Security of Radio Frequency Identification (RFID) Tags
The purpose of this article is to provide an insight to the explosive growth of wireless system using RFID that has led to the other side of concern which is securing the data on the fly. Although, RFID tags are reasonably secure, yet it can still be used against you surreptitiously. Many technical challenges remain in the present age of wireless networks, which we will be discussing in this article.
We have devices incorporated with RFID which can be used by an end user ranging from a parent monitoring baby`s movement remotely, to a government tracking weapons that are in transit. RFID is ubiquitous. Few of the fascinating uses are in casinos for robbery proof chips, loss resistant golf balls, amusement parks for no swipe ticket passes, in humans and animals with their identity data stored, incorporated on smart fitting dress rooms to access the product data and may to find similar alternatives and as anti-theft. Technology has paved way to vastly expand in the wireless space.
Wireless communications over the years has taken a paradigm shift in terms of tremendous growth in communications industry. Now a days cellular phones have become a part of daily life for every individual which adds sophisticated features and technologies over the air. In addition to that wired networks are replaced with wireless sensor networks starting from Home broadband, to remote monitoring using technologies available.
“Every convenience comes at a cost”
RFID
Radio frequency identification is the use of wireless magnetic fields to transmit data, for automatically identifying and tracking tags attached to the objects. The tags contains information stored electronically. The RFID technology has generated much hype in the past few years, out of which the major driver for the development has been tagging physical objects, places & things with a radio chip so they can interface with computers. RFID technology is both hailed as the key to “internet Of Things (iOT)”, and condemned as invasive surveillance technology, and in more extreme circles it is feared as Mark of the beast [1]. As RFID is ubiquitous, our objective is to try to provide an insight on it. Although, RFID tags are reasonably secure. Yet it can still be used against you surreptitiously
Technical Overview
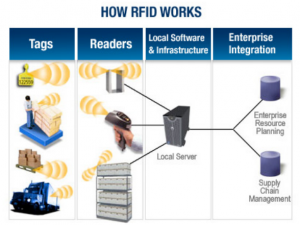
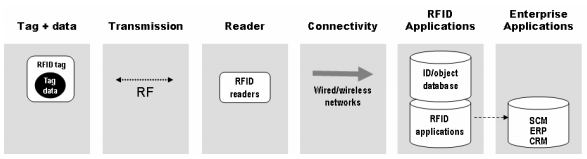
The technical infrastructure part of RFID consists of a radio transponder and a receiver, also known as tag and a reader. Information is stored on a tag and is transmitted to a reader over a radio frequency (RF) connection. The reader in turn connects via a wireless/wired networks to a server hosting the RFID application that makes use of the transmitted data, and in case of a supply chain applications, a middleware manages the RFID data flow between readers and enterprise application.
RFID Tags
Tags contain a microchip and a transponder. The microchip stores data related to the object and the transponder transmits that data to readers. The data is written on the tag along with a unique identifier code at the point of manufacture (factory programming), but can also be programmed by an OEM or end user (field programming).Tags are either passive or active. Passive tags are smaller — about the size of a grain of rice, and getting smaller. They are activated when they enter the range of a reader’s signal. The reader’s antenna sends power to the transponder, activating the data stream. Passive tags are much smaller in size and memory, than active tags and are cheaper to manufacture.
RF Connection
Tags transmit data to readers over different radio frequencies, depending on the application needs. RF frequencies are dividing into several bands including low frequency (LF), high frequency (HF), ultra-high frequency (UHF), and microwave. Passive tags transmit at all frequencies while active tags transmit at higher frequencies only. The exact frequency that can be used within the various bands, as well as power (output) levels, are controlled by the regulatory body of each country. Each frequency varies in terms of regulation, performance, size and cost of the associated technology.
MIFARE RFID hacks
One of the most common RFID Cards is the MIFARE Classic, produced by NXP Semiconductors
The MIFARE Classic card family, which covers the public transport, access management, loyalty cards etc., are passive and fully compliant with ISO/IEC 14443 Type A.
For cryptographic purposes, the MIFARE Classic cards use the CRYPTO1 cipher. This is a proprietary encryption algorithm, which was developed by NXP, based on the Hitag2 algorithm. CRYPTO1 is used in HITAG RFID systems and the details of the algorithm were kept secret by the manufacturer. The approach is called “Security through Obscurity”. Eventually, the hackers Nohl and Plötz from the Chaos Computer Club (CCC) in Berlin discovered the algorithm by reverse engineering.
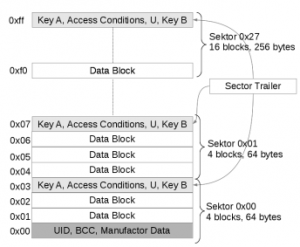
The MIFARE Classic card 1k chip has 1k EEPROM memory, which is separated in 16 sectors with 4 blocks, each containing 16 byte making a total of 64 blocks and the 4k version offers 4k of EEPROM memory, separated in 256 blocks, where 32 sectors have 4 blocks and additional 8 sectors having 16 blocks. The first block contains the unique identification number (UID) of the card as well as some vendor specific data which is write protected. On the last block of each sector, access keys and access rules can be found, which does not intend to store user data.
Before any memory operations are allowed on a sector, a reader has to authenticate itself for this sector. Hence, the sector trailer uses secret keys containing A and B which are used for the authentication. The access conditions located in the same block specifies memory operations allowed on the sector. The sector trailer itself has specific access conditions. The key A is never readable, key B can be configured readable or non-readable. If it is declared as readable, only key A can be used for authentication and key B is used to store data. There is also the single byte U, which has no defined purpose. The data blocks are used to store information for the application. For example, a cafeteria card could hold the name of the owner plus the current balance of the card.
MI fare Classic 4k register & Blocks structure
Algorithm used for encryption
From the re-engineering of the chip, it was known that the crypto logic had only one input and the UID was used as input as well as the key and those two had to be connected somehow, suspecting the connection method was XOR. To prove this theory, the first bit of the UID as well as the first bit of the key were flipped. If they were connected via XOR, this should still result in the same value. As confirmation for the team, the card responded again, which meant the theory via XOR connection was correct. With testing, they found out that the first five bit of the UID and the key are connected directly, which means the nth bit of the UID is connected to the nth bit of the key. For the other bits, the relationship is different. Another discovery made during testing the radio protocol was that the algorithm uses a pseudo random number generator (PRNG), which is realized with a linear feedback shift register (LFSR).
Along general lines, a LFSR creates a sequence of numbers which appear random. It always starts with the same number and moves to the next number with the same frequency. Also, the nth number of one LFSR will always be the same. Challenged faced with using LFSR in passive RFID tags is, the cards relied on power supply from the reader. Inferring, every time the card is removed from the reader, it is out of power and the LFSR starts again with its initialization sequence as soon as it is provided again with energy, sending the same numbers in the same frequency as the last time. This was proved in an experiment of the CCC. They put the card next to the reader and switched on the reader. As a result, it always needs approximately the same time after the card is supplied with energy and starts creating random numbers, that the reader starts communicating. Within this experiment, they had the same random values of the LFSR in 12 out of 27 attempts.
With the work done by the CCC, it is possible to present the CRYPTO1 algorithm of the MIFARE Classic cards in detail. The algorithm consists of a LFSR and a function f(x). In the beginning, the shift register is initialized with the secret key. Afterwards, the PRNG creates 32 bit and XORs them with the UID. This string will then be shifted into the state of the shift register. The created random value is also used for the challenge response protocol between reader and card. At this point, the encryption is activated and all incoming and outgoing bits are XORed with the key stream. The shift register itself is only used for bits containing data or cyclic redundancy check (CRC) values. For encrypting parity bits, a bit of the key stream
which was already used for a data bit is used again. Each cycle, the function f(x) computes one bit for the key stream out of 20 bits it gets from the LFSR. The 18 taps of the LFSR are used to fill the first register bit on each shift. For this, the taps are connected linearly, implying the update function does not contain any non-linearity, which means that when one of the shift values is given, it is possible for an attacker to calculate previous values as well as upcoming values. With today’s knowledge of crypto systems, this can be considered a serious weakness.
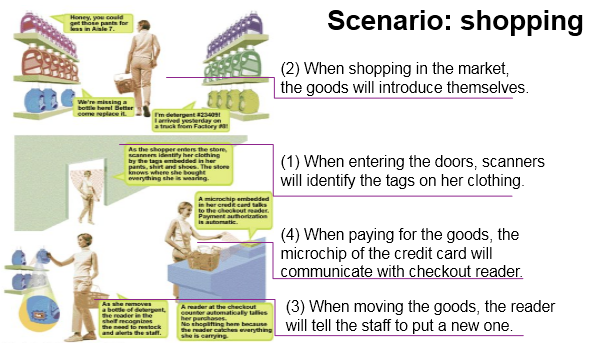
Future examples of RFID usage in internet of things:
In future we can see each object in the real world will be tagged with RFID for monitoring, tracking and maintenance purposes. Below figure explains once such scenario:
Security and Privacy issues with RFID:
At this point of time we see all our sensitive information is being communicated over internet and is stored in different devices, all these devices and communication network and devices are using RFID’s. We can sense our data which is at risk, let see some of the security and privacy issues which must be considered to secure the data by both organizations and individual:
TAG DATA
RFID tags are considered “dumb” devices, they can only listen and respond, no matter who sends the request signal. This brings up risks of unauthorized access and modification of tag data. In other words, unprotected tags may be vulnerable to eavesdropping, traffic analysis, spoofing or denial of service attacks.
We will look at each of these in turn:
Eavesdropping (or Skimming)
Radio signals transmitted from the tag, and the reader, can be detected several meters away by other radio receivers. It is possible therefore for an unauthorized user to gain access to the data contained in RFID tags if legitimate transmissions are not properly protected. Any person who has their own RFID reader may interrogate tags lacking adequate access controls, and eavesdrop on tag contents. Researchers in the US have demonstrated a skimming attack on an RFID credit card, through which credit card information, such as the cardholder’s name and account information, could be skimmed if not properly encrypted.
Traffic Analysis
Even if tag data is protected, it is possible to use traffic analysis tools to track predictable tag responses over time. Correlating and analyzing the data could build a picture of movement, social interactions and financial transactions. Abuse of the traffic analysis would have a direct impact on privacy.
Spoofing
Based on the data collected from eavesdropping or traffic analysis, it is possible to perform tag spoofing. For instance, a software package known as “RFDump”, that runs on a notebook computer or personal digital assistant, allows a user to perform reading or writing tasks on most standard smart tags if they are not properly protected. The software permits intruders to overwrite existing RFID tag data with spoof data. By spoofing valid tags, the intruder could fool an RFID system, and change the identity of tags to gain an unauthorized or undetected advantage. One example is trying to save money by buying expensive goods that have had their RFID price tags spoofed to display cheaper prices. By combining the two capabilities of eavesdropping and spoofing, a replay attack is possible where an attacker can “query a tag, receive the information it sends, and retransmit this information at a later time”.
Denial of Service Attack
The problems surrounding security and trust are greatly increased when large volumes of internal RFID data are shared among business partners. A denial of service attack on RFID infrastructure could happen if a large batch of tags has been corrupted. For example, an attacker can use the “kill” command, implemented in RFID tags, to make the tags permanently inoperative if they gain password access to the tags. In addition, an attacker could use an illegal high power radio frequency (RF) transmitter in an attempt to jam frequencies used by the RFID system, bringing the whole system to a halt.
RFID READER INTEGRITY
In some cases, RFID readers are installed in locations without adequate physical protection. Unauthorized intruders may set up hidden readers of a similar nature nearby to gain access to the information being transmitted by the readers, or even compromise the readers themselves, thus affecting their integrity. Unauthorized readers may also compromise privacy by accessing tags without adequate access controls.
As a result, information collected by readers and passed to the RFID application may have already been tampered with, changed or stolen by unauthorized persons. An RFID reader can also be a target for viruses. In 2006, researchers demonstrated that an RFID virus was possible. A proof-of-concept self-replicating RFID virus was written to demonstrate that a virus could use RFID tags to compromise backend RFID middleware systems via an SQL injection attack.
PERSONAL PRIVACY
As RFID is increasingly being used in the retailing and manufacturing sectors, the widespread item-level RFID tagging of products such as clothing and electronics raises public concerns regarding personal privacy. People are concerned about how their data is being used, whether they are subject to more direct marketing, or whether they can be physically tracked by RFID chips. If personal identities can be linked to a unique RFID tag, individuals could be profiled and tracked without their knowledge or consent. For instance, washing clothes tagged with RFID does not remove the chips, since they are specially designed to withstand years of wear and tear. It is possible that everything an individual buys and owns is identified, numbered and tracked, even when the individual leaves the store, as far as products are embedded with RFID tags. RFID readers can detect the presence of these RFID tags wherever they are close enough to receive a signal.
Way to tackle the security risk in RFID’s:
Things in RFID which we have to address for security risks are:
- Tag Data Protection
- Reader Integrity
- Personal Privacy
Conclusion
While the use of RFID technology is increasing across a range of different industries, the associated security and privacy issues need to be carefully addressed. Because RFID tags come in different flavors, there is no overall, generic RFID security solution. Some low-cost passive and basic tags cannot execute standard cryptographic operations like encryption, strong pseudorandom number generation, and hashing. Some tags cost more than basic RFID tags, and can perform symmetric-key cryptographic operations. Organizations wishing to use RFID technology need to therefore evaluate the cost and security implications as well as understand the limitations of different RFID technologies and solutions.
References
http://en.wikipedia.org/wiki/Radio-frequency_identification
http://www.proxclone.com/
http://www.alientechnology.com
http://www.rfidjournal.com/case-studies
http://www.sos.cs.ru.nl/
http://www.iot-a.eu/public/public-documents/d6.4
http://www.rfidjournal.com/articles/view?1338
http://www.nytimes.com/2006/10/23/business/23card.html?pagewanted=1&_r=1
About the Authors
Steevan is a Certified Ethical Hacker with over 5 years of experience in software development and information security. He has extensive experience in security domain including penetration testing, application vulnerability assessments, Hardware security, web services security, Network vulnerability assessments, Android and BlackBerry mobile application testing.
Vikram is a senior consultant in KPMG Global Services – Cyber Security practice. He has close to 4 years of experience in enterprise application security, Hardware security and information security. He is one of the gadget lover and his passion resides in Mobile security.