What After HACKING TEAM LEAKS!
Humans can increase their degree of freedom through knowledge. Abu Hamid al-Ghazali says: “Man has choice in what he knows and is choice-less and externally controlled in what he doesn’t know”, which means that whenever his knowledge expands, his freedom increases. A Quote By Dr. Mustafa Mahmud
Abstract
It’s No Wonder that all the world is searching and seeking to be secured , after the news of HACKING TEAM , hacked and Leaked information ,Documentation and Source code of their program “Remote Control System”, I myself was one of the people who are interested in this topic to understand and gain knowledge, but what After That we will be discussing in this article .
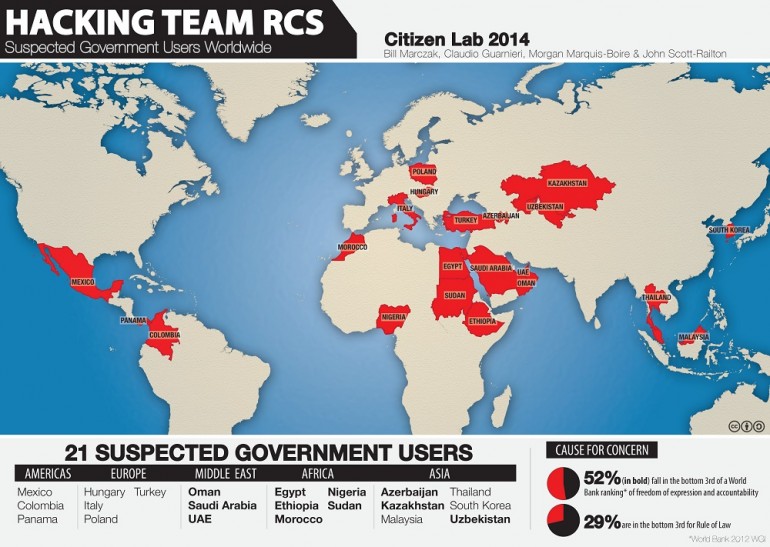
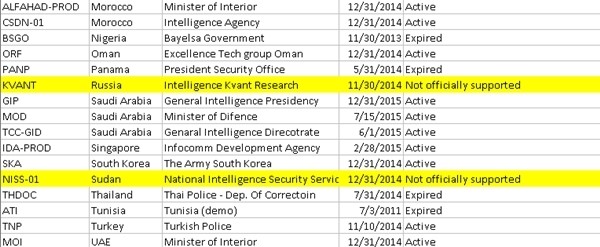
Hacking Team currently has, based on internal documents leaked by the attackers on Sunday evening, customers in the following locations:
Egypt, Ethiopia, Morocco, Nigeria, Sudan Chile, Colombia, Ecuador, Honduras, Mexico, Panama, United States Azerbaijan, Kazakhstan, Malaysia, Mongolia, Singapore, South Korea, Thailand Uzbekistan, Vietnam, Australia, Cyprus, Czech Republic, Germany, Hungary Italy, Luxemburg, Poland, Russia, Spain, Switzerland, Bahrain, Oman ,Saudi Arabia, UAE
The list, and subsequent invoice for 480,000 Euro, disproves Hacking Team’s claims that they have never done business with Sudan. According to Human Rights Watch, Sudanese security forces have repeatedly and violently suppressed protestors demonstrating against the government, with more than 170 killed in 2013.
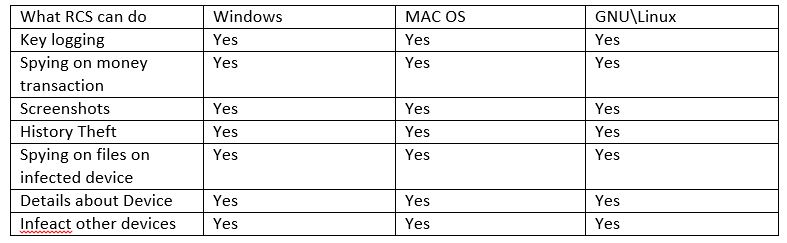
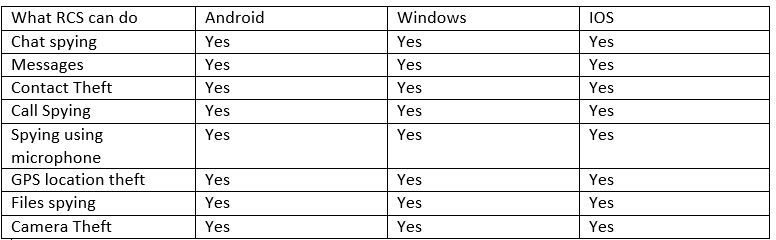
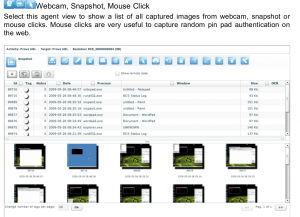
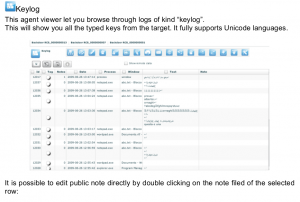
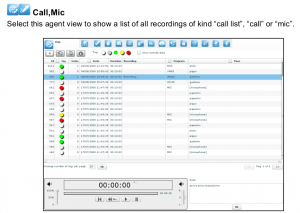
What Can Remote Control System do
Systems that RCS can Act with(Patch them):
- Windows
- GNU Linux
- MAC OS
- Android
- IOS
- Windows phone OS
- Blackberry phones
Windows –MAC OS – GNU/Linux
RCS can’t patch backdoors to GNU/linux Distributions and MAC OS as to work permanently, the patching is done when the Operating system restarts , but its enough time to sniff the data and cause damage.
Patching the backdoors can be done by (Including the backdoor inside another program-using program vulnerabilities-injecting code and malware in the network).
- Password and session theft from chrome-Firefox-IE
- Works on windows (8 -8.1 -7 -2008-2012)
- Works on linux (Debian6 -7 – Fedora17 -20 – Ubuntu )
- Works on MACOS (10.8 -10.9 -10.10)
- Keynoting
- Webcam shots
- Screenshots
- E Coins theft
- Geo-location
- Skype Contact theft
- Email Theft
Android-IOS-Windows Phone – BlackBerry
RCS can’t patch backdoors to Mobile (Android-IOS-Windows phone-BB) as to work permanently, the patching is done when the Operating system restarts, but its enough time to sniff the data and cause damage.
Patching the backdoors can be done by (Including the backdoor inside program-using program vulnerabilities- QR Codes or URL).
Its true that RCS is a Target Surveillance not a dragnet Surveillance , so it attacks specific people ,so it will not affect privacy unless you are someone the governments want to know everything about you, but we could say that this is not everything , maybe it can be used in a way or another.
So What Now?
What can be done to feel secure and free again is merely some ideas needs to be implemented to gain results :
- Increase Security Knowledge ,spread the security wise among people.
- Develop security professionals , there are many security Experts but why not increase the numbers ,allowing us to act and do more.
- Develop our own OS, and
- Use DEEP WEB ,
- Make Deep Web of our own.
About The Author

Khaled Alaa, Information Security Engineer at Raya Data Center