DLL Hijacking
Introduction
In this article I would like to discuss DLL Hijacking attack, due to its impact and ease of exploit. The article we will go through the concept of DLL Hijacking, then how to exploit systems using DLL hijacking in simple steps, then will introduce a demo of exploiting a vulnerable program.
DLL & DLL Hijacking
Let’s first understand what is DLL and what is it’s usage,a DLL is an abbreviation for Dynamic link library. DLLs are libraries that contain shared functions used by executable files at runtime, as an example an application that displays a MessageBox that says “Simple MessageBox” , what actually happens inside this application that it loaded a built-in DLL called “User32.dll” inside this DLL it executes a function that is calledMessageBoxA (eg.MessageBoxA(0,“Simple MessageBOX”,MB_ OK“);(see Figure below).
The flow that the application takes to load a DLL at runtime is first the windows try to locate the DLL location, to achieve this the windows searches a well-defined set of directories in a particular orderas described in DLL Search Order, based on that logic If an attacker gains control of one of the directories on the DLL search path, it can place a malicious copy of the DLL in that directory, This is called DLL Hijacking so If the Application does not find the legitimate DLL before searching the compromised directory, it will load the malicious DLL. Like this we can use DLL Hijacking to perform remote code execution or even Privilege escalation if the vulnerable program runs as administrator
DLL Hijacking in a few steps
So what are the steps to perform a successful DLL hijacking attack?.
1.Targeting a certain application.
2.Monitoring DLLs that are loaded by this application.
3.Find the search order for the DLLs
4.Target a DLL where you can put your malicious DLL to run before the legitimate DLL, or better Target an unavailable DLL for example VulnDLL.dll .
5.Find out which function this DLL is executing for example executeme()
6.Write a code you want to be executed when the DLL loads and put the code inside a function executeme().
7.Compile the code to shared library and name it VulnDLL.dll
Let’s Crack Some Systems
in this part I’ll show a Demo on how to perform a successful DLL Hijacking Attack.in this Demo we will target tftp32.exe application. you can find a list of applications reported to be vulnerable to DLL Hijacking On the following link: http://www.exploit-db.com/dllhijacking- vulnerable-applications/
So let’s start the fun part!!!
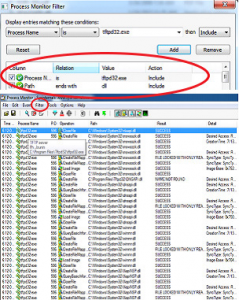
as discussed we need to get the list of DLLs that get loaded in runtime when the application starts, this can be achieved easily using Procmon.exe tool, so just start your application and add the following filter in procmon,
•Process Name is tftp32.exe
•Path ends with DLL
These filters will get us all entries related to the process tftp32.exe and all DLL files it’s trying to load so now lets target a DLL
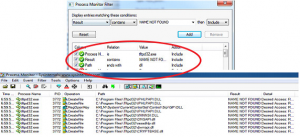
we can notice in the results column in procmon that there are columns that state “NAME NOT FOUND”, which means that the system is trying to load the DLL but it can’t find it so these are the perfect DLL to target. So lets add another filter
•Results Contain NAME NOT FOUND
Great now we have a smaller list of targets To choose from, any one of these DLL’s can Be vulnerable to DLL Hijacking so lets pick One, for example “IPHLPAPI DLL”
As discussed the application load the DLL to execute a function existing inside this DLL , so now the next step, we have to figure out which function inside this DLL the application needs, with a little bit of reversing using IDA we can obtain this information, I was able to get the function name using static reversing only, in some other cases you will need to reverse the application in run time to obtain the function name, now lets start reversing.
In case of this application it will be very trivial just load the application with IDA
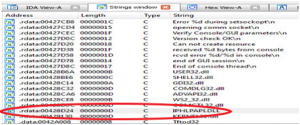
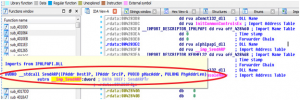
•open the “strings” subview and search for the Target DLL IPHLPAPI DLL(see Figure below)
•double click on it so it gives you reference to where it’s used in the assembly code (see Figure below).
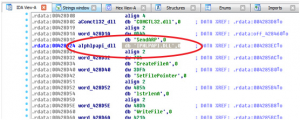
we can see that a string was defined by the value “IPHLPAPI.DLL” (db ‘“IPHLPAPI.DLL”) . we can see where this string value is used in the code . if we double clicked on DATA XREF: .rdata:004283EC (see figure below).
On the address where the target DLL is referenced we can find that it import a function called SendARP(),we don’t need to know what this function does, we only need to know it’s name.
So as you have all guessed by now the only step remaining is
•Write a code we want to get executed when the vulnerable application run
•Insert this code inside a function called SendARP(),
•Compile this code into a shared library(DLL) and call it IPHLPAPI.DLL” ,
• Insert it in a path where the system looks for it and we will get our self a back door or a remote code execution on the system.
Just to demonstrate I will write a code that open a MessageBox that displays to the user “DLL Hijacked”, below is a code snippet.
Simple explanation for the code is that when the DLL is called (DLL_PROCESS_ATTACH) , execute SendARP() Function. Finally eachtime the program run this function will get executed.
Instead of just opening a message Box you can use this vulnerability to get the victim reverse connect to you and probably get a permanent shell or backdoor on the box ,or even better you can get a Meterpteter session if you insert the right code inside SendARP() function.
Summary
So now we know how to exploit DLL hijacking vulnerabilities, what about remediating them? In a few points let’s see some recommended solution
From development perspective
1.always use fully specified Path name in the C functions LoadLibrary() or LoadLibraryEX()
2.Consider removing the current directory from the standard search path by calling the C Function SetDllDirectory with an empty string (“”).
From System hardening prespective
3.Make sure the registry key SafeDllSearchMode value is set to ‘1’ this places the user’s current directory later in the search order (HKEY_LOCAL_MACHINE\ System\CurrentControlSet\Control\Session Manager\SafeDllSearchMode)
As a matter of fact the below is not really a complete solution as for some reason Microsoft has a feature “DLL Local Redirection”, where if an application name is abc.exe and you created a folder called “abc.exe.local”, this will force the application to search all DLL it needs from this local folder first even if it was specified using LoadLibraryEX(“Path to DLL”) .So if you think of it, this can make all applications vulnerable to DLL hijacking Attacks.
About The Author
Khaled Sakr, Information Security Engineer at Security-Meter