Mobile Phone Forensics
Digital Forensics: It is not new, but as long as there is data, it is applicable.
In the past years the need of computer forensic science has been upraised after the crimes got intelligent and computer dependent, this science firstly appeared – as we know- in the United States, its importance strongly appeared in the last decade when the cyber war got even wilder and wilder.The Computer forensic doesn’t mean only computers, the more generic name is Digital Forensic which includes all types of electronic devices which, in one case or another, can contain evidence or lead to evidence such as computers, PDAs, USB devices, memory cards, optical media, volatile memory, GPS devices, network traffic and last but not least the mobile phones.
In the last few years mobile phones got smarter and more powerful, you can do your daily work from your mobile phone and in some days you don’t need to get your Laptop opened, a hacker can conduct an attack from his smart phone and a criminal can commit an electronic crime using his smart phone or tablet, from there the need to do forensic analysis on smart phones strongly raised.
The tricky part in the Mobile forensic is the various and the way different operating systems run on smart phones nowadays, for example:
• Android, the open source Linux based OS.
• IOS, used by Apple.
• RIM, used by BlackBerry.
• Windows Mobile Phones.
• Symbian, used by Nokia.
• Bada, New OS developed by Samsung.
Besides the huge number of devices appear in market every short period, this makes the mobile forensics software manufactures apply frequent updates to their software with new compatibilities to keep track with new devices.
In some cases the mobile under investigation is the victim not the suspect, you need to know what you are looking for and the
case circumstances before start analyzing.
The information that may contains evidential data in mobile phones and can be useful for the analysis and add valuable data to the investigation are more than
what you firstly think such as:
• Contacts (Phone numbers, e-mail addresses and messengers), you can expose relations between the mobile owner to other persons in the case.
• Call logs (dialed, received and missed), prove that there were communication between specific parties.
• Conversation messages (received and sent), can contain important data exchanged between the case parties.
• Network information can prove unusual network activity, such as sending private information over the internet to a specific destination.
• WIFI history, prove that he connected to the hacked network in a case.
• Web history, for different mobile browsers, can prove that the owner viewed specific pages related to a case.
• Installed applications, if the installed applications has malicious goals related to the case this information will be so important, such as spying application.
• Social network programs and chat history, for various chat programs like Skype.
• Organizer information, calendar, memos, appointments and to-do lists.
• The OS log files that will show you information about the OS behavior.
• You can also do time-Line analysis, to keep track of the user’s activities regardless which application was used.
• The normal file system browsing and analysis.
• The keyword search can reveal a hidden related data.
• Also you can extract the words used by the user in messages, search, e-mail, etc…
• GPS information, specially the GPS history, can prove that the mobile holder was in a specific place and also in the coordinates stored with the camera snapshot, which shows where that photo was taken (Geo positioning information).
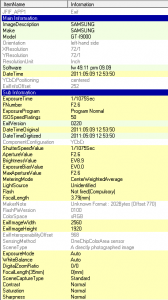
• Photos and videos, by viewing the EXIF (Exchangeable image file format) data of the photos, you can collect valuable information such as timestamp and shooting information and here is an example from EXIF reader:
Mobile Forensics Software:
There are several mobile forensic programs, today we will talk about the Oxygen Forensic Suite with Samsung Galaxy S (I9000) smart phone, and the suite will need to upload an agent to the mobile under investigation, with the following steps:
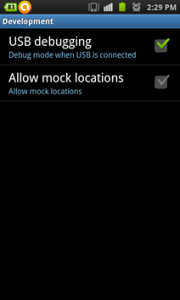
• In the smart phone, select USB debugging option from settings — Application — Development, as follow:
• Install the mobile driver in your machine and connect the smart phone to the computer by the cable, Bluetooth or infrared.
• Open the program and start connection wizard, after a while it will read your mobile and you need to confirm that the shown mobile is the same what you need to conduct analysis on.
• Select to upload the Oxygen Agent (OxyAgent), it will uninstall itself after finish acquiring.
• At the mobile phone you will notice the active agent.
• After finishing, select to add the phone to the case and start navigation and analysis.
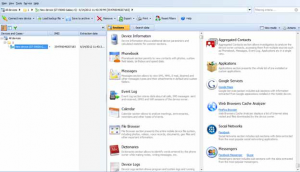
The below figure represents the main window of the program and you can investigate each point of interest (contacts, Call Log …etc) as mentioned at the beginning of the article:

About The Author
Ayman Shaaban, Security Researcher at Kaspersky Lab