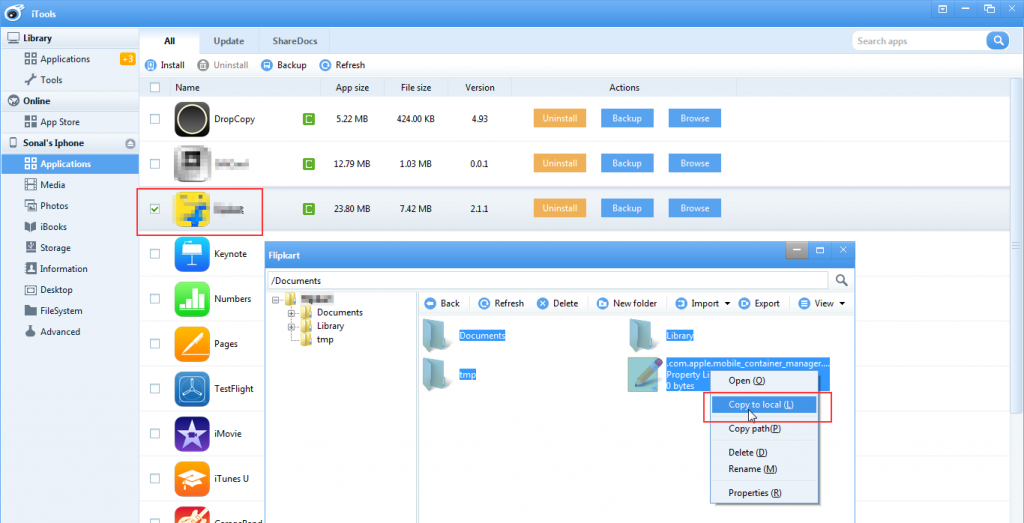
Select the folders to copy and right click on the selection. The iTool will give you multiple options, out of them click on Copy to local provided proper path.
Figure 30
Observe in the below snapshot that ‘document’ folder contains different files including database and json file. Use can use notepad++ or WordPad to open json files.
Figure 31
To view database file, use SQLite Manager, which is a Firefox addon.
Figure 32
Observe in the below snapshot that library folder contains multiple files including Cache, Application Support files, Cookies.binarycookies, Cache snapshot and database folder. You can go though each and every folder and extract the sensitive application data
For more information, refer ‘Insecure data storage’ on – https://www.owasp.org/index.php/IOS_Application_Security_Testing_Cheat_Sheet
Figure 33
And yes here we have successfully performed the iPhone Application Testing on non-jailbroken device. It’s true that for pentesting you should have jailbroken device but if you do not have one then also you can able to perform your task 🙂 and that’s making our life easier.
References:
- https://www.owasp.org/index.php/IOS_Application_Security_Testing_Cheat_Sheet
- https://www.owasp.org/index.php/Projects/OWASP_Mobile_Security_Project_-_Top_Ten_Mobile_Risks
- iTools – http://itools.en.uptodown.com/
- iFunbox – http://dl.i-funbox.com/
- Fiddler – http://www.telerik.com/download/fiddler1
- Burp – http://portswigger.net/burp/download.html
- plistEditor – http://www.icopybot.com/plist-editor.htm
- Notepad++ – http://notepad-plus-plus.org/download/v6.7.4.html
- BinaryCookie Reader – http://securitylearn.net/wp-content/uploads/tools/iOS/BinaryCookieReader.py
- SQLite Manager – https://addons.mozilla.org/en-us/firefox/addon/sqlite-manager/
About The Author
Sonal Gawand, Assistant Manager – Enterprise Risk Services