ISO/IEC 27001:2013 PART2
In Part 1 , We Talked about ISO 27001 history, benefits, structure and content . Now we are going to tackle with the 114 security controls, certification process .
Link of Part1 | http://goo.gl/DFXTn0
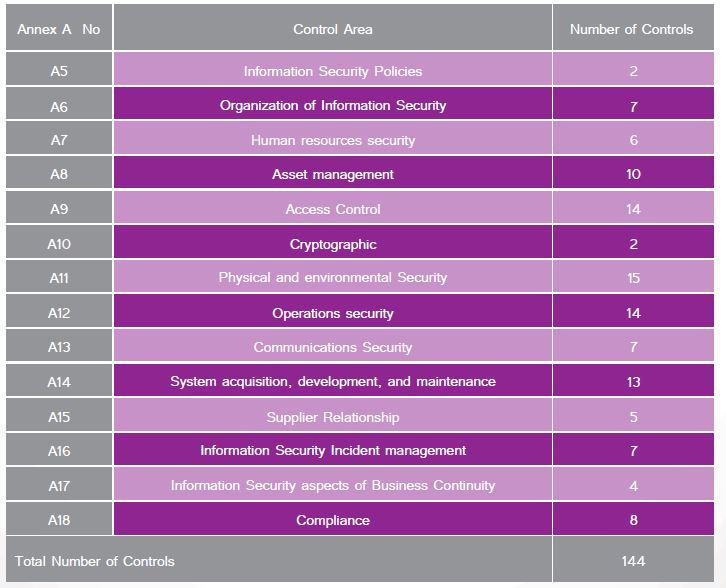
Annex A Control Objective and Controls
List of Control area and control objectives and Controls of ISMS
Annex A Control Objective and Controls : 114 Security Controls
Annex A is the best known series of security control objectives for Implementation ISO/IEC 27001:2013
All Controls are Optional to be implemented
Annex A Consist of
»14 Control Area : Core topic areas that Covered Most Aspects of Information Security
» 34 Control Objective : Objectives of Control
» 114 Control : Applicable Controls to be Implemented on ISMS Program
A.5: Information Security Policies
Manage and Update of Organization Information Security Policies
A.6: Organization of Information Security
Manage of Organization Information including: Identified Role and Responsibilities, Segregation of Duties, Mobile Devices and teleworking
A.7: Human resources security
Manage of Organization Human Resource including: During, prior Employment Relationship
A.8: Asset management
Manage of Organization Assets
A.9: Access Control
Manage and Control Access of Organization Information
A.10: Cryptographic
Control of Using Cryptographic inside Organization
A.11: Physical and environmental Security
Manage and Control of Organization Physical and environmental Access
A.12: Operations security
Manage and control all Operation security including : Operational Procedure and Responsibilities , logging and Monitoring , Technical vulnerability management and information systems audit
A.13: Communications Security
Manage and control Organization Communication Security including : Network security management and information transfer Controls
A.14: System acquisition, development, and maintenance
Manage and control System Development Cycle Including: identified and enforce security requirements , Secure of development system
A.15: Supplier Relationship
Manager suppliers relationship including : apply information security for supplier relationship and service delivery management
A.16: Information Security Incident management
Manage information security incident
A.17: Information Security aspects of Business Continuity Management
Manage information security Continuity and Redundancies
A.18: Compliance
Manage organization compliance with legal and contractual requirements
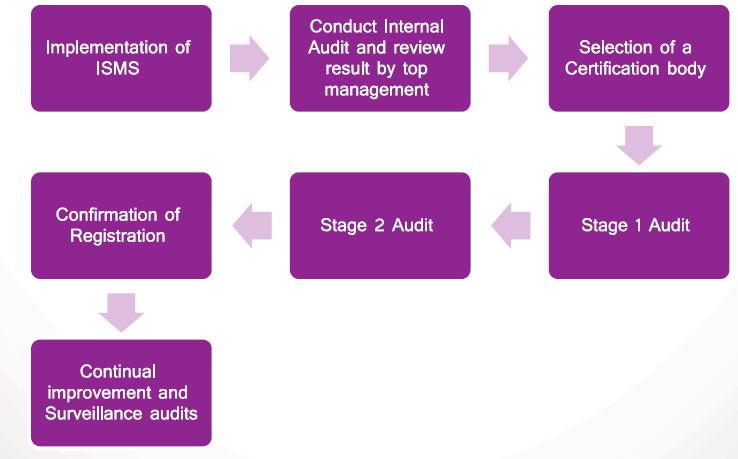
The ISO/IEC 27001:2013 Certification Process
There are Three Core Phases
Phase I : Before External Audit
1. Implementation of ISMS
Complete of implementation cycle of Information security management system ( ISMS) Including mandatory Requirements and optional Controls
2. Conduct Internal Audit and review result by top management
The organization conduct periodic internal audits to ensure the ISMS incorporates adequate controls which operate effectively and review it by Top Management
3. Selection of a Certification body
Organization select a Certification body “ BSI , DNV, SGS “ to conduct External audit activity and Certified Organization ISMS Program
Phase II : External Audit
4. Stage 1 Audit
Conducted off or on site to determine if your ISMS system has met the requirements of the standard and is capable of being audited.
5. Stage 2 Audit
Conduct on site to audit the effectiveness of the ISMS system. Stage 1 and Stage 2 must be completed to become ISMS certified.
Phase III : Following the audit
6. Confirmation of Registration
Lead Auditor recommend to Certification Manager of Certification Body that Organization are certified. The Certification Manager will review Organization file to ensure that the recommendation has been made in an impartial, fair and competent manner.
Upon completion of the above Organization will be officially certified to ISO/IEC 27001:2013 .
7. Continual improvement and Surveillance audits
Conduct Internal Audit Activity by Organization and Certification body auditor will conduct surveillance audit for organization every 6 months or 12 months for next three years after organization achieve ISO/IEC 27001:2013 Certification
Estimated Time needed for Implementation and Certification ISO/IEC 27001:2013
Based on my Experience
Phase I : Estimated time needed for Implementation ISO/IEC 27001:2013
Estimated Duration needed for Implementation depend on Organization size
“ Employees, Systems and Information “
• Small Organization : 50 – 150 Employee
Estimated time for Implementation of Standard from 6-8 Months
• Medium Organization : 150 – 400 Employee
Estimated time for Implementation of Standard from 10-12 Months
• Large Organization : 400 to 1000+ Employee
Estimated time for Implementation of Standard from 13-16 Months
Phase II : Estimated Time needed for Certification ISO/IEC 27001:2013
Case 1 : if there is one or more Minor Nonconformity and the organization try to Correct them accordingly the Certificate can be Issued around a Month
Case 2 : if there is one or more Major Nonconformity and the organization try to Correct them accordingly the Certificate can be Issued around 3-5 Months
Conclusion
ISO/IEC 27001:2013 gives Organization a Perfect Information Security management framework for implementing and maintaining security. In this Article, I tried to shed some light on new standard and its Mandatory Requirements, Optional Requirements , Structure , Benefits , Certification Process and Estimated time for Implementation and Certification.
References
• ISO/IEC 27001:2013 Information technology – Security techniques – Information security management systems – Requirements
• ISO/IEC 27002:2013 Information technology – Security techniques – Code of practice for information security controls
• The FDIS versions of ISO 27001 and ISO 27002
• http://www.pc-history.org/17799.htm
About The Author
Ahmed Riad, Middle East Business Continuity Leader