Ransomware : Trojan that encrypts most file types in a system
1. EXECUTIVE SUMMARY
This is an analysis of a packed executable malware. This sample is identified as ransomware. In-depth behavioral and code analysis is performed on this sample. This malware is a packed executable (The executable was packed by UPX). This malware is a Trojan that encrypts most file types in a system so that they can’t be accessible unless the user enters the correct password.
2. Identification
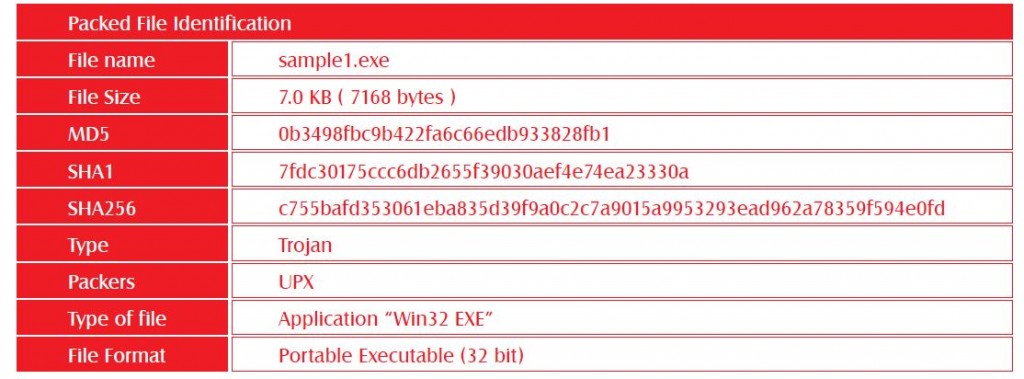
2.1 Packed File Information
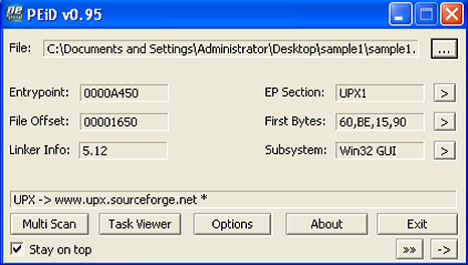
2.2 Packing detection
3. Behavior analysis
3.1 Process Activity:
Malware doesn’t create or kill any processes
3.2 File Activity:
As a malware encrypt files on the system so it almost reads and writes all files exist in the system . In addition it creates two files
C:\Documents and Settings\Administrator\Local Settings\Temp\3mN6As37iqV6y5t.exe
C:\Documents and Settings\Administrator\Desktop\-+- -+-+++-+-+-_ +++-¦.txt
3.3 Registry Activity:
• Set a new value “C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\3mN6As37iqV6y5t.exe” in “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” with name “Alcmeter”
• Create sub key “HKEY_CLASSES_ROOT\.crypt” with value “UVLBIYGQHQZADNF”
• Create sub keys “HKEY_CLASSES_ROOT\UVLBIYGQHQZADNF” with unnamed value “CRYPTED!”
• Create sub key “HKEY_CLASSES_ROOT\UVLBIYGQHQZADNF\DefaultIcon” with unnamed value “C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\3mN6As37iqV6y5t.exe,0”
• Create sub key “HKEY_CLASSES_ROOT\UVLBIYGQHQZADNF\shell\open\command” with unnamed value “C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\3mN6As37iqV6y5t.exe”
3.4 Network Activity:
Malware doesn’t initiate or receive any network connection
4. Code analysis
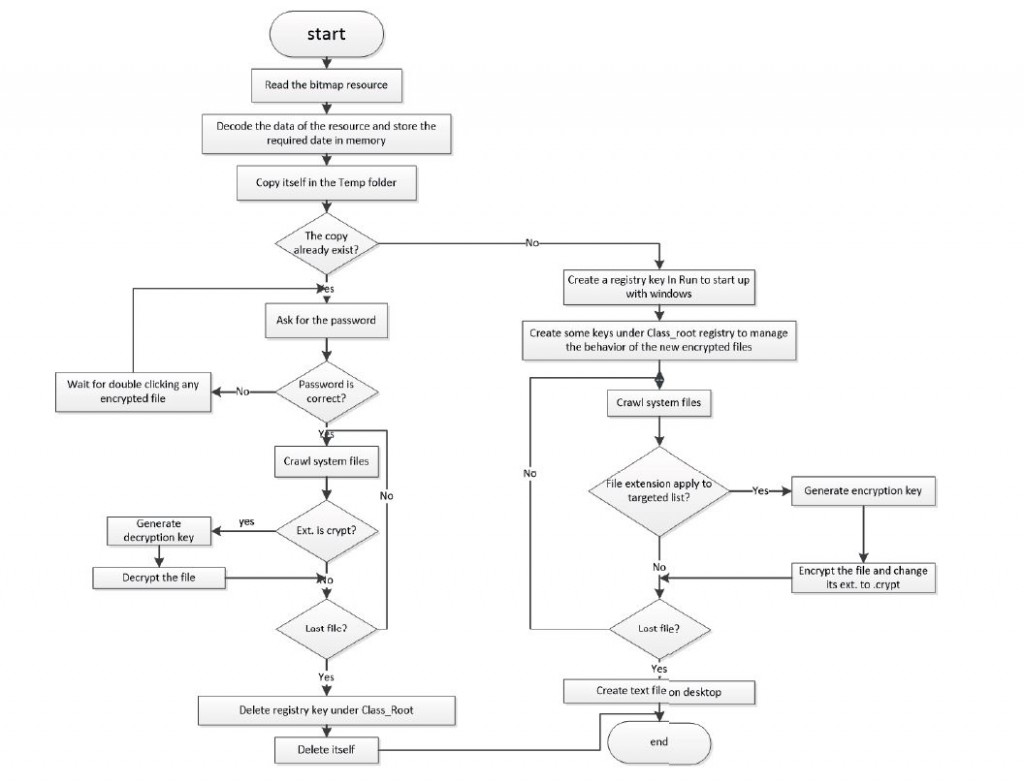
At first the malware prepares the data needed in its operation. It gets this data from a bitmap resource by reading its data and decoding and then arranging this data in memory by RtlMoveMemory API
• Dword_144c30 » list of targeted extinction
• Dword_143e38 » string “crypt”
• Dword_406db9 » encoding key
• Dword_406dc9 » hash of password (MD5 hashed five times)
•Dword_406dd9 » random name for file copied in temp folder
• Dword_406de9 » random name for created registry key under Class_root registry
After preparing data in memory malware starts copying itself in “C:\Documents and Settings\Administrator\Local Settings\Temp” directory and set its metadata to the metadata of the file “explorer.exe”.
Now the malware needs to ensure that it is running at startup and defines how the new file type “.crypt” created by malware behaves when it is double-clicked. After that, it creates a new value “C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\3mN6As37iqV6y5t.exe” with name “Alcmeter” in registry key “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” to ensure its running at startup. It creates sub key “HKEY_CLASSES_ROOT\.crypt” with unnamed value “UVLBIYGQHQZADNF” which is the key contains the program used to run this type of files and the sub key “HKEY_CLASSES_ROOT\UVLBIYGQHQZADNF” with unnamed value “CRYPTED!” , sub key “HKEY_CLASSES_ROOT\UVLBIYGQHQZADNF\DefaultIcon” with unnamed value “C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\3mN6As37iqV6y5t.exe,0”, and sub key “HKEY_CLASSES_ROOT\UVLBIYGQHQZADNF\shell\open\command” with unnamed value “C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\3mN6As37iqV6y5t.exe” to define the behavior of the encrypted file.
Now the malware prepares everything and becomes ready to start its destructive action. It starts to crawl all files in the system and checks which of them exists in list of targets to encrypt it.
It gets the available partitions on the system then crawls them one by one. When it gets the first file it checks if it is file or directory. If it is directory, malware check if it is the same directory (.), the parent directory, or it is not. In case of same directory or parent directory malware escape it and continues to the next file otherwise it will access the directory and continue crawling. In case it is file, the malware starts comparing its extension with targeted list. If the extension is not existed in the list, the file is escaped and malware continues to the next file, else the procedure of encryption is started. When the file extension exists in the target list then the malware starts the process of encryption.
At first the malware gets the file size and metadata then moves the file pointer 79 bytes then reads the file into memory. After reading the file, the malware gets the first character of file name and uses it with the data in address 0x406595 to generate the encryption key in address 0x406585 then starts the encryption procedure. After encryption, the malware moves the file pointer 79 bytes then writes the encrypted data to the file and sets its metadata to one that it did read before. Finally it renames the file to the same name with the new extension (.crypt) and continues to the next file.
After finishing encryption of all files, the malware creates a text file on desktop with name “-+- -+-+++-+-+-_ +++-¦.txt” then it searches for another bitmap resource called “pussylicker.bmp” and tries to use its data to write a new file but actually it didn’t find this resource. At this point, the malware finishes its destructive action and waits for user action.
When a user restarts the system or double-clicks any encrypted file it runs the copied version of malware existed in Temp folder. When this copy runs, it asks the user to enter password then it hashes the password by MD5 algorithm five times then compares the resulted hash with the stored hash in address 0x406dc9. If the password is wrong a massage popped up then returns to waiting state. If the entered password is right, the malware executes exactly what it executed in encryption process with some differences:
• It searches only for files with extensions .crypt
• After key generation, it runs decryption procedure instead of encryption procedure
After decryption of all files of the system, the malware deletes the sub key “HKEY_CLASSES_ROOT\ .crypt” then deletes the sample (keep the run registry and the copy in Temp folder)
5. Removing malware
Step 1:
Patch the malware to reverse its action after comparing password and run it on the system.
This step will lead to decryption of all encrypted files and deleting the malware and sub key registry HKEY_CLASSES_ROOT\.crypt when entering any wrong password
Step 2:
Delete the files created by the malware
C:\Documents and Settings\Administrator\Local Settings\Temp\3mN6As37iqV6y5t.exe
C:\Documents and Settings\Administrator\Desktop\-+- -+-+++-+-+-_ +++-¦.txt. Confirm that the sample file is deleted
Step3:
Delete the value “Alcmeter” that is added in “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” registry
Delete the sub key HKEY_CLASSES_ROOT\ UVLBIYGQHQZADNF
Confirm that the value in Run registry is deleted
About The Author
Mohamed Elhenawy, Senior Malware Analyst at Eg-CERT