Digital Investigation Concepts Part1
Abstract
In this article, a process model for Digital Forensics Investigation is developed and suggested as an alternative way to start digital investigations. The proposed model introduces the notion of a digital crime scene with its own digital evidence to be applied to law enforcement.
This article is structured as follows: Firstly, Providing background about Cyber-Crime
definitions and categories. Secondly, presenting a new model for the relation between digital forensics attributes and showing its significance to start solid investigation. Finally, provides scenarios in order to demonstrate the effectiveness of the model when applied on the investigations in reality. i.e. memory investigation, live investigation, hacking investigation, virtualization, cloud computing investigation process and network investigation.
Cyber-crime Background
The intense increase in cyber-crime is due to the innovative ideas that criminals have with regard to new types of cyber-crime and
new ways to commit these crimes. Criminals exploit human and technologies vulnerability to commit crimes in a way that makes it very hard to trace them back. The ever-changing nature of technology from virtualization to encryption …etc. contributes to the problems encountered by experts when collecting and preparing digital evidence for courtroom presentation.
Cyber Crime Definition
There are many definitions for cyber-crimes but the most common one is “Offences that are committed against individuals or groups of individuals with a criminal motive to intentionally harm the reputation of the victim or cause physical or mental harm to the victim directly or indirectly, using modern computing devices and telecommunication networks”.
Cyber Crime Categories
1-The computer as a target: The attacker seeks to deny the legitimate users or owners of the system access to their data or computers. A Denial-of-Service (a.k.a., DOS or DDOS) attack or a virus that renders the computer inoperable would be examples of this category.
2-The computer as a tool of the crime: The computer is used to gain some other criminal objective. For example, a thief may use a computer to steal personal information.
3- The computer as incidental to a crime: The computer is not the primary instrument of the crime; it simply facilitates it. Money laundering and the trading of child pornography would be examples of this category.
4- Crimes associated with the prevalence of computers: This includes crimes against the computer industry, such as intellectual property theft and software piracy.
What is Digital Forensics?
Digital forensics is defined as “The application of computer science and investigative procedures for a legal purpose involving the analysis of digital evidence after proper search authority, chain of custody, validation with mathematics, and use of validated tools, repeatability, reporting, and proper expert witness presentation” When considering this definition of digital forensics, investigators must apply the following two tests for evidences in both digital and physical forensics to survive in a court of law:
• Authenticity: Where the evidence originated?
• Reliability: How the evidence was handled?
Rules of Digital Forensics
An expert forensic investigator will do two things: make sure to preserve as much of this data in its original form, and to try to re-construct the events that occurred during a criminal act to know what happened. Because digital evidence is very volatile and can easily be contaminated or compromised when handled incorrectly, forensic investigation efforts can involve many (or all) of the following steps
• Making full (or mirror) copies of digital information from impounded sources for simulation and analysis purposes.
• Ensuring that the correct chain of custody is kept for the evidence to protect evidence against tampering.
• Being committed to evidence contradicts as known facts.
• Documenting any changes in evidence.
Digital Evidences
This article will consider digital evidence as ‘any data stored or transmitted in digital form that can help investigators to establish a link between a crime and its victim or its perpetrator’ by answering the five W’s questions in digital forensics process. Who, What, When, Where, Why.
Who controlled the evidence? What was used to collect it? Why was it done in that manner? When was each piece of evidence found? Where was the evidence found?
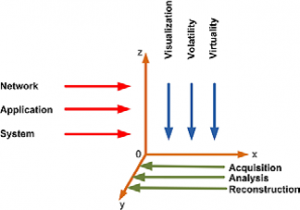
The main contribution of this article is to study the factors that influence the relation between evidence characteristics
(Visualization, Volatility and Virtuality) and the location (Network, Application, or System). Regulated by the factor of Evidence-Handling (Acquisition, Analysis
Digital evidence may be found in many layers
and many statuses as shown in figure 1
Axis Y: Defines the phases that all digital evidences should go through to deliver consistent and admissible report
• Acquisition.
• Analysis.
• Reconstruction.
Acquisition: involves the evidence search, evidence recognition, evidence collection and documentation
Analysis: determines evidence’s significance and probative value to the case by looking at its visibility and explaining its origin.
Reconstruction: involves organizing the results from the analysis done and using them to develop a theory for the incident drawing conclusions about what happened.
Axis Z: defines the Place (Where the digital evidence exists?)
Evidence can be found in the System, Application, or Network, but regardless of the location of evidences they all should go through the steps of acquisition, analysis, and reconstruction to reach the answer of the 5Ws (Who, What, When, Where, Why) but to decide start-point and path of investigation which are influenced by the factors of the third axis.
Axis X: defines the challenges exits with our digital evidence:
• Volatility
• Visualization
• Virtuality
Volatility: “Is the digital evidences persistent or not?”
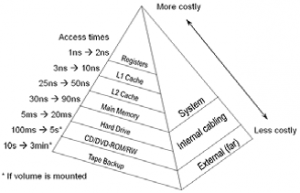
The following figure shows the relation between the ‘RAM’ with reference to ‘Time in Nano Second’. Which means the content of memory could be changed within a Nano second. High level of volatility means more chances of possible failure to produce relevant, enough and admissible evidence which leads failed investigations.
Visualization: “How is the data physically viewed? i.e. (encrypted or plaintext state)”
The physical appearance of evidence is a main factor that influences the investigation. Encryption for instance is creating challenges for forensic examiners, potentially preventing them from recovering any digital evidence, the influence of encryption challenge over the three possible evidence locations as
follows:
• System forensics: The integration of strong encryption into operating systems “File-system level encryption” prevents investigators to access to any data on the computer.
• Application forensics, logs will always play a key role in any evidence-based investigation, as they help to preserve evidence and shorten investigation times encrypted application logs will prevent investigators to extract and analyze them.
• Network forensic, Attack could be tunneled through non-standard protocols and encrypted traffic cannot be analyzed or traced by investigators
Virtuality: “Is it virtualized environment ?”
Today virtual environment can be created by software and hardware, in virtual forensics, the lack of physical access to recourses constitutes a disruptive challenge for investigators.
“Cloud Computing”. Is an obvious instance to show challenges investigators can encounter in virtual environment. Cloud Computing
is a model for enabling convenient, ondemand network access to a shared pool of computing resources (e.g., networks, servers, storage, applications and services).
The virtual instances for Cloud environment, where i.e. data is stored or processes are handled virtually provide a complex issue
to conduct valid forensic investigation, and due to the decentralized nature of data processing in the Cloud, traditional
approaches to evidence collection and recovery can fail the investigation.
After identifying the notional foundations and factors influencing digital forensics findings and paths.
The next part of this article discusses the practical process to investigate Cyber Crimes.
About The Author
Mounir Kamal
(Section Manager – Incident Handling and Digital Forensics),
CISA, Crangie Mellon CERT/CC Certified Incident Handler, CEH, CHFI, CREA