Stuxnet PART1 : The PERFECT CRIME
Summary
Recently there has been a new computer worm that has gained lots of attention from the computer security community, the energy sector, the media and even the general public. It’s the “Stuxnet” worm.
The reason for this unsurprising attention is because “Stuxnet” is one of the most complex computer threats the world has ever seen. I decided to write two articles about the worm, the article that you are currently reading will be the first and shall act as an introduction to the Stuxnet worm, its motives, the attack vectors and the motives behind it, the second article shall go under the hood and take a closer look at the technical aspects of the worm and the SCADA systems targeted.
1 – Introduction
Stuxnet is a computer worm that was written to target Programmable Logic Controllers (PLCs). PLCs are a part of a bigger automation environment called SCADA (supervisory control and data acquisition) systems; SCADA systems are special computer programs used to run mega infrastructure projects, like gas pipelines, electricity grids, nuclear facilities and power plants.
Stuxnet was carefully written to “access, and in some cases reprogram” those PLCs by modifying certain pieces of the code stored on them. The purpose of this “reprogramming” is to make those PLCs work in a manner the attacker is tended and to hide those changes from the operator of the equipment.
In other words, the Stuxnet creators wanted to plant something, hide it well and then have the option to control, eavesdrop or cause damage from a remote location In order to achieve this multipurpose goal; the worm creators used a record number of different com ponents to increase their chances of success.
This includes but not limited to:
● zero-day exploits
(A total of four un-patched Windows holes to facilitate the worm entry, Initial infections were probably caused by USB)
● A Windows root kit
(A collection of malicious programs designed for windows operating systems – like a Swiss army knife this includes an array of tools and can do many things)
● The first ever SCADA/PLC root kit
(A collection of malicious programs designed for control systems – like a Swiss army knife this includes an array of tools and can do many things)
● Antivirus evasion techniques
(Special techniques to trick the Antivirus into believing that nothing is wrong)
● Complex process injection and hooking code
(Injects itself into certain parts of the SCADA software, allowing it to execute with a high privilege)
● Network infection routines
(Uses the infected LAN network to replicate and multiply)
● peer-to-peer updates
(Can be updated remotely)
● Fake driver signed certificates
(Used a signed yet expired “Realtek semiconductors .inc” signed hardware driver certificate to trick windows into inherently trusting the malware)
● And a command and control interface.
(Can be controlled remotely)
Stuxnet creators were very professional in hiding their tracks, that it’s nearly impossible with the current information we have to know who wrote it. The source code of Stuxnet is full of references that have caused researchers to point fingers towards Israel, being currently engaged in a political dispute with Iran regarding its nuclear program.
One of the most notable references is the word “Myrtus,” which the name of a specific Stuxnet file, according to the New York Times, linguists and Biblical scholars also highlighted that the term’s usage could refer to the Book of Esther in the Bible’s Old Testament.
In the Book of Esther, Jewish forces — after unraveling a Persian attack plan — stage a preemptive and successful assault against their adversaries. (Source New York Times 30/9/2010)
Another reference Buried in Stuxnet’s code is a marker with the digits “19790509” that the researchers believe is a “do-not infect” indicator. If the marker is found on a PC this means it’s already touched/ infected or exempted and the worm will stop in its track.
The researchers — Nicolas Falliere, Liam O Murchu and Eric Chen — speculated that the marker represents a date: May 9, 1979.
“While on May 9, 1979, a variety of historical events occurred, according to Wikipedia “Habib Elghanian was executed by a firing squad in Tehran sending shock waves through the closely knit Iranian Jewish community,” the researchers wrote. (Source Computer World 30/9/2010) But again this can only be misleading information placed on purpose.
If the perfect crime is a crime that gets the perpetrators what they want without leaving a serious trace, then indeed Stuxnet is the perfect crime.
2- First Discovery
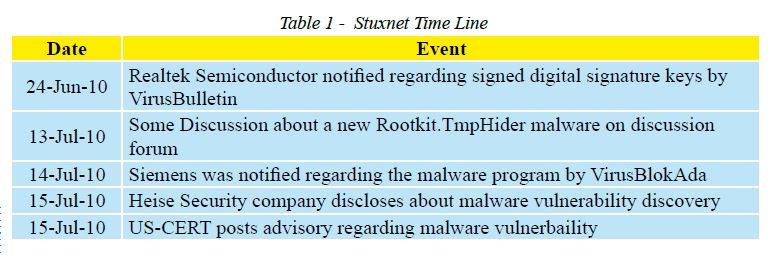
Stuxnet was first announced in June 2010, although recent reports prove that it was already infecting systems since mid 2009. This period between the first infection and the announcement of discovery is probably due to the fact that the majority of infections were in Iran. And that the creators of the worm were not seeking fame or media credit. They had a fixed target.
The following table shall make it easier to follow the sequence of events.
3 -The Target
It’s now evident that Stuxnet is targeting only industrial control systems, especially the ones in Iran. The ultimate goal of Stuxnet is espionage and sabotage the critical infrastructures (Like gas plants, refineries, nuclear facilities…etc) that use this special Industrial Control Systems Software.
The espionage is by checking for very specific variables on the infected host, those carefully selected variables can easily give away a lot of information about the type of operations taking place in the targeted facility.
The damage can be easily achieved by remotely instructing the worm to “reprogram” certain variables that can make the facility over heat for example.
4 -How does it spread?
The Stuxnet malware was initially spread via USB key. It may also be propagated via network shares from other infected computers sharing the same local network (LAN). As noted above, Stuxnet uses a specially crafted Windows shortcut placed on USB drives to automatically execute malware as soon as the .lnk file is read by the operating system. Disabling the auto-run
feature is useless against this attack.
In other words, simply browsing a USB drive using an application that displays shortcut icons (like Windows Explorer) runs the malware without any additional user interaction. Once the computer is infected, it will attempt to infect any other USB drive inserted into it.
It is likely that any USB drive inserted in a machine will be viewed using some sort of file explorer, thus the chance of infection is very high.
5- Infection Rates
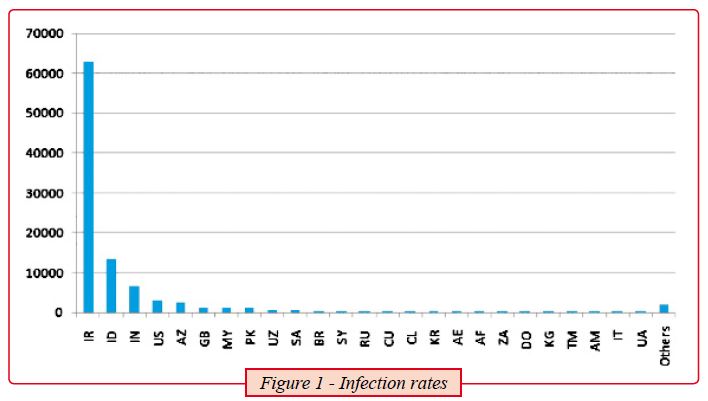
According to a recently published report[2] from security firm “Symantec”, the infected hosts have reached nearly 100,000. It’s very alarming that such a high number of infections can take place on “supposedly” some of the world’s most mature organizations, due to their critical nature of business. Apparently this “false security” is not limited to Iran only but to 155 countries.
This data was gathered through Symantec’s monitoring systems that tracked the infected hosts’ traffic going back to the Command and Control systems (two C&C systems were tracked and shut down, one in Germany and the other in Malaysia)
The data between the infected machines and the command and control centres is encrypted and includes data such as: the internal and external IP address of the infected system, the computer name, the windows version and most importantly if this network has the Siemens SIMATIC step 7 industrial control software or not.
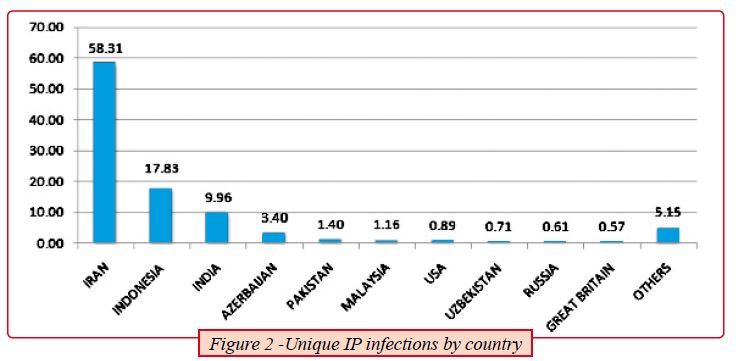
Figure 2, shows that out of the 100,000 infected hosts, Symantec was able to observe more than 40,000 infected hosts with unique external IP addresses from over 155 countries. 60% of those machines are in Iran.
,/br>
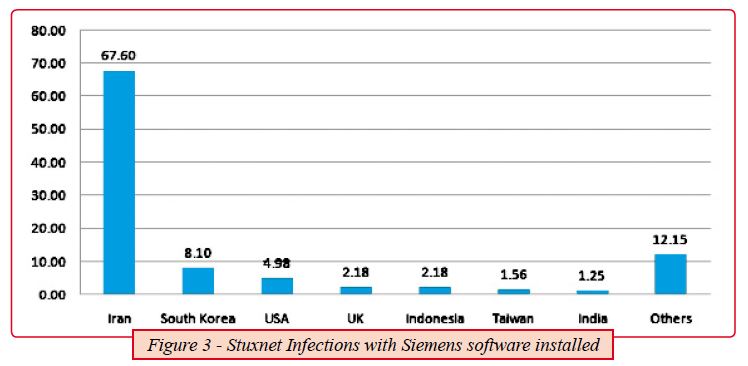
Figure 3, shows the percentage of the infected hosts with Siemens step 7 software installed, this shall give out a note on how precise this worm is.
The noticeable high number of infections in Iran is probably due to the fact that this country was the main target of the attack; the additional infections are likely just side effects or collateral damage due to the fact that most of those companies dealing in the energy sector exchange resources and consultants, deal with the same vendors and engage in similar business activities.
6- Conclusions
Stuxnet is worthy of studying because for the first time in malicious code history – it is the first to exploit not one but four 0-day vulnerabilities, compromise two digital certificates, and inject code into industrial control systems and hide the code from the operator and from all the expensive antivirus programs.
Stuxnet is so complex that very few people around the world can come up with such malicious code. This piece of malware requires extensive knowledge in multiple areas of computers and control systems in general and Siemens PLCs in particular. This array of expertise can only come together very seldom.
A worm that diverse and sophisticated requires a team of 5-6 people working full time for 6 month, with access to a SCADA system and deep knowledge of Siemens SIMATIC software and the target system architecture.
In fact security experts believe that a complex attack like Stuxnet can only be a government sponsored attack. If we can get away from Stuxnet with just one lesson it’s the fact that direct and specially crafted attacks against critical infrastructures are unfortunately, Real.
The damage that those few lines of code can incur in the real world is like nothing we have seen in the history of computers. A typical worm can steal your credit card information or your personal email password. But worms like Stuxnet can put critical infrastructures like a nuclear facility for instance under a threat that can deprive wide areas of land from any form of life for hundreds of years.
This worm should question our conception that malicious programs can at best cause serious financial loss or personal information leakage, but never a human life.
On a regional note, Stuxnet should be very alarming to decision makers in our countries.This worm targets one of the main driver of our economy and that’s the energy sector. By being designed to attack SCADA systems which are responsible for running all of the natural gas and oil plants in the world. This worm is capable
of causing a real damage to the economy, public safety and the environment.
I really appreciated the conclusion from a Symantec expert commenting on the situation “Stuxnet is the type of threat we hope to never see again”.
7- Recommendations
Seeing the amount of sophistication demonstrated by this worm, it’s now imperative that decision and policy makers should start reviewing their national security threats and risks.
The recommendations that can help nations achieve the goal of securing their infrastructure against the digital threats can be summarised as the following:
● Determining the Critical Infrastructure, by using a risk based methodology. Governments should have a clear view on what is critical and what is not. And prioritize the action plan accordingly
● Assisting owners & operators of Critical Infrastructures (both Government and private sectors) to address their information risk, being accountable for their own assets and by setting an information security baseline that public and private critical infrastructure companies comply with
● Testing and measuring Critical Infrastructure Information Protection (CIIP) maturity over time and updating the strategy based on the measurements
About The Author
Omar Sherin, Mr. Omar Sherin is the head of critical information infrastructure protection (CIIP) at Qatar Computer Emergency Response Team (Q-CERT), an ictQATAR initiative. In this role he participates in technically assessing critical infrastructure, drafting guidelines such as the Qatari National ICS Security Standard, and conducting Qatar’s national cybersecurity drills. He is also an international partner of the Industrial Control Systems Joint Working Group (ICSJWC) and a certified business continuity professional, certified ethical hacker, and ISO 27001 lead auditor. He has more than 11 years of professional experience in information security and resiliency, and has worked for several multinational firms in the oil and gas sector.