My Story with Packetyzer development : C++ packet analysis library
| Cairo Security Camp 2018 | Rating 0 |
| Post / Page | Order By: Most Rated | Highest Rated |
|---|---|
| Writing Your Own Malware |
[Total:139 Average 3.7] |
| Issue 20 |
[Total:34 Average 1.5] |
| Pentesting on Non-Jailbroken IOS Device’s– PART1 |
[Total:23 Average 4] |
| Computer Forensics Lab Requirements |
[Total:21 Average 3.2] |
| Xss Attack Through MetaSploit |
[Total:14 Average 3.9] |
| CAM Table Overflow Attack & how to prevent it |
[Total:8 Average 3.5] |
| Security of Radio Frequency Identification (RFID) Tags |
[Total:8 Average 3.4] |
| Killing Android Mobile SIM Cards Using USSD |
[Total:7 Average 3.7] |
| Master of Security Science (MSS) By EC-Council University Program Review |
[Total:6 Average 2.2] |
| Pentesting on Non-Jailbroken IOS Device’s!! PART2 |
[Total:6 Average 3.8] |
| Post / Page | Order By: Most Rated | Highest Rated |
|---|---|
| Interview With Vivek Ramachandran Founder of Security Tube.net |
[Total:2 Average 5] |
| Grey Box Pentesting Scenario |
[Total:2 Average 5] |
| Encrypting Windows Traffic Using IPSec PART1 |
[Total:2 Average 5] |
| Mobile Device Forensics at a glance |
[Total:4 Average 4.8] |
| Understanding the POS (Point-of-sale) Malware |
[Total:2 Average 4.5] |
| Custom Shellcode Encoders |
[Total:5 Average 4.4] |
| Issue 23 |
[Total:4 Average 4] |
| Issue 15 |
[Total:3 Average 4] |
| Pentesting on Non-Jailbroken IOS Device’s– PART1 |
[Total:23 Average 4] |
| Xss Attack Through MetaSploit |
[Total:14 Average 3.9] |
It’s very basic for a security pentester or security engineer to have a solid understanding of computer networking fundamentals, so as I was new to these fundamentals I thought it would be a great experience to contribute to the “SRDF Project” where my experience started. Today I am going to tell you about my story with pushing my first Packet Structure Class & developing my packet analysis library “Packetyzer”.
The story began when I met a friend “Eng. Amr Thabet during a session at my college, where he started to tell me about his project & that he was looking for contributors. Moreover I was really motivated to contribute and it would help me gain programming and networking experience, as my C++ language skills were not powerful enough.
Let me tell you about my project. Packetyzer is a high level library for C++ designed to make the forging and decoding of network packets easier. It has the ability to decode packets of the most common network protocols, capture them and send them on the wire. This capability allows the construction of tools that can probe, scan or attack networks. It enables the creation of networking tools in a few lines.
A packet is described by its protocol layer type, where fields of each layer have useful default values that you can overload. All packets and connection streams are analyzed, from the Ethernet header to the application layer protocols.
Raw packets are represented as an array of cPacket class where each packet is analyzed carefully. cPacket is the main packet representation used in Packetyzer
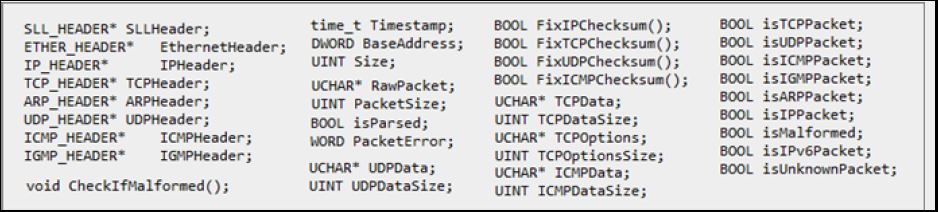
After my first push I was motivated to continue and enhance this class. Amr guided me, so I started to widen the functionality of the class. Following the OOP theory I have created other classes like cPcapFile where packets are feed to the packet stack through it “using a pcap file” or even by cPacketGen “generating raw packets” or cWinpcapCapture “capturing network packets”, where the stack is analyzed and represented as a traffic structure “by cTraffic class”.
Moreover cTraffic was the start as its responsible to analyze packets of the same session and add the related packets by their protocol types as Streams which are composed of IP protocols “cConStream” and non-IP protocols “cARPStream & ICMPStream”. cConstream analyzes TCP and UDP protocols, then the application layer protocols are decoded into their related Streams “like cHTTPStream”.
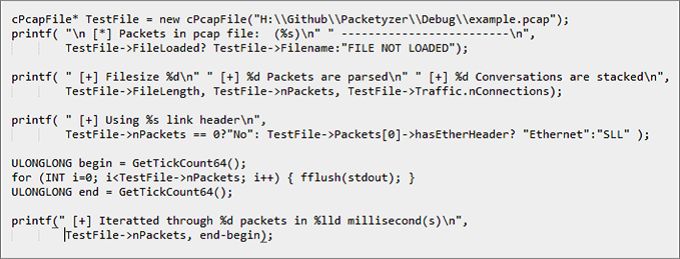
The following shows a basic usage of my library: Packetyzer calculates packet checksum and checks the TTL to detect if the packet is forged. It has the ability to recalculate the checksum and correct it in the actual packet. I have enhanced cTCPReassembler to reassemble TCP Segments and get the data buffer from the packets reassembly.
Over a month I have been optimizing the memory usage for the library, after inspecting the memory usage and analyzing a pcap file of 10000 packets whose file size is 93.0 Mb. I have found that after freeing memory there was garbage left behind of about 500Kb which is very low when compared to other libraries, even Wireshark.
At the end of the day, all I can say is that this was a great experience for me, which allowed me to have an open mind on other aspects of computer networking and computer security.
I am planning to have many more features in Packetyzer Enhancing TCP Reassembler to be more intelligent.
• Implementing IPv6, IPv6 Options Decoders.
• Adding Layered Service Provider class.
• Adding more application layer parsers.
About The Author

Anwar Mohamed, Mobile Security Researcher