Journey to the wonders of ICS Security
Introduction
Industrial Control Systems play a vital role in our daily life. They control important aspects of different industries that cross our daily life in some way or another. Industrial Control Systems or ICSs control everything around you from small processes as in your car to nuclear reactors and aircraft systems. You can find ICSs in most utilities for example Oil & Gas, Smart Grid, Water treatment and so on.
Since we are security enthusiasts, when looking into these systems you can clearly see how vulnerable and fragile they could be. These systems are very obsolete and they were not secured by design so when they were connected to our IT network, they were massively attacked and torn down. And you can imagine how catastrophic it would be if someone attacked an ICS that controls prison security gates, electricity Smart Grid or even a nuclear reactor.
In the old days, ICS systems were isolated from the internet. ICS was just used to control a specific industrial process and there was no further needs. With the rapid growth of internet and IT technologies, it became necessary to connect ICS systems to IT networks for real time monitoring, analysis and even remote control. This lead to the exposure of these critical systems to vulnerabilities of IT networks. Now an attacker can attack an Oil & Gas company for example from outside. After gaining access to the internal network, he can pivot through the network till he reach a machine that controls a critical process like the flow of gas or petrol in a pipeline. Now he can switch off the flow causing severe financial loss to the company, and that’s the least he can do. He can also raise the flow causing a disruption or even an explosion that may lead to loss of lives.
It happened before
Attacks against ICS are not that new, targeted or even non targeted attacks caused or almost caused major effects in the past. I’ll mention the most notable ones from my point of view. You can search for more and I assure you will find disasters. Note that all incidents you’re going to find are only the ones disclosed to public. There are lots of other incidents that were not disclosed for national security matters or whatever.
The first incident that –in my opinion- changed the history of ICS security is the most advanced ICS malware ever created called Stuxnet hitting nuclear reactors in Iran and Russia and some other countries as well. In 2010 Stuxnet was a major topic in worldwide news after disruption of nuclear centrifuges in Iranian nuclear facility in Natanz. Stuxnet is twenty times complex computer virus that was only targeting motors of centrifuges in nuclear facilities and also pipelines. Stuxnet used four zero-day vulnerabilities in windows to propagate through networks and replicates itself into every single thumb drive that is connected to the infected system. Stuxnet was very targeting in such a way it will infect a system, look for specific software that is used to control Siemens PLCs, look into their control logic and search for any motors controlled by PLCs. If any motors found, it will monitor the frequency of the controlled motors, and only attacks if these motors spin between 807 Hz and 1210 Hz.
Stuxnet attacks these systems by changing their rotational speed causing an increase in pressure. Moreover, Stuxnet would hide the real values of the system parameters giving normal readings to human engineers and operators while playing around with the motors’ speeds. If Stuxnet didn’t find any software on the infected system it will remain dormant till this system either connect to another network or a thumb drive is connected to the infected machine. In both ways, it will replicate itself through the network or infected USB drives. And by the way, that’s how Iranian nuclear facilities were compromised although they were completely isolated from the internet.
The second incident was in October 2013 when Israeli Road Control System got hacked causing traffic jam in Haifa highway for more than 20 minutes. A malware infected security camera in the Carmel Tunnel toll road and was able to gain its control. The next day, it shut down the roadway again during morning rush hour. It remained shut for eight hours, causing massive congestion. Experts who investigated this accident said that this malware was not sophisticated enough to be the work of another government and it was more likely done by hacktivists.
There are a lot incidents related to targeting ICS systems and causing severe damages in some cases people actually died but I mentioned the above two incidents to demonstrate how computer viruses and series of ones and zeros could be weapons in cyberwarfare. And in cyberwarfare, which is better than ICS to attack when trying to harm your opponent’s infrastructure?!
What is ICS?
“Industrial Control System” is a general term that encompasses several types of control systems used in industrial production, for example Distributed Control Systems [DCS] and Supervisory Control And Data Acquisition [SCADA]. ICSs control different types of industrial processes such as electrical, chemical, water, oil and gas.
Distributed Control Systems [DCS]
DCS system controls industrial processes within the same geographic area such as a plant or a field. DCS can be dissected into two types of components. The first one is field devices spread across the plant to do the hard and dirty work and the second one is controlling devices located in the control room inside the plant or the field. In this control room human operators monitor the operation of the outside industrial process and issue commands according the readings coming from field devices. Note that all of this is happening on the same geographic area.
Supervisory Control and Data Acquisition [SCADA]
SCADA differs from DCS in such a way that there is a centralized system that monitors and controls entire sites or complexes of systems spread out over large area like countries or even continents.
SCADA can be divided into two parts
- Supervisory Control
- Responsible for automating the control process of running industrial processes with no human interaction by using Remote Terminal Units [RTUs], Intelligent Electronic Devices [IEDs], Programmable Logic Controllers [PLCs] or any other type of controllers
- Data Acquisition
Starts at the RTU/PLC level when analog signals coming from field devices are converted to digital signals and sent back to Human Machine Interfaces [HMI] so the human
- operator can monitor the readings of the running process and can make supervisory decisions to adjust or override normal RTU/PLC control.
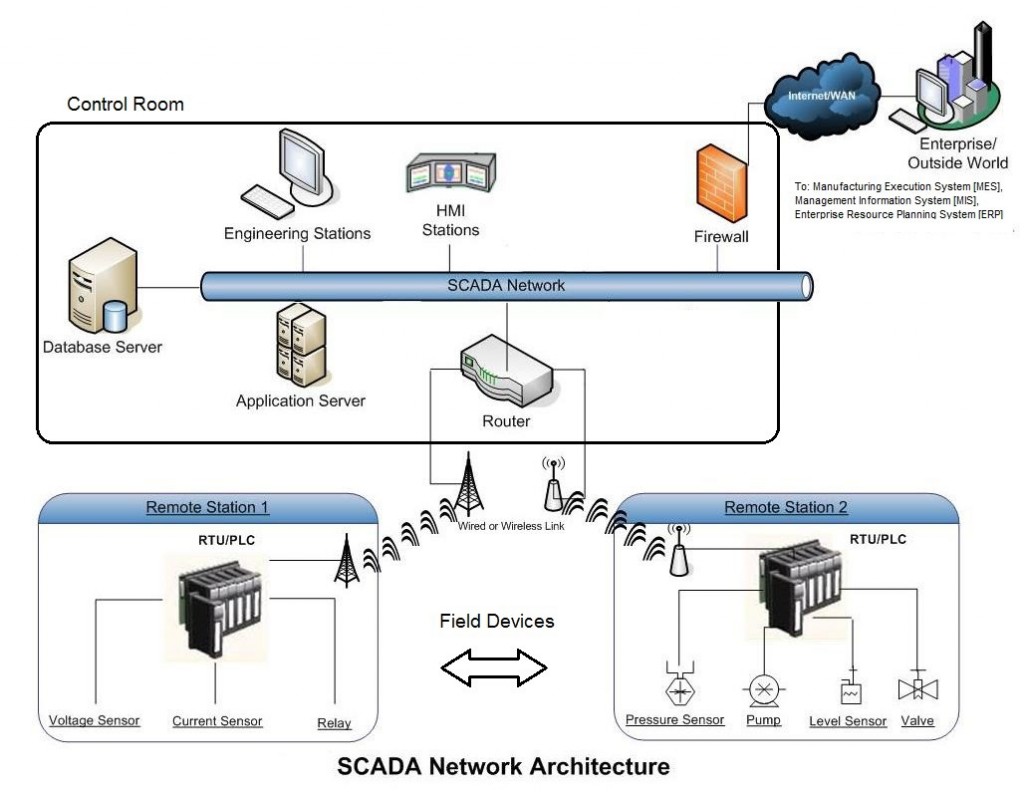
SCADA Architecture
SCADA systems are now the most widely used systems across the globe since it facilitates controlling of different remote sites from only one central location.
When dissecting SCADA components, they can be categorized according to their geographical position in two categories
- Field Components
- Control Center Components
We will be looking into each component explaining how it works and its role in SCADA architecture. We will focus on control center devices and the controllers in the field. We’ll also give a brief description about other field devices like sensors and motors.
Field Components
Field devices include those components who exist in the field and participate directly in the running industrial process. They can be categorized into three type according to their role:
- Information Gathering Devices
- Controllers
- Action Devices
Information Gathering Devices
These devices are responsible for gathering information about industrial process various parameters such as heat, pressure, flow, level and many others. These devices are called sensors. Sensors are widely used in any control system as they are considered the eyes and ears of every process controller.
Controllers
Controllers are considered as the mind of the ICS. Sensors gather information about the process pass it to controllers, controllers process this information and issue the right commands according to the logic they were programmed to. Then they pass these commands to action devices. The most common types of controllers are Programmable Logic Controllers [PLCs], Remote Terminal Unites [RTUs] and Intelligent Electronic Devices [IEDs].
PLCs / RTU
There is a significant difference between PLCs and RTUs. A while back, PLCs were used only to control the industrial process and RTUs were used as communication translator between components in field and control center. RTU is microprocessor controlled device that understands analog signals coming from field devices like sensors and convert it into digital signals and packets that control center devices can process. RTUs also receive digital inputs from control center components and translate it back to analog signals which can be processed by field devices. So mainly RTUs interface field devices to control center components.
Nowadays, PLCs took over the job of RTUs besides their main job automating the process control. PLCs become digital computer based controllers directly connected to both field devices and also control center devices. It handles the communication between control center and field devices in such a way where it sends the current values of different process parameters to control room devices. These values are fetched from sensors that are connected also to the PLC. PLC also send commands to action devices
Action Devices
Action devices are considered as the arms of the ICS. They are the ones who do the dirty work in the field. They receive commands from controllers and execute them. These devices could be a motor or a pump for example and the actions could be starting or stopping a motor, raising its rotational speed or switching a pump on or off.
Control Center Components
Control Center of any ICS system contains different types of components that assist human engineers and operators to monitor the running industrial process. Control Center could be connected to the IT network of the company to help upper layer managers take real time decisions like starting, holding or stopping the operation according to real time feeds they get from control center. These are the most common components you can find in a control center:
- HMI Servers
- Historians
- Controllers
- Engineering Station
Note that controllers could also be found in control centers not in the field, in some applications controllers are required to be near the human engineers.
HMI Servers
HMI servers or Human Machine Interfaces are responsible for visualizing the running process so human operators can observe the current values of different parameters of the running process and also issue commands to adjust theses parameters’ values through this interface. HMIs are connected to controllers to get the values of different industrial process parameters. It also can adjust these parameters by commands received from human operators or engineers. HMI is basically a software solution, each ICS vendor has their own version of HMI software. This software can be a desktop application that only can be accessed on a single machine or a web application based software that can be accessed both onsite and also remotely. This makes it easier for human operators to handle ICS processes anywhere even using their smartphones.
Historians
Historian servers are important for retaining the events that happens across the SCADA system. Events in SCADA system could be a motor start or stop, temperature rise or alarm that was set off because of a critical condition in the system. Historians basically collect data from various devices in SCADA network and log them to a database in real time. It also captures plant management information about production status, performance monitoring and quality assurance. Historian systems also offer the ability to view the data that has been logged normally in graph form, thus showing change in a specific value over time.
Engineering Station
Engineering Station is a computer used to update the control logic of PLCs and RTUs. It’s used by engineers to change what output should RTU or PLC give when a certain input happens. It’s also used for updating the firmware of PLCs, RTUs and IEDs. They are very similar to computers with IDE [Integrated Development Environment] software that developers use to develop different applications for example NetBeans or Visual Studio but in this case engineers are using another software to develop control logic on controllers. Each controller vendor has their software that is specially designed to develop control logic for their PLCs or RTUs.
How all of this are tied together?
SCADA components are connected together in two types of networks, the first network connects field devices and controllers and they all speak analog signals. The second one connects controllers or signal converters (RTUs) with HMI servers, Historians, Engineering stations and application servers. All of those speak in packets meaning that they all communicate through normal TCP/IP packets we used to see in normal IT networks like HTTP, SMTP, DNS and so on. The difference here is in OT networks, they speak different protocols for example Modbus, DNP3, IEC61870-5, EtherNet/IP, OCP and so many other protocols. Some of these protocols are open and some others are proprietary protocols limited only to products of one specific vendor.
we used to see in normal IT networks like HTTP, SMTP, DNS and so on. The difference here is in OT networks, they speak different protocols for example Modbus, DNP3, IEC61870-5, EtherNet/IP, OCP and so many other protocols. Some of these protocols are open and some others are proprietary protocols limited only to products of one specific vendor.
Conclusion
To really understand risks facing our critical infrastructure we should understand their architecture and how all of its components are connected together. I hope this article gave you a glimpse of what ISC systems look like and how they operate. The next step after understanding ICS architecture components and how they are tied together is deeply dissecting different industrial protocols and understanding how they work in real world scenarios and then study their vulnerabilities and weaknesses. I hope you liked this journey and wish seeing you next time in another article.
————————————
About The Author

Ahmed Fouda
Information Security Engineer at CONNECT-PS