Neurevt bot Malware Analysis
Introduction
Neurevt bot “Beta Bot” has a lot of functionalities along with an extendable and flexible infrastructure. Upon installation, the bot injects itself into almost all user processes to take over the whole system. Moreover, it utilizes a mechanism that makes use of Windows messages and the registry to coordinate those injected codes. The bot communicates with its C&C server through HTTP requests. Different parts of the communication data are encrypted (mostly with RC4). Many components cover a large number of the most popular malicious functionalities, including downloading malware, DDoS attacks, and credentials stealing.
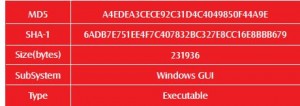
File Identification
Information Gathering
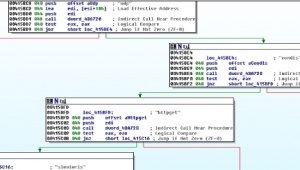
The following snippets found during this phase show some capabilities for real “Beta bot” for sale:
Neurevt Behavioral Analysis
1] Malware sets the below registry “ShowSuperHidden” to zero (default=1) to hide with protected operating system files:
HKU\S-1-5-21-3506987661-2624146946-3848342493-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced\ShowSuperHidd
en: 0x00000000
2] Betabot creates winlogon0 folder and copies itself with random named under the following paths:
C:\ProgramData\winlogon0\[random_name].exe
C:\Users\All Users\winlogon0\[random_name].exe
First path will be used by malware for persistence as shown by autorun tool output .
3] System Monitoring:
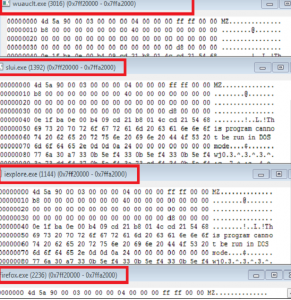
Process neurevta4e.exe was started by explorer.exe
Process “[random name].exe” was started by parent process “neurevta4e.exe”
Process wuauclt.exe was started by “[random name].exe” and tries to connect to the malicious domain 7obby.com
4] By exploring memory of running processes with “RWX” protection, it has been observed that malware copied itself to the same memory area “0x7ff20000 0x7ffa2000” for many processes to keep persistence except explorer.exe infected memory area “0x7ff10000-0x7ff92000.
Infected processes are neither system authority processes nor services processes; they are all under the same user account running the infected processes as shown below:
5] UserMode System Call hooking:
The sample uses “KiFastSyatemCall” function which will be used at the user mode system call hooking.For more information about this system call hooking technique, check the following link:
http://www.malwaretech.com/2014/06/usermode-system-call-hookingbetabot.html
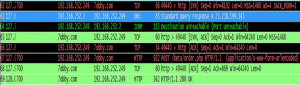
6] Network Monitoring:
Injected process wuauclt.exe “PID=700” tests connection by query “www.update.microsoft.nsatc.net” Then, wuacult PID=700” establishes connection to “7obby.com” with the upcoming fake user agent (malware uses fake popular user agent to avoid network layer detection): Mozilla/5.0 (compatible; MSIE 7.0; Windows NT 5.2; WOW64; .NET CLR 2.0.50726)
The below screenshot shows that malware sends encrypted messages to command and controller stored at ps0, ps1, cs0, cs1, cs2, cs3
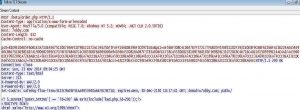
svchost.exe process tries to resolve the following domains but it could not find such names
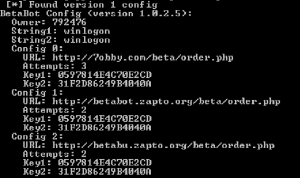
7] Configuration Extraction: The configuration section of the bot, this section is encrypted inside the bot and decrypted while the bot is running could be extracted using betabot-re script published at this link https://github.com/KenMacD/betabot-re
The output shows Betabot version=1.0.2.5, owner is as shown “792476” primary malicious domain “7obby.com” and its backup domain betabot.zapto.org and betabu.zapto.org and keys used for encryption.
Malware Capabilities
The following shows some of the malware capabilities:
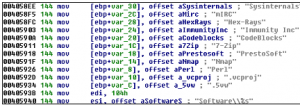
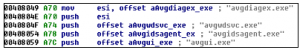
Gathering Information about softwares: Neurevt detects and gathers information about many softwares specially security and gaming softwares through open registries keys .
Detect many antivirus products:
The following screenshot is an example of AVG antivirus processes detected by sample
Privilege detection and escalation:
RtlQueryElevationFlags: A pointer to a variable that receives the elevation state
It tries to escalate privileges through fake errors with different languages to escalate privileges using “UAC” User Access Control Message feature that could appear as shown at below screenshots:
Credentials Stealing
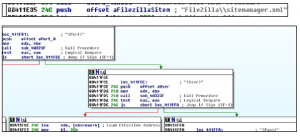
Neurevt tries to steal FTP software credentials an example screenshot for Filezilla shown below:
DDOS toolkit:
Trojan may perform DDOS attack using the following tools condis , slowloris, udp also malware contains fake user agents that could help to launch this attack
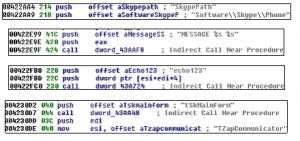
Skype Spam:
Neurevt tries to access Skype via SendInput API like “tSkMainFom” and “TZapCommunicator” and send message to contacts :
Recommendations:
Think, before you click! Read the prompts your system shows you and do not click “Yes” or “OK” thoughtlessly. In case of doubt, ask someone for help or try to search the Internet for more information about the prompt in question.
An up-to-date comprehensive security solution with a malware scanner, firewall, web and real-time protection is an absolute must. A spam filter that protects you from unwanted spam emails also makes sense.
The installed operating system, browser and its components as well as the security solution installed should always be kept up-to-date. Program updates should be installed as soon as possible to close existing security vulnerabilities.
In addition to these recommendations, more details exist at the following link: https://blog.gdatasoftware.com/blog/article/a-new-bot-on-the-market-beta-bot.html
Removal
To detect and remove this threat and other malicious software that may be installed on your computer, run a full-system scan with an appropriate, up-to-date, security solution.
About The Author
May Medhat, Malware Analyst at EG CERT