GVOL : GUI app built in java for the purpose of malware analysis
Every function performed whether by an application or operating system produces a particular change at (RAM) memory. Consequently, analyzing the data captured from memory image acquired from a target system gives an extraordinary insight into the runtime state of the memory, enables the analyst to track recent activities and bypass hiding tools such as those used by rootkits.
Furthermore, analyst using memory analysis could examine critical data such as unencrypted mails, non-cacheable internet history events, code injection…etc. Moreover, it is so useful for malware analysis procedures allowing analyst to know what occurred before and after infection of the system. One of the best toolkits used for memory analysis is Volatility. In this article, we introduce GVol which is a GUI and automation tool for Volatility framework.
GVol is a lightweight GUI application built in Java designed to automate the usage of Volatility toolkit for the purpose of malware analysis. The application includes various Volatility plugins with their predefined options.
In addition to that, users can create batch files to run multiple plugins at once to scan a memory image. Furthermore, GVol includes pre-configured batch files to simplify the usage of Volatility for malware analysis process.
The supported operating systems are Windows XP, 7, 8, 8.1, and Linux. The application requires the Java Runtime Environment. GVol has some predefined batch files, plugins, options and profiles.
GVol Features:
1. GVol automates the use of Volatility using a graphical user interface.
2. It works with any Volatility version.
3. GVol includes a set of predefined profiles for windows operating system, also the user can add new profiles of other operating systems.
4. User can select plugins and related options from the existing database or add new plugins or options.
5. GVol has batch file feature to run multiple plugins. In addition to that, user can set options for each plugin at batch file through a graphical wizard.
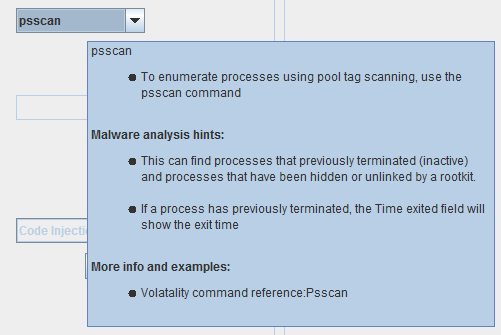
6. GVol contains a plugin description and malware analysis hints gathered from “The Art of Memory Forensics” book and “Volatility Command Reference” which can downloaded from this link: https://code. google.com/p/wiki/CommandReference23
7. GVol has a console output section which shows the command running at background and also the output generated. The user can chose to write this output to a file. The output file name will be a concatenation of the following image name, batch file name (if it was used) and plugin name.
How to Use GVol:
1. Download GVol from the following link: https:// github.com/eg-cert/GVol
2. Open the file “GVol.jar” to open GVol main interface.
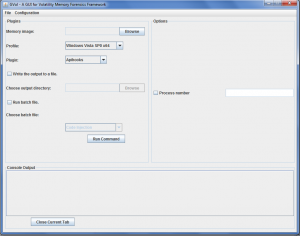
GVol Configuration:
- Download Volatility toolkit: https://code.google.com/p/Volatility/downloads/list
- Select “Configuration” from the main interface to edit Volatility configurations.
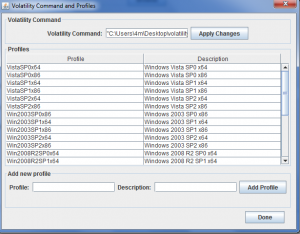
- Select “Command & Profiles”.
- Type the command that runs Volatility. It would be the path of the standalone executable or “Python vol.py” if you use the python script. Do not forget to click on “Apply Changes”.
- Profiles can be added through “Add new profiles” section by writing the new Volatility profile and its description then click “Add Profile”.
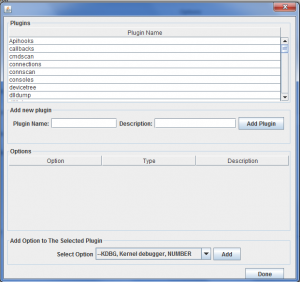
- To add new options or delete an old one, From “Configuration” menu, select “Volatility Options”.
- Also, user can edit Volatility plugins and select their convenient options by selecting plugins from “Configuration” menu.
- User also can update plugin description, by typing plugin name and its description then click “Yes” to update existing plugins.
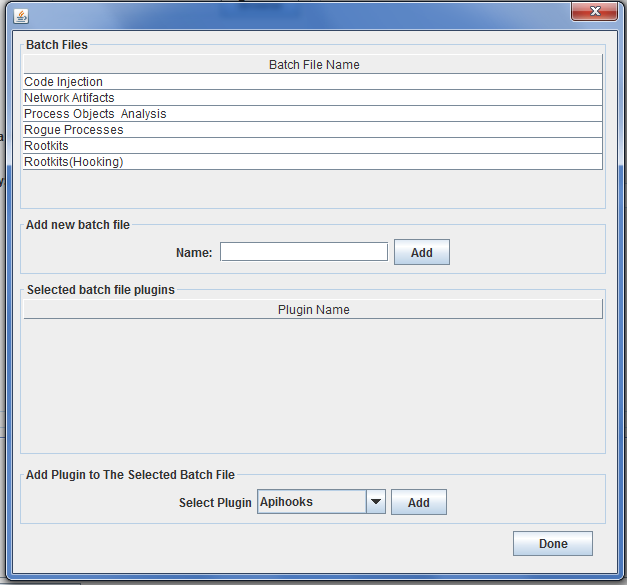
GVol Batch File Feature:
User can run multiple plugins to scan a single image through Batch files as follows:
- First of all, batch file must be added or selected from the main menu.
- Select File then “Manage Batch Files”.
- A new batch file can be added by typing its name to “Add new batch file” section.
Attach required plugins to the batch file selected from “Add Plugins to the Selected Batch File.”
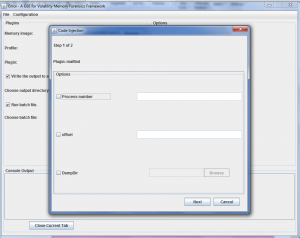
GVol includes preconfigured batch files, each batch file contains some plugins that could be used to achieve a certain scanning or detection. GVol available batch files now are: Code injection batch file, network artifacts batch file, rogue processes batch file, process Objects analysis and rootkits batch file.
Running GVol:
User can select between two options either running GVol with single plugin or running multiple plugins by using the batch file option.
Running single plugin:
- Determine the target image to scan and specify its profile.
- Check plugin description and hints by just pausing the mouse pointer at the selected plugin.
- Choose plugins and set their options.
- Select “Write the output to a file”.
- Select the output directory.
- Click “Run command”.
Notes:
You can run another simultaneous command by repeating these steps (1-6). The output of the new command will be visible in a new tab in the output area.
You can stop a running command by selecting its tab and clicking on the “Close current tab” button.
Running multiple plugins:
- Determine the target image to scan and specify its profile.
- Select the check box “Run batch file”.
- Specify the required batch file.
- Select the output directory.
- Click “Run Batch”.
- A wizard will appear to enable user set options for each plugin listed at the selected batch file.
GVol Output:
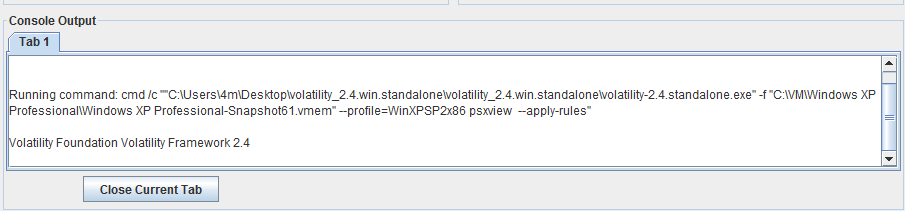
After running single plugin or batch file, user can check the running command and output also at “Console Output”.
If the user selected the “write the output to a file” option and he specified the output directory. The output file will be generated as follows:
- For single plugin, the output file name format will be as shown below:
- Image name: Windows XP Professional-Snapshot1
- Plugin name: psxview
- Output file number: output0
- For batch file, the output file name will be as shown below:
- Image Name: Windows XP Professional-Snapshot1
- Batch file name: Rogue Processes
- Plugin Name: psxview
- Output file number: output0
About The Author
May Medhat, Malware Analyst at EG-CERT
Mohamed Shawky, Developer at Eg-Cert