Successful Story with Twitter Bug Bounty Program in 2014
At beginning of September 2014, just like other social networks, Twitter started their bug bounty program for paying security researchers monetary rewards with minimum reward of 140$.
That made many white hat hackers including me start looking for security issues and vulnerabilities in twitter and I’ve successfully found a serious vulnerability in twitter that could incur and cause big financial losses for Twitter so let me share the story with you.
The story started when I was checking the twitter business site “ads.twitter. com” which allow people to advertise on Twitter and promoting their Tweets. When you start an ad campaign you should put your payment card details to the account. So i started an ad campaign and i added my own credit card, then I noticed a link to a page called “Payment methods”.
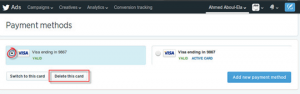
This page gives you the ability to add a new credit card or delete an existing one.
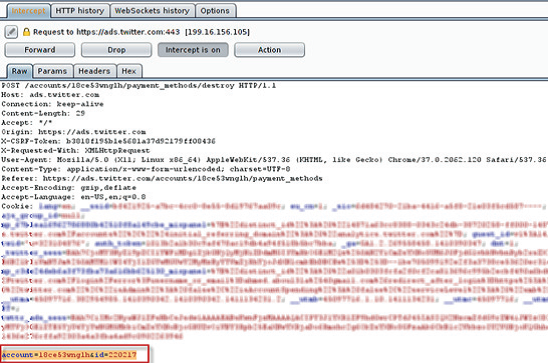
I tried to delete my existing credit card while intercepting the http request sent using burp suite Proxy, i found there is only two POST parameters sent in the request such as “account=18ce53wnglh&id=220217” .
Account: is my twitter account id
Id: is the credit card identifier stored in twitter’s database.
What goes in my mind immediately is to check if this request is vulnerable to logical attack, i tried to change the account and id parameters to my other twitter account and replied again the request. Suddenly i found that my credit card was deleted from the other twitter account without any required interaction. This is obviously insecure direct object reference vulnerability.
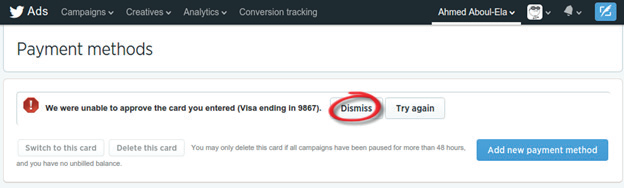
I have found also another similar vulnerability but this time the impact was higher and easier to exploit than the previous one . i tried to add an invalid credit card to my account , then it displayed an error message “we were unable to approve the card you entered” and showed a button called “Dismiss” .
When i pressed on the Dismiss button i found the credit card was disappeared from the account, so i thought it have same effect of deleting credit card.
I added again invalid credit card while intercepting the http request, i found that it only use the credit card identifier in the request without the account id parameter . i changed that credit card id to another credit card id added to my other twitter account and guess what ? The credit card was also deleted from my other twitter account.
The credit card id consists only of 6 numbers without any alphabetic characters so Imagine a black hat hacker who could write a simple programming code and use for loop on 6 numbers he could delete all credit cards from all Twitter accounts which will result in halting all the Twitter’s ads campaigns and incur big financial losses for Twitter .
I reported the two vulnerabilities to twitter security team and they have fixed it within 2 days and they paid me the highest reward in Twitter bug bounty program at that time.
About The Author
Ahmed Aboul Ela, Cyber Security Analyst at EG-CERT