Knowing Your Adversary – Implementing a Cyber Threat Intelligence Program
As far back as I could remember, there was always a need to have additional information for validation or confirmation that an incident, security event, investigation was complete or just when it came to plain old protecting the company from threats. No matter the industry, all companies doing business on the World Wide Web aka “Internet”, must have a program in place to receive and/or provide intelligence and other information, in order to achieve the big picture when it pertains to any threat, aka your adversaries. It is important to also remember that adversaries do not necessarily have to be external sources, because the number one threat to all companies is the insider, negligent or not.
COMPOSITION OF CYBER THREAT INTELLIGENCE PROGRAM
When it pertains to the design and structure of your cyber threat intelligence (CTI) program there will be known dependencies and contributors to think about and plan out. Not all CTI programs will be alike, although many might be similar or consistent due to industry working groups and collaborative arrangements between similar companies, e.g. big box retailers may have similar framework and structure because the 2 or 3 companies are working together to identify and benchmark cyber threats. Knowing what content will comprise your CTI program will come from the benefit of knowing your own organization and the possible sources of information that can be “fed” or “ingested” into your CTI program. Also to note that not all CTI programs have to be completely automated; there could be part manual and part automated or for the most part automated and a little manual.
So, when we discuss dependencies, what am I speaking about? Well, as I mentioned previously, knowing your environment and corporate landscape will be important when deciding what content or information you would like or think needs to be consumed as intelligence sources within your CTI program. Coupled with knowing your organization is the concept of access and visibility with stakeholders in your company environment, and the ability to influence where needed to gain support for your CTI program. After all, the intelligence information (and hopefully actionable at least) you receive and analyze will be purposeful to your internal business partners and stakeholders. The other aspect of dependencies is the availability of internal technology resources, which also includes log sources. A CTI program can work independently of or in concert with your SIEM technology as well.
The other primary consideration for your Cyber Threat Intelligence program are the contributors, or sources for your program. Contributors can be broken down into 4 categories (or more if needed):
- Internal Partners
- External Sources
- Technology and Monitoring
- Compliance and Risk
Lets examine some examples of each category so you get a better picture of what sources would fall where.
Internal Partners: These sources could include Loss Prevention, Business Intelligence, Corporate Security (Physical), Human Resources, Risk Management, Investor Relations.
External Sources: The sources in this category include industry working groups, industry information sharing groups and listservs, government agencies, other corporate partners, etc.
Technology and Monitoring: Sources such as your SIEM feeds, independent log sources from firewalls, Intrusion Detection (IDS), anti-malware, etc., proactive monitoring and investigation initiatives and other associated data.
Compliance and Risk: Your various groups within InfoSec including risk, compliance, governance and associated groups.
BUILDING YOUR FRAMEWORK
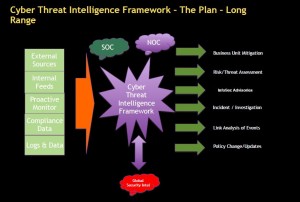
When building any program or initiative its important to build a “framework” of how your program will work/operate at a high level. You could add granularity where needed or made sense. The graphic above depicts a sample framework that I have utilized and planned at numerous companies (where I worked) and/or companies I consulted with. There are a couple of key decisions that can be made at this point in the game:
How automated will the program be? In some instances, companies maintain different components in their program. As an example, the company may subscribe to threat feeds that they ingest into their SIEM environment. If a company utilizes a fully managed service aka Managed Security Solutions Provider (MSSP), then most of those ingest their own threat feeds and/or other external feeds as well.
To SIEM or not to SIEM? So in the above example, external threat feeds can be ingested into your SIEM solution and then correlated with your existing log data. Some companies choose to utilize a “threat correlator solution” that acts as the overall CTI SIEM and all data (sources, contributors) flows into threat correlator. A contributor of this data would be some or all of your SIEM logs.
Outcome of all the threat data: Based on your needs or wants, your CTI analysts can be producing various end products including risk and threat assessments, Information Security Advisories that contain actionable intelligence, critical vulnerability alerts, identify issues within the organization that require additional investigation or research, link analysis between various events that could identify patterns or trends in your organization and there could be instances where security gaps are identified which require policy change in the environment.
IDENTIFYING YOUR ADVERSARIES
Most companies I know or I have worked with, they want to know or have a good idea of who the threats are and where they are originating from. The combination of your CTI actions coupled with monitoring of your network will weed out the “small stones hitting the glass window” and raise to the surface your real threats, both inside and outside. This is where the cooperation between your CTI team and Security Operations team comes into play, through monitoring activities to identify normal and abnormal traffic and activity on your network.
The Insider threat can include what I like to call, “negligent insiders” and/or the insiders that are purposeful and know exactly what they are doing, either recruited by third parties or working alone. In instances where there may be heightened events like discharges, layoffs and reduction in force events, partnering with your HR teams will be beneficial in identifying potential threats before they become serious issues. The other type of insider that tends to be an issue are the “sympathizers” to outside groups like animal or environmental activist groups. These types of people need to be closely monitored in order to prevent issues from trending.
External threats can be wide and far ranging, everything from an activist organization with a cyber arm to it, extremist organizations, sympathizer organizations, nation states, terrorism groups, cyber hacker organizations, cyber espionage teams, organized criminal gangs and the list goes on. Those “small stones hitting the glass” threats are typically kids aged 13-17, who may have some great computer skills but bored at home with nothing to do and through the use of online “crime-as-a-service” offerings end up sending large numbers of packets your way in the form of a Syn Flood or sometimes, larger Distributed Denial of Service (DDOS) attack.
BENEFITS AND ADVANTAGES
For all purposes, creating, building and implementing a cyber threat intelligence program can be extremely beneficial for any organization, because you will likely stay “ahead of the curve” or in this case your adversaries or threats. Your ability to not only gather technical indicators of compromise (IOC), indicators of attack (IOA) and additional information, your CTI team can start to build intelligence and information related to the cyber threat actors and groups behind the various tactics, tools and procedures (TTP’s) identified through your program. This is where “knowing your adversary” is very important. If you know who or what is targeting your company, or executives or systems, then you will have a better chance of preventing and mitigating issues (security events) before they can transform quickly into critical issues (security incidents) that can lead to far worse things like compromises, system breach, denial or services and/or degradation of resources. Better yet, protecting your company’s name, reputation, brand and revenue is important as well.
Additional advantages of your cyber threat intelligence program can be created between your security department and your internal customers (stakeholders, business units, etc.) As an example, if you were to produce a weekly or daily threat intelligence report and distribute to your internal partners and try and make the content as relevant to your company as possible, these reports could open the door for internal customers requesting assistance in the form of a risk assessment for a new service they might be offering. These types of reports when distributed the right people, there could be situations where additional internal partners will be identified that request to be included in these reports. This opens up visibility to you and heightens your exposure in the company environment. The more people know about you the better.
When it comes down to implementing your program there is nothing wrong in taking steps. As an example, you may start out with threat feeds ingested by your SIEM and an analyst working to create reports and advisories through monitoring and proactive investigations. Then there are cases, where some industries are far more likely to have consistent cyber threat targeting like energy, government and entertainment companies, so in these cases a more robust program needs to be implemented quicker. Every company or organization will be different when it comes down to implementing your program.
In situations where your executives are less interested in a CTI program or they believe it is not necessary, it will be important for you, the security executive or manager to conduct a risk / threat profile exercise, either on your own or hiring a contractor to build a profile on what your risks and threats are facing your company. If you address these concerns with your executives in this manner and can tie other examples of brand failure, or legal actions or other negative affects caused by the threat groups, your company executives are likely to change their minds very quickly. Outside all of this, any introduction of “actionable” intelligence that you can provide regarding a pending threat to the company or systems (zero-day vulnerability that could open your company up to hackers), most executives can see the bigger picture and will approve some spending in some level of a cyber threat intelligence program. It might just be the matter of “crawl, walk, run…..”
About The Author
Harris D. Schwartz, Cyber Security Expert.