Dyre Wolf Attack
Dyre Wolf Attack
Banking Trojans, malware designed to leach money from compromised accounts, are nothing new to the world of cyber security. According to that, these targets accounts are personal checking or saving accounts belonging to individuals that happen to fall prey to the malware. Hundreds, even thousands of dollars can be transferred out of individual’s accounts and directly into the attackers and earning them quick money.
The victim calls the attacker number and is greeted by a very professional-sounding person with an American accent who states he works with the relevant bank. After a brief conversation, this individual prompts the victim to give the username and password in question for the account and verifies it, several times. The attacker may also ask for a token code. Within this verifying stage, the attacker might ask to speak with a co-worker with similar access to the account, and who may be one of the authorized persons on that account, and ask them to verify information as well, and give a token code over the phone.
There have been several reports of compromise resulting in losses of $500,000 to over $1,000,000 USD. It’s important to note, these attackers are targeting organizations that typically make large transfers of this size on a regular basis to try to avoid triggering fraud detection mechanisms in place.
What is the Dyre Wolf?
This is a new campaign that utilizes the now popular Dyre, or Dyreza, malware directly targeting corporate banking accounts and has successfully stolen upwards of a million dollars from unsuspecting companies. (The Dyre wolf wants Money). In Q1 of 2015, the Dyre Trojan was the top offender among the top malware families attacking globally.
How Dyre Wolf works?
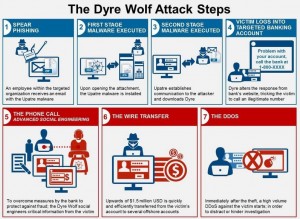
The following figure shows the Dyre Wolf attack sequence.
Step 1 Spear Phishing:
The mail that the employee received contain zip file, this file named “invoice”, “fax”, or “doc” with random number generated behind it (file147357x.zip). The file inside the zip has an embedded PDF icon but actually it is an EXE or SCR file. Phishing mail characteristics and attachments:
Subject: Unpaid invoice
Subject: Your FED TAX payment was rejected
Subject: Invoice #1006501
Subject: New Bank Details
Attachment: Invoice [6 random numbers].pdf
Attachment: ADP-invoice.pptx
Step 2 the first stage malware is executed:
- Upatre malware uses “checkip.dynds.org” to determine the public IP address of the attacker machine. This website replies with a simple message “current IP address: X.X.X.X” this malware uses this information to understand who has been infected.
- Next a STUN (Session Traversal Utilities for NAT) server is contacted to determine the public IP address and the type of NAT (Network Address Translation).
- Internet connectivity is checked to determine if the proxy is being utilized by contacting google.com.
- Upatre makes its initial contact with the command and control (C&C) server.
The following are known C2 servers: 109.228.17.152, 109.228.17.155, 109.228.17.158, 166.78.103.85, 176.114.0.58, 193.203.50.17, 193.203.50.69, 202.153.35.133, 203.183.172.196, 212.56.214.130, 212.56.214.154, 213.239.209.196, 217.172.179.9, 217.172.181.164, 217.172.184.75, 217.23.8.68, 80.248.224.75, 85.25.134.53, 85.25.138.12, 85.25.145.179, 93.190.139.178, 94.23.196.90, 94.23.61.172
- Upatre downloads Dyre file from a varied list of domains as well as changing filenames.
Step 3 the second stage malware is executed:
- Establishing persistence: As a part of installation, the dyre malware establishes persistence by creating a service “Google Update Service” (googleupdaterr.exe) or “User Data Update” (userdata.dat), this service is set to run automatically each time the system restart. Once the system started, it then inject a malicious code into the legitimate SVCHOST.EXE process after which the malicious “Google Update Service” stops.
- Establishing a darknet: During this stage the Dyre malware makes connections to several nodes in order to establish peer to peer tunneling network.
- Web browser hooking: once Dyre has installed itself and established a solid networking connection, it hooks to victim’s browser (Internet Explorer, Firefox and Chrome) in order to intercept credentials the user may enter when visiting any of the targeted banks sites.
- Email Spreading: If Dyre detects that the OUTLOOK email client is installed, it will attempt to send email messages to various recipients with DYRE Payloads attached as zip file. The body of mail content will be mysterious as example (Please remit BACs before date DD/MM/YYYY).
Step 4 Victim logs into targeted bank account:
The dyre alters the bank page with the fake number 1-XXX-XXX-XXX
Step 5 the phone call – Enter advanced social Engineering:
Dyre has a number of different ways to operate its social engineering schemes:
- The classic injection: In this technique Dyre monitors the victim’s online activity. The moment the victim attempts to browse to one of Dyre’s targeted web pages [Bank of America, NatWest, Citibank, RBS (Royal Bank Of Scotland), Ulsterbank] , the malware injects new fillable data fields into the page, all while collecting the victim’s login credentials. This is a classic injection mechanism for banking trojans, it happens on the legitimate original page, and is commonly implemented by malware like ZeuS and all its offspring, SpyEye, GootKit, Bugat, etc.
- The Proxy and web fakes: In this technique Dyre monitors the victim’s online activity. The moment the victim attempts to browse to one of Dyre’s targeted web pages, the malware redirects the request through a proxy server over to Dyre’s server. In response, the C&C sends back a page replica of the bank’s webpage adapted to the original page the victim was supposed to reach. This replica is completely faked and contains extra data fields for the victim to fill out.
- On the fly – server side injection: In this technique Dyre again monitors the victim’s online activity. The moment the victim attempts to browse to one of Dyre’s targeted web pages, the malware intercepts the response from the bank’s servers. It reaches out to its operators’ highly secure PHP server, presenting it with the bank’s original page response. The PHP server takes over and sends the response to the victim’s browser, only this time it includes adapted code injections that are thrown into the bank’s response before it is served back to the victim. This is an on-the-fly mechanism that Dyre uses to avoid coding its injections into the configuration file. It also allows the attacker to communicate with victims in real time, presenting them with carefully selected social engineering designed to complete a fraudulent transaction.
Step 6 The Wire Transfer:
After obtaining the credentials from the victim, the attacker logs into the account and transfers some amount of money. There have been several reports of compromise resulting in losses of $500,000 to over $1,000,000 USD. It’s important to note, these attackers are targeting organizations that typically make large transfers of this size on a regular basis to try to avoid triggering fraud detection mechanisms in place.
Step 7 The DDOS:
Immediately after the wire transfer happens, the attacker issues a DDoS attack against the victim. The DDoS itself appears to be volumetric in nature. Using reflection attacks with NTP and DNS, the Dyre Wolf operators are able to overwhelm any resource downstream.
Recommendation Techniques:
There are several ways that organization can take in order to stop or limit the risk of the Upatre or Dyre Malware:
- Strip executable from email attachments (configure mail server to strep any executable files)
- Current antivirus and/or endpoint protection.
- Restrict execution of programs from temp folders.
- Use Two Factor Authentication with banking sites (Recommended to utilize the maximum security features)
- End user awareness (Be proactive with end-user education and security awareness)
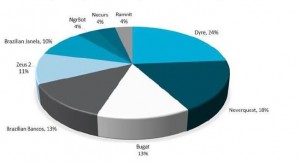
DYRE Statistics:
The Dyre/Dyreza Trojan started out as a seemingly simple RAT (Remote Access Trojan) project around mid-2014.
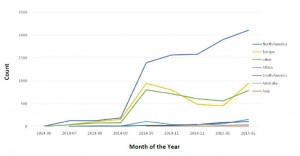
North America is the most affected geography seeing highest infection rates of Dyre. This falls in line with the majority of the banks targeted by Dyre.
About Author
Ahmed M. Hammad, Information Security Engineer at Security Meter