Reversing FinSpy Mobile Part 1
Introduction
Reverse engineering is a vitally important skill for today’s expert security professional. Everything from reverse engineering malware to discovering vulnerabilities in binaries are required in order to properly secure an organization from today’s ever evolving threats. This series focuses on the static approach to analyse Android malware.
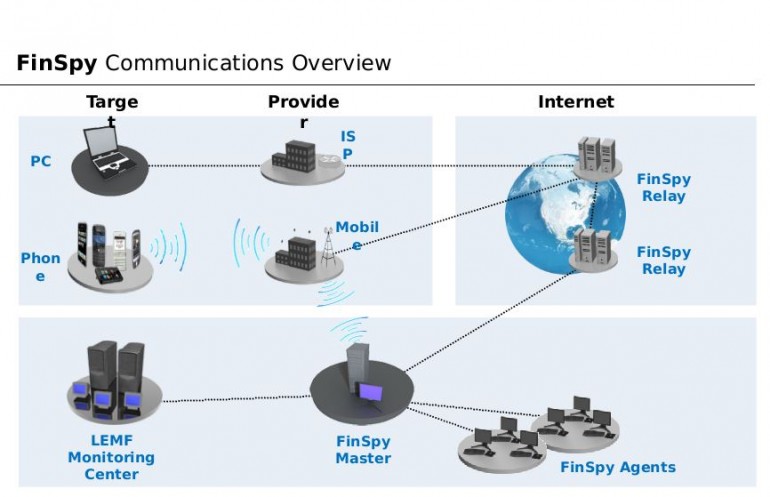
We will be examining FinSpy Mobile that was leaked lately among 40GB of internal documents and source codes of government malware made by Gamma FinFisher. FinFisher is a range of attack tools developed and sold by a company called Gamma Group used by governments worldwide to capture user data.
FinSpy Mobile is the mobile version, compatible with Android, Blackberry, iOS and Windows Phone. All communication with the C&C is encrypted. It can record incoming and outgoing emails, provide location tracking, and provide “live surveillance through silent calls.
Let’s Get Started:
Download FinSpy sample c30ec9c98b15863ccd509126384caca1 from goo.gl/gZyXjM
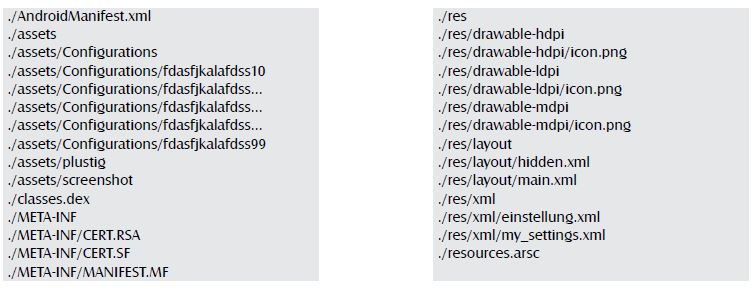
The apk files can be simply uncompressed just like zip files to get their contents that include the manifest file this is usually in the binary format. The archieve file is composed of:
AndroidManifest.xml:
This file this is usually in the binary format and can be converted into a readable file by downloading AXMLPrinter2.
jar and running
java –jar AXMLPrinter2.jar AndroidManifest.xml
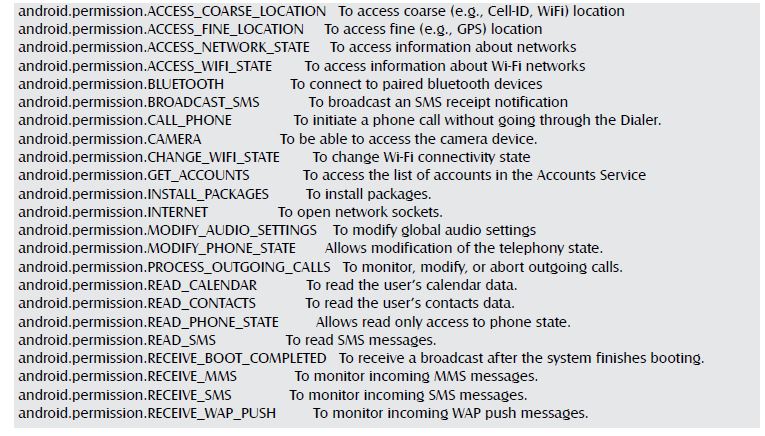
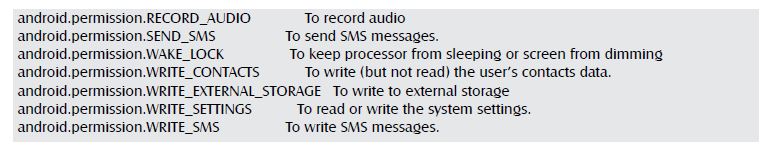
Permissions:
From the decoded xml we could extract these permissions:
Activities:
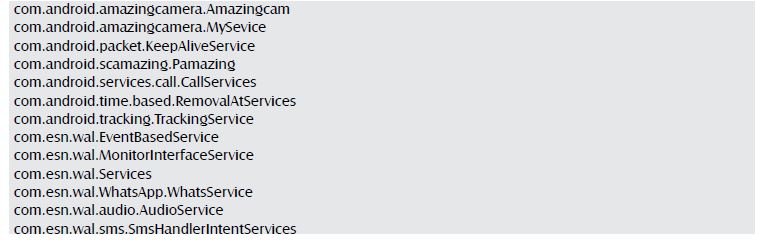
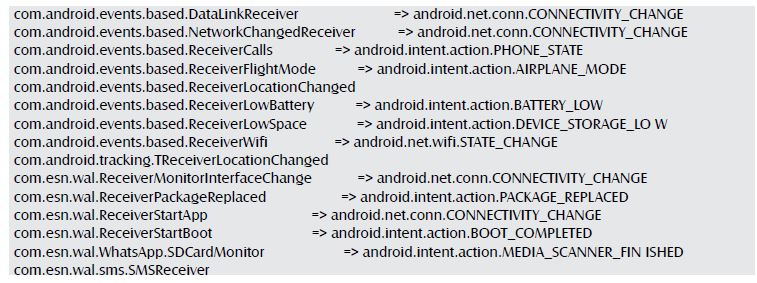
Services:
Services:
Assets:
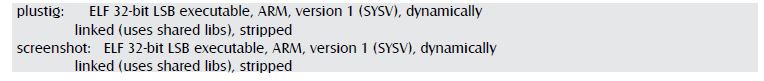
Inside the assets directory there are 2 suspicious files:
Realizing that these files are ELF executables we can guess that their functions, one to capture the screen and the other needs more focus.
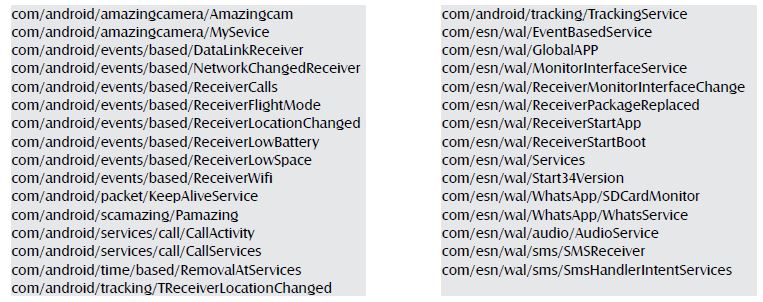
Classes Structure:
Now its time to examine the actual code of this malware. Upon unzipping the apk file we got a classes.dex file which is a dex file that contains the application code. Using tools in android sdk we could get the classes structure by running:
dexdump -h classes.dex | grep “Class descriptor” | cut -d”:” -f2 | cut -c4- | cut -d”;” -f1
From this structure we can setup a classes checklist for our reversing journey
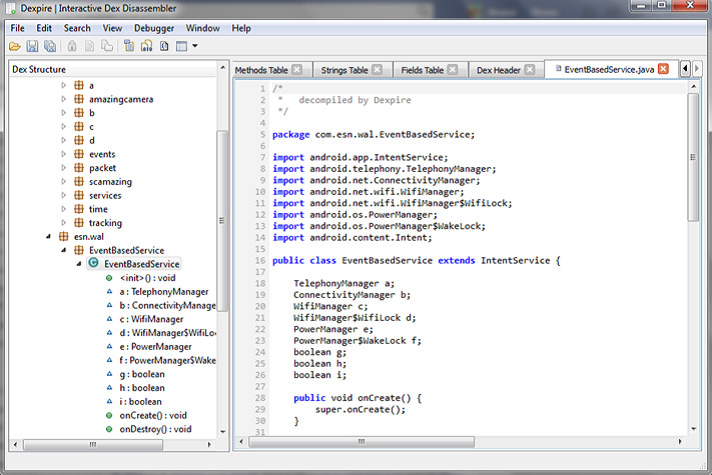
To go on dumping and understanding the application codes, for this purpose I am going to introoduce Dexpire!
Dexpire | Interactive Dex Disassembler:
• Disassembler for the dex format used by Dalvik.
• Directly decompile Dalvik bytecode to Java source code.
• Full APK view, including decompressed manifest, resources, certificates, strings, constants, etc.
For the next parts, we are going to analyze various classes to learn the mechanism of the malware through dexpire.
About The Author

Anwar Mohamed, Mobile Security Researcher