Risk Based Approach To Mitigating Insider Threats in the SDLC
The scope of this article is to discuss the inherent flaws in an SDLC environment that insiders exploit to carry out an insider attack. SDLC process is a development methodology followed by many organizations, and suggests ways of better managing and governing them.
Who is an Insider? An insider is a person who already rests on the trusted radar of the organization, meaning he is already in the trusted network of the organization and has access to information and data which is given to him based on his job roles and responsibilities. A malicious insider on the other hand is a current or former employee, contractor or other business partner who has / had authorized access to an organization’s systems, networks and / or information which he intentionally exceeds / misuses in a manner that negatively affects the confidentiality, integrity and availability of the organization’s information or information systems.
Real life incidents of insider SDLC threats
1. Ration cards created and sold by a desk clerk at the food control office in one country; when the clerk discovers he can actually create one and print them out, a factor overlooked during the requirement analysis. This incident had great potential for turning out into a national security.
2. An employee uses the backdoor that he inserted into his code to gain access to his former company network, alter applications and put them out of business subsequently.
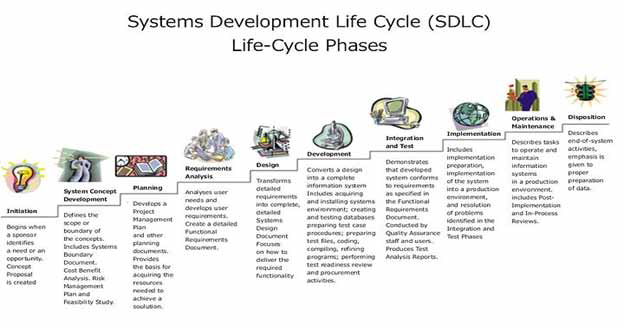
What is SDLC? The Systems Development Life Cycle is a conceptual model used in project management. In general the SDLC process is divided into the following phases and they are :
1. Preliminary analysis
2. Systems analysis and requirements definition
3. Systems design
4. Development
5. Integration and testing
6. Acceptance, installation, deployment
7. Maintenance
The picture attached below describes the above mentioned stages of the systems development life cycle that are divided into ten steps from definition to creation and modification to information systems.
Systems Development Life Cycle ( SDLC) Life-Cyle Phases
The Exploitable Phases
Though multiple risks prevail in all the phases of SDLC, the requirements definition phase, the system design phase, the system implementation phase ,the system deployment phase and the system maintenance phase are the most overlooked ones that are routinely exploited by malicious insiders causing damage.
We shall now look into how to strengthen each of the phases using a risk-based approach thereby engineering reasonable level of assurance into the SDLC process.
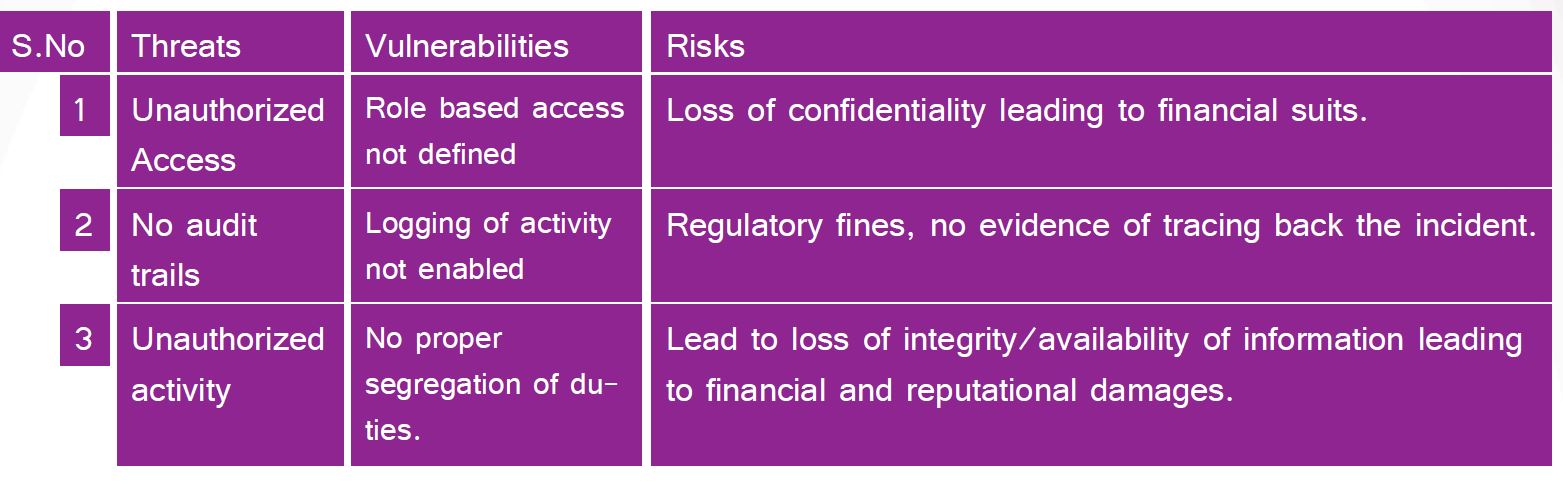
Risk based Requirements definition : Ensures information security team is an integral part of requirements definition phase and define requirements based on risk based methodology and record the risks identified. The following table describes some of the common threats and vulnerabilities captured during the requirements definition phase.
Note: The tables listed here for enumerating the threats, vulnerabilities and risks are intended not to be complete.
System Design Oversights As per statistical data, insufficient attention to automated workflow processes and authorized system overrides, are the most commonly used methodologies insiders use for circumventing rules. Implement suitable controls relating to your organization by performing a risk assessment on the system design phase.
Risks in Implementation Phase/Maintenance phase Probably the two most exploited phases of the SDLC and require greater attention than the above phases. Record the risk related to implementation and maintenance, prioritize and establish timelines to close them off. We illustrate some of the most common threats, vulnerabilities, risks and controls that are applicable to these two phases. Recording efforts and benefits of closing off the risks would help in adding greater value.
Best Practices: The following points described in a nutshell, describe the best practices that can be implemented in an SDLC to minimize the exploit surface.
1. Enforce strict separation of duties and least privileges in all the phases.
2. Log, monitor and audit all employees’ activities, monitoring privileged users’ activities must be done more closely.
3. Use layered approval process mechanisms for implementing and managing source code in production systems.
4. Implement secure backup and recovery procedures.
5. White-list application behavior and monitor suspicious behavior.
6. Educate and continually train employees on secure software coding practices and methodologies.
7. Implement strict password and account management policies.
8. Implement code integrity monitoring tools.
9. Perform continual risk assessments on SDLC.
10. Ensure Infosec team is an integral part in all the SDLC phases.
Conclusion:
Insider exploits are real and need to be managed effectively to reduce the business risks and ensure stakeholders’ interest. It is therefore imperative that organizations of all sizes implement and practice a risk based approach to software development to better strengthen the SDLC program. Last but not least managing insider risks requires executive support, a steady but patient and dedicated approach to effectively mitigate them.
References : www.cert.org
About The Authors
Vinoth Sivasubramanian, A passionate Infosec professional striving to reach the doors of excellence in information security, audit and governance.
Currently working with In space technologies as a system administrator, Kannan is equally passionate on information security and is working towards his CISSP.