“Wireless Security Threats are LIVE in your Network”
I can imagine that some of the readers are saying, thanks god, I have not allowed Wi-Fi in my network so, I’m secure and I can flip the paper BUT, wait, unfortunately YOU ARE under Wireless threats even you’ve chosen not to install it and even if you believe that Encryption is enough for protecting your existing Wireless Network.
Actually, we are living in an era that connectivity and number of communication channels is dramatically increasing, everybody is bringing his own Device and/or Technology inside the corporate (BYOD/ BYOT Phenomena) and would like to use that in Business, everybody needs to be online with hiscorporate email through his Smart Phone and/or Tablet and asking IT to provide that and commonly Security is sacrificed for Functionality or usage in such cases.
One of the technologies that mostly used by these Devices is Wireless LAN or Wi-Fi and organizations are trying to entertain the connectivity by having such great technology but another aspect always over sighted which is Security. Although, you have allowed a set of your users to be connected to your network m and saved a lot in Passive Work, Cabling, Management of Floor switches, but your security posture is jeopardized, Security is all about Trade-off and how you choose
between functionality and Security and ease of use.
What makes the matter more complex is whether or not you choose to install a WLAN, you are vulnerable to some kind of Wireless Threats, but how & what kind of threats you are talking about here….. so, let’s have some scenarios to be more practical.
Scenario #1; you don’t have a wireless network at all, but one of your employees who have a laptop or having a wireless card, that can be easily purchased from local market by 20-30 USD, and trying to connect to your neighbors network which they have an open network and they have a good internet speed, good advantages that hackers usually used to offer to victims, and he is sending a sensitive documents or internal email through this neighbor’s network, so he typically leaked some data/information outside the organization without IT/ Information Security Departments doesn’t know about that at all, but the organization will know if these information is related to their corporate advantages and if you are a popular company or a bank you will be heading a next day’s news.
The above threat is widely known as “Connecting to Un-Authorized External APs”
Scenario#2; you have a wireless network and its SSID called “XYZ” which is your company name, and one hacker sits simply outside your network inside his car and published a wireless network via his Window 7 Machine called the same name “ XYZ”, but you were that expert and you have encrypted your legitimate “XYZ” by WPA2, but hacker makes it Open with internet access, so, users starts to connect to un-legitimate “XYZ” as its open and have open internet connection – with no-proxy – and starts to leaks and hacker starts to sniff and you know the rest of the story. The above threat is widely called “Honeypots or Wi-phishing”
Scenario#3; you have a wireless network, and one of your employees purchased an Access Point – costs 20-30 USD & maybe less- and plugged it into Switch port and spread your network outside the organization, and you know the rest. The above threat is widely called “Rogue AP”
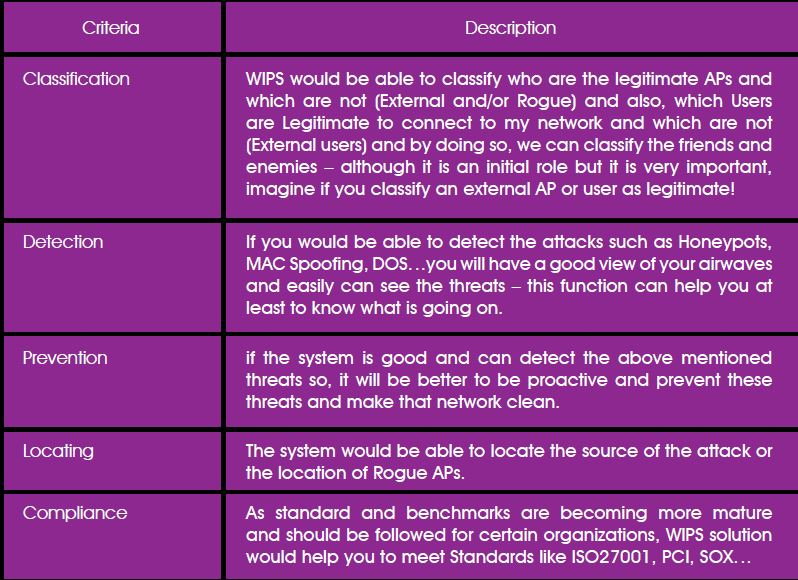
The above three scenarios are only examples and there are a lot of scenarios with its associated threats such as, WLAN Denial of Service (DOS) or Distributed DOS (DDOS) where hackers will try to make your network down and affects availability of the network, Ad-Hoc Connections is also one of the wireless attacks where users connects to each other’s and share sensitive information and you won’t have any idea about such communication, Misconfigured Access Point which relates to the IT/IS operation of the organization which could make your network vulnerable through missing one encryption parameter in a single Access Point , MAC-Spoofing which widely used in open encryption network with Web Authentication.
The below figure is showing the attacks that widely known for wireless; And as you see by not having a WLAN or applying a good encryption only will not make you ahead of these threats, which makes your role harder but don’t forget that WLAN brings a lot of advantages and it is the time to pay the price. The Good news that most wireless vendors are aware of that and they are trying to implement some techniques in their solutions to be ahead of these threats, some of the vendors are implementing that as an integrated solution such as, Cisco, Juniper Trapeez, ARUBA… and some trying to protect organizations by having an overly security solution such as AirTight, Motorola AirDefense, AirMagnet…
Actually vendors are trying to implement WIPS – Wireless Intrusion Prevention System to monitor the airwaves & detect wireless threats and to be able to classify, detect, prevent & locate
wireless threats.
It’s Paramount to mention that neither a single product nor Technology would help you to protect yourself against such threats, its Security Strategy, collaborative defense approach and applying Security Best Practices would do but from the other hand, WIPS can help you to complete the Defense Policy and stay ahead of such threats. The WIPS solution usually should do the following as listed in the below table, and if you would to build your own WIPS you should make the below as your minimum requirements coupled for sure with your business requirements;
So in summary, living in a challenging era like today would have a lot of security challenges that should be looked carefully and organization should look at how the evolving communication channels and/or technologies are affecting the organization security posture and try to update its Security strategy and think thoroughly in Confidentiality, Integrity and Availability and how that can be applied in Pepole, Process and Technology.
About The Author
Mohamed Enab, CISSP, CCSP, SSCP