Types of SQL injection
SQL injection is probably the most dangerous known web attack. Sometimes it could lead to remote code execution that gives the hacker a full control of the system. In this article we will talk about SQL injection types.
1- Error based SQL injection :
In this case the database simply the application sends back the database errors directly to the user. Sometimes this happens because the developer of the website didn’t turn off debugging on the server.
Injection : or 1=user()–
Response : Syntax error converting the nvarchar value ‘ahmed’ to a column of
data type int.
From this example you can see that the user name ‘Ahmed’ which is the output of the user function is sent back in the error message. The attacker can also retrieve other information from the database.
Tip : If you don’t have a good experience with databases and what useful functions you can go to this website which will give you a cheat-sheet for SQL injection :
http://www.pentestmonkey.com
The exploitation of the error based SQL injection is fairly straight. For example the attacker can make an invalid comparison between an integer and the data he needs to extract. To make things clear lets see an example (Assuming MS SQL database).
2- Union based SQL injection :
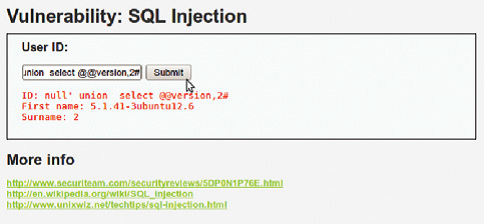
Union based SQL injection as the name suggests abuses the union operator. The basic idea is to append the data that the attacker wants to a table that is already displayed in the page. See this example from DVWA (A vulnerable web application created for training hackers and to be used in educational classes). Inject this code inside the id parameter :
null’ union select @@version,2#
The database will simply display the results in the search query as you can see in the following image
Another thing to notice here is tha the database version reveals also the operating system information which is something that should be disabled by the database administrator.
3- Blind SQL injection :
This is the hacker’s last choice since it take a fairly long time. I worked once with blind SQL injection and to be honest it wasn’t a pleasant experience it took me all the night to successfully exploit this vulnerability. Even with some tools available like sqlmap, sometimes you need to write your own scripts to successfully exploit blind sql injection. Now let’s talk about how blind sql injection works. In this case the database will not give you any output not even an error message so you need to find another way to retrieve data. This can be done by asking database questions like “if the first letter of the user name is not an a then wait for 10 seconds” which in the database language can be this query: http://[site]/page.asp?id=1; IF (ASCII(lower(substring((USER),1,1)))>97)WAITFOR DELAY ‘00:00:10’
the above query will wait for ten seconds only if the first letter of the user name is not “a” then you have to do this with all other letters of the user name. Then you move to the password hashes and so on. This makes it obvious that using automated tools or scripts is fundamental otherwise it will take you days to retrieve only the basic information.
About The Author

Fady Osman, Information Security Consultant at ZINAD