Crack into a Wireless Network or Make a Sandwich?
That’s right
It all started while being so hungry and trying to figure out what to eat, during the last visit to my family and found out that my brother has changed the wireless connection password. The moment I started thinking of what to do, few application names popped out of my head such as aircrack-ng, weplab, WEPCrack, or airsnort.
As my eyes gaze around the room, checking what else could have possibly changed, I found this mini-live-cd based on Tiny Core Linux called ”Beini” a Chinese GNU/Linux distribution, created and maintained by ZhaoChunsheng from Tianjin, China lying around on my desk.
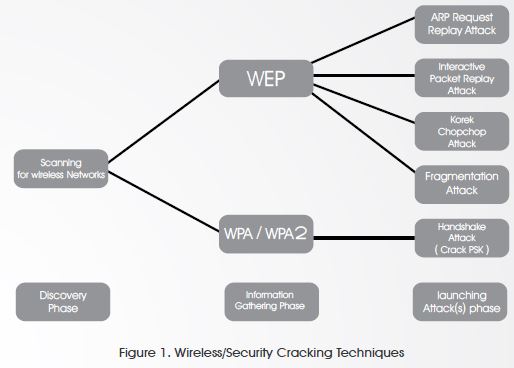
The distribution is not commonly known and/ or used however, it is very light and if you need an easy and simple way to crack into a wireless network, Beini is the best open source tool for it. It took me less than a minute to boot from the CD, and another couple of minutes to get the key for the house wireless network. As I am about to show you step by step how-to crack into a wireless network, first let me show you how would I think and what are the techniques that could be used on the figure below (Figure 1):
Wired Equivalent Privacy (WEP)
I would probably use the following cracking techniques:
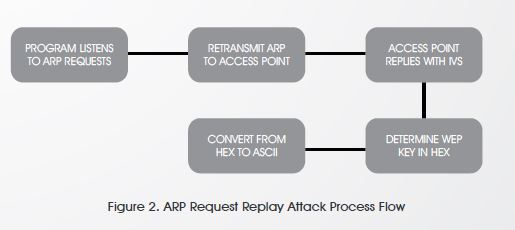
1. ARP Request Replay Attack
This is a very effective way to create new initialization vectors (IVs), the program listens for an Address Resolution Protocol (ARP) packet then retransmits it back to the access point. The access point keeps responding with ARPs (new IVs) and this way we’ll be able to determine the WEP key
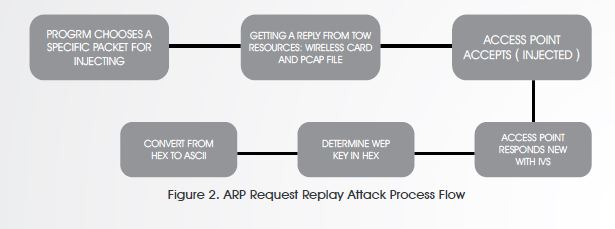
2. Interactive Packet Replay Attack
This attack allows you to inject and obtain packets to replay from your own wireless card and a pcap file (heard of something called “libpcap” before? Maybe?). Certain packets would only work (to be accepted by the access point) which will in return cause new IVs, and that’s the goal of this whole process, new IVs to find the WEP Key.
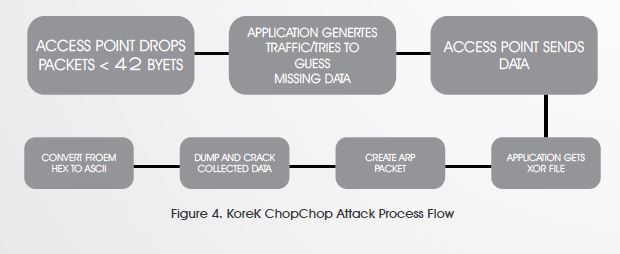
3. KoreK ChopChop Attack
Decode one packet! Disclose the plain text. Successful attacks can decrypt a WEP data packet without knowing the key. It is also worth mentioning that it can even work against dynamic WEP which is a combination of 802.1x technology and the Extensible Authentication Protocol (EAP) — Dynamic WEP changes WEP keys dynamically.
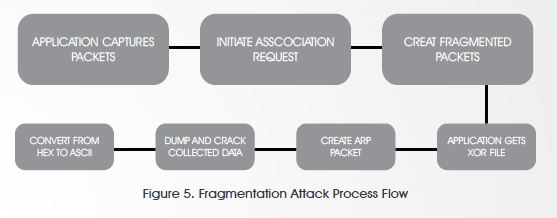
4. Fragmentation Attack
Again, fragmentation attack does not recover the WEP key itself, but only obtains the PRGA (Pseudo Random Generation Algorithm). PRGA can be utilized later on to generate packets which is also in return help in the injection attacks. The attack obtains the full packet length of 1500 bytes xor, so any size of packet could be generated, and is sufficient to create ARP request.
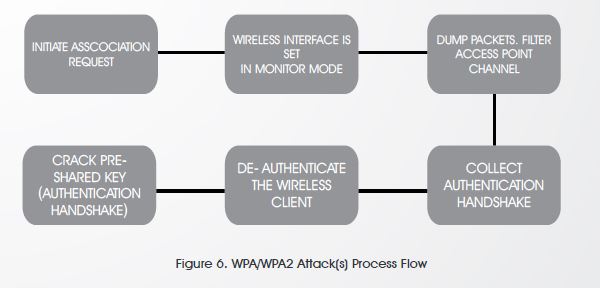
Wi-Fi Protected Access (WPA/WPA2)
The authentication methodology is the same on both, a dictionary attack must be deployed otherwise forget about it (in case of brute-force/dictionary attack failure)
Alright alright, enough talking, let’s start cracking.
First, I will boot up my device using the Beini Live CD (from a USB stick or a regular CD)
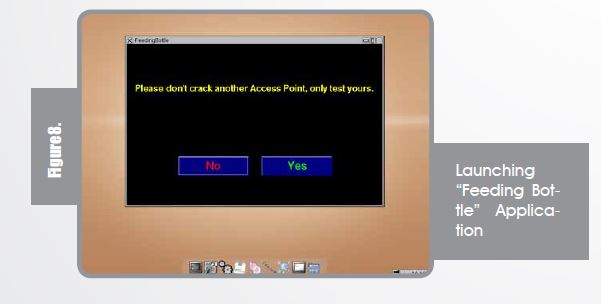
Choose the “FeedingBottle” icon from the task bar.
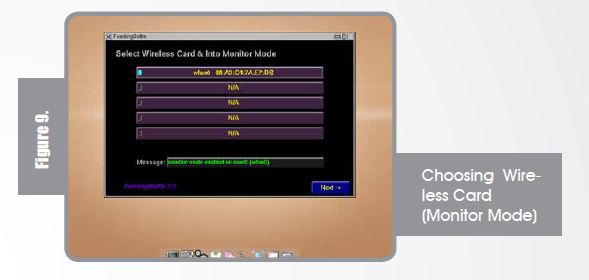
Please remember, this is only a proof of concept and you may test it on your access point only. After clicking “Yes” you will get the following screen to choose your wireless card and setting it into “Monitor” Mode.
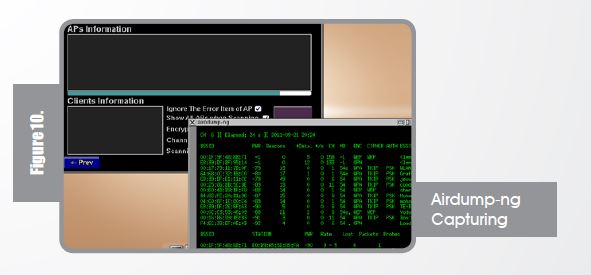
Once you hit “Next ->” and “Scan” airdump-ng starts to capture raw 802.11 frames to start collecting IVs.
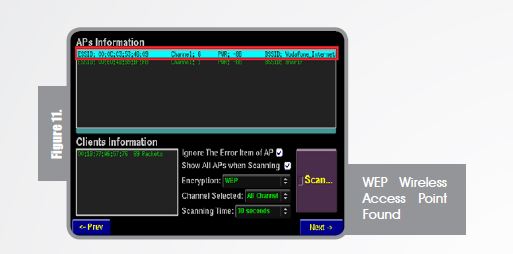
After scanning the large network (so many birds to hunt) I choose my house access point, I am a good guy.
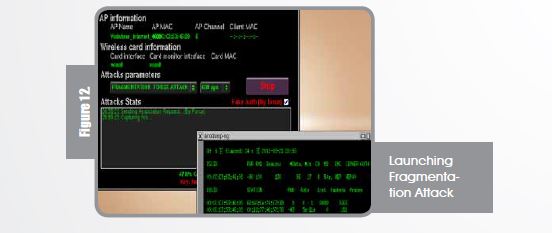
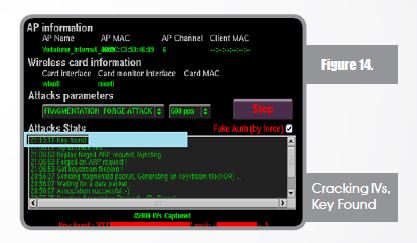
As previously mentioned, I would think of 4 attacks to launch against WEP of which “ARP Request Replay Attack” is considered to be the quickest and “Fragmentation Attack” is considered to be the longest, at least in my very own opinion and more reliable since ChopChop attack doesn’t work with all access points. On this proof-of-concept I will be showing you the longest way “Fragmentation Attack”. Launching Fragmentation Attack
Once the attack is launched, airdump-ng starts to capture, IVs are the keys of our success, we try to initiate association request for fake authentication.
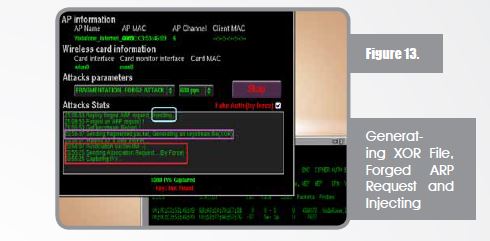
Now association is happening, fragmented packets will be sent and generating a key stream file (xor file that will help in creating packets without knowing the key).
After the injection, IVs are being captured and collected to start cracking. IVs collecting/ capturing is what counts and not the packets because it doesn’t help us with WEP cracking and many of the packets will be beacons (transmitted by access points to show their existence – hey I am here!).
When enough IVs are captured (depending on the WEP Key size) you shall find the cracker working smoothly and in a few minutes the message “Key Found” will light up your eyes. Below you will see that the key was found and even converted to ASCII (from HEX).
Finally, cracking into wireless networks could be easy, and it could take a few minutes, especially in the case of Wired Equivalent Privacy (WEP) Security. In that case, it is highly recommended to switch to the newer security, WPA2 which is using Advanced Encryption Stand-ard (AES), and use higher security techniques in order to protect your wireless network. Also, it is worth mentioning that the strength of your password plays a main role, so please consider using a strong password including uppercase/lowercase characters, numbers, and symbols. Last but not least, please use the above mentioned information wisely and remember: “With Great Power, Comes Great Responsibility” – Spider Man
About The Author

Sameh Sabry, Associate Vice President – Professional Services at SPIRE SOLUTIONS