Hiding data inside the padding area of files
Today, we will talk about Steganography, which is the science of hiding information inside other data instead of just encrypting it. Steganography might be thought as the cousin of cryptography and, amazingly, both can be mixed to have something stronger than both.
In most cases, this can be done by changing small number of bytes in a file to the wanted data which can be an image file or a sound file.To make this clear, check the example below.
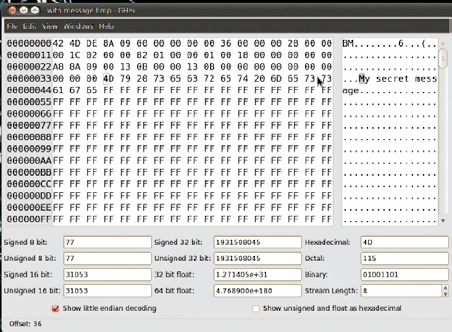
One of the following images contains the message, “My secret message”. Are you able to tell which of them contains the message?
Actually yes. By zooming in the second image, you will notice that the image has some colored pixels at the bottom left corner. Those pixels are the ones that contain the secret message
The following picture shows the image opened with a hex editor (you may use hex workshop in windows, ghex or bless hex editor in Linux):
What is going to be done is that the information will be hidden inside, what is called, the padding area. Before that, let us first talk about what is the padding area (you can skip this part if you are already familiar with the padding area).
What is the padding area??
Some bytes are added to a file or a network packet of a four byte alignment. These bytes are added because the computer is capable of handling data which are aligned of multiples of four bytes. It is faster since the registers and the buses are 32 bits (assuming a 32 bits machine). Also, one of the obvious examples is your graphics card which the frames sent to it are to be aligned of four bytes.
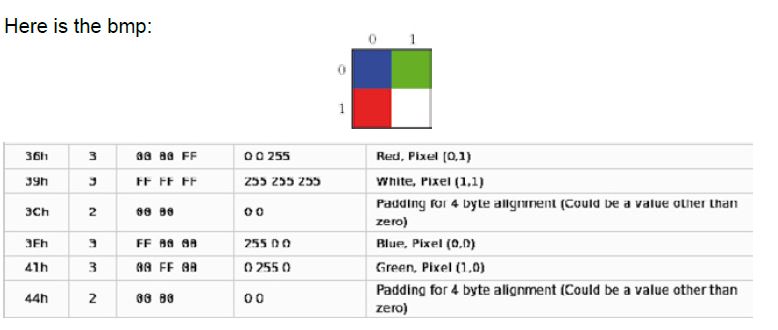
Let us examine a simple bmp file and see the padding area. This example is taken from bmp file specifications in wikipedi:
This table shows how the image is stored in the file: As seen above, the image of 4 pixels has four bytes wasted, and these bytes will not be rendered by any graphics application. In addition, no application cares about their value, so the hidden message is saved on them.
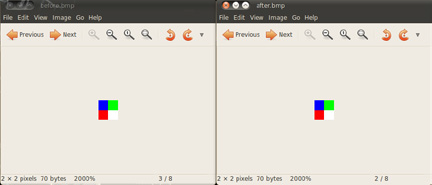
Let us do some test on it. In this 4 pixel image, the word “test” is stored in those 4 bytes and notice if the colors are changed. One of the following two images contains the message and the other one does not contain anything:
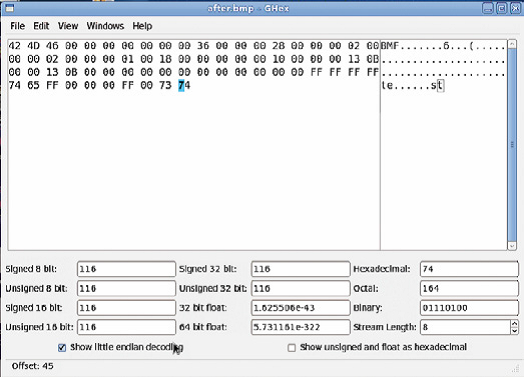
As seen above, the colors have not changed at all. In the following image, the second picture which contains the word “test” changed its colors when opened in ghex:
How to calculate the available padding space?
The available padding space is calculated by using the following formula (assuming a 32-bit machine):
(Number of pixels in a row * number of bytes for each pixel)%4 Where can it be used?
It can be used for hiding information, but also it can be used for uploading shell codes in websites that allows image uploading. However, this can be used by worms instead of uploading the shell code to a server. If it is used to store a shell code, will the antivirus be able to detect that?
It is believed that antivirus will not be able to detect that since the signature will be changed by either changing the image or rather its dimensions.
About The Author

Fady Osman, Information Security Consultant at ZINAD